Archive for KnowledgeBase
Posted by Siren on November 22, 2016
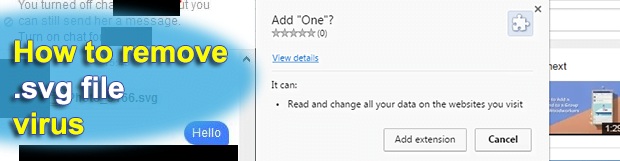
SVG stands for “Scalable Vector Graphics”, which is a fairly popular XML-based image format that allows for extensive animation effects. One of the main pros of .svg extension files for graphics designers is that these objects can be handled via commonplace text editors, just like XML text files. The virtues being obvious, cybercriminals have come […]
Read more →
Posted by Siren on November 21, 2016
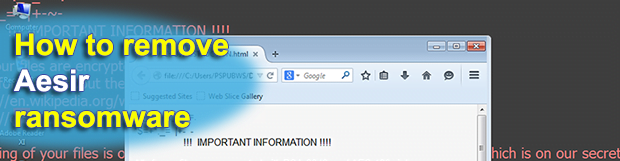
A new variant of the Locky ransomware appears to be in rotation right now. As opposed to its precursor dubbed Thor, this spinoff appends the .aesir extension to one’s encrypted files. Furthermore, the infection creates an updated set of ransom notes named “([random_number])-INSTRUCTION.html” and ““([random_number])-INSTRUCTION.bmp” to provide victims with a data decryption walkthrough. The threat […]
Read more →
Posted by Siren on November 11, 2016
There is an uptick in the volume of phishing emails allegedly sent on behalf of Apple’s iTunes Store. The threat actors attempt to wheedle personally identifiable information out of recipients by urging them to click on an embedded rogue link. The persuasion effect is attained through a notification about a nonexistent order that the user […]
Read more →
Posted by Siren on November 3, 2016
Popular applications have always been cybercriminals’ favorite targets. The fact that a huge number of people worldwide opt for using Skype as their online communication medium couldn’t possibly stay beyond threat actors’ focus. There have been numerous incidents in the past where Skype accounts got spammed with rogue links, and this trend is on the […]
Read more →
Posted by Siren on October 27, 2016
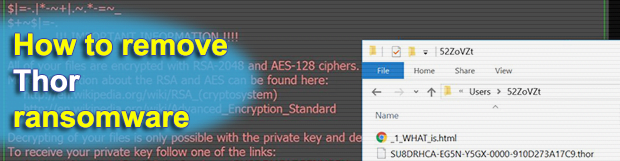
Thor is the latest persona of the infamous Locky ransomware. This variant was released less than a day after the previous .shit extension edition was discovered, which might suggest that the latter was a misunderstanding in the cybercriminal ring responsible for this lineage. The updated pest doesn’t have many adjustments inside. It appends .thor to […]
Read more →
Posted by Siren on October 20, 2016
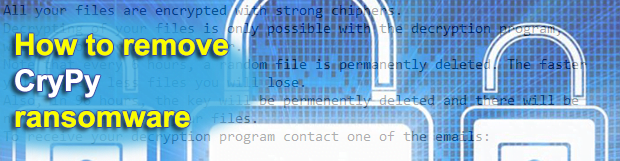
Python-based ransomware is not a new phenomenon in the online extortion environment, but it hadn’t been nearly as well-orchestrated as it has become with the emergence of the CryPy baddie. This crypto threat is proficient at evading antiviruses and leverages an extraordinarily hard-to-tackle encryption principle. The main hurdle to handling these attacks is that the […]
Read more →
Posted by Siren on October 15, 2016
Customizing web browser settings is as easy as ABC – all that needs to be done is go to the configuration pane and type the preferred values for homepage, new tab and default search. It may even be possible to pick the most popular service providers from a readily available list. This whole built-in convenience, […]
Read more →
Posted by Siren on October 14, 2016
Ransomware takedowns are still the exceptions rather than the rule, but they do occur once in a while. The WildFire Locker campaign, for instance, discontinued about a month ago due to a well-orchestrated operation by law enforcement and private sector security organizations. While this initiative was undoubtedly a success, the same group of cybercrooks recently […]
Read more →
Posted by Siren on October 5, 2016
There are no extraordinary tweaks made to the prolific Cerber Ransomware in the course of the fresh update. It still leverages the same strong cryptosystem to lock a victim’s files. As before, it changes the desktop wallpaper to a grayish image with random pixels and some warning text in green font. The circulation peculiarities are […]
Read more →
Posted by Siren on September 27, 2016
It takes a great deal of security awareness and caution to prevent the average ransomware attack from getting through, but it’s much more difficult to counter such a compromise after it actually took place. When the .odin file virus hits a Windows computer, the risk mitigation task is twice as tough. It locates and encrypts […]
Read more →
Page 19 of 36 «...101718192021...»