Archive for KnowledgeBase
Posted by Siren on August 31, 2016
In pursuit of effective ways to serve malicious software to Windows computers, cybercrooks often bank on different types of social engineering. In one of the recent hoaxes, the criminals have been sending emails with rogue subpoenas allegedly on behalf of the Australian Federal Police. This scam, obviously, targets Australians and tries to infect their machines […]
Read more →
Posted by Siren on August 23, 2016
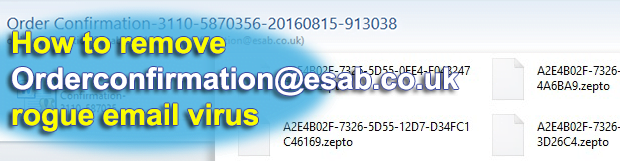
Security analysts have been noting a considerable volume of malware-tainted spam sent out from orderconfirmation@esab.co.uk. The emails titled “Order Confirmation-[random number string]” are disguised as if they were hailing from ESAB, a well-known manufacturer of industrial equipment. That’s not true, though. The menacing part of this phish is all about the .docm attachment that installs […]
Read more →
Posted by Siren on August 20, 2016
In the ongoing battle with crypto ransomware, the security industry is still lagging behind. What experts are mostly trying to do is revert the damage after the attack rather than prevent the predicament. In the case of the so-called Nemucod family of ransom Trojans, the contamination is usually beyond the reach of conventional antimalware. Delivered […]
Read more →
Posted by Siren on August 15, 2016
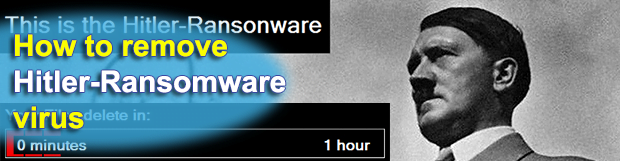
Although the Windows infection dubbed the Hitler-Ransomware isn’t currently in active real-world rotation, a couple of its characteristics are quite disturbing and make the sample a more hazardous threat than the commonplace ransom Trojans. The malicious specimen that researchers were able to spot and analyze appears to be buggy. It causes the compromised OS to […]
Read more →
Posted by Siren on August 10, 2016
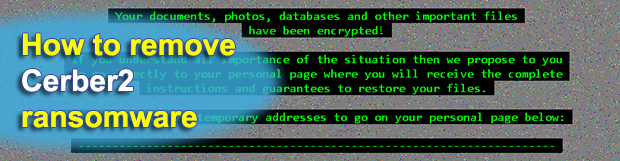
There is a bevy of details and ties that can be deduced from just the name of the latest crypto infection dubbed “Cerber2”. The symptoms of an assault by this new ransomware threat include a muddle of encrypted, hence inaccessible .cerber2 files spawned across the infected computer, as well as scary warning messages that ask […]
Read more →
Posted by Siren on August 7, 2016
If someone anticipates a pleasurable online experience with the startgo123 service, it’s not that way in fact. This is one of the myriads of homepage and search hijackers floating around the worldwide web. First off, it’s malicious because people never really opt into using it – instead, their web browsers get literally invaded by this […]
Read more →
Posted by Siren on August 7, 2016
Searchboro.com and the underlying browser extension demonstrate the worst practices of browser hijacking. Windows users infected with this adware strain experience an abrupt interference with their custom online settings. Most of the time, it simply takes some attentiveness to avoid this sample as it propagates via software bundles where the default installation already includes the […]
Read more →
Posted by Siren on August 6, 2016
It doesn’t take a genius to grasp the business model behind hijackers like Youndoo.com. These PUAs (potentially unwanted applications) take control of their victims’ web browsers in order to ensure that certain portions of web traffic are being continuously obtained from all the infected Windows computers. There are tons of interested parties whose wet dream […]
Read more →
Posted by Siren on August 6, 2016
The fact that the Nuesearch browser adware is served to computers through a technically legitimate scheme is a lame excuse for its unscrupulous distributors. By incorporating its loader into the setup clients for third-party solutions where this inclusion is deliberately blurred, the ne’er-do-wells spread their hijacker to PCs whose owners have no idea that the […]
Read more →
Posted by Siren on August 3, 2016
Not every computer application that’s bundled with other software is malicious. For instance, millions of Windows users are regularly encountering Adobe Flash Player updates, where third-party products are included in the default installation routine. There is an offending facet of such packaging, though. Trotux is a potentially unwanted browser extension distributed along with some freeware […]
Read more →
Page 21 of 36 «...101920212223...»