Archive for KnowledgeBase
Posted by Siren on July 28, 2016
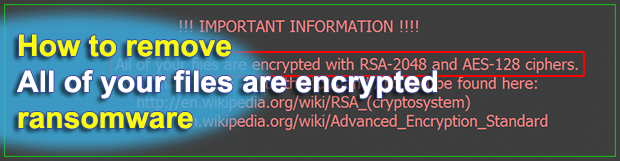
Amongst a bevy of attributes exhibited by every sample of data-encrypting ransomware, the structure and text of warning messages are like fingerprints. Some of these infections try to intimidate people through blatant misinformation and exaggeration, for instance, stating that one’s files are locked with a stronger cryptosystem than it actually is. In the case of […]
Read more →
Posted by Siren on July 23, 2016
Cyber ransoms and real-world ones are hardly any different from each other. In either scenario, there is an object or set of objects stolen or made inaccessible. Then, the criminals suggest some type of correspondence to interact with the victim and communicate their demands. Computer crooks usually stick with ransom notes in several different formats, […]
Read more →
Posted by Siren on July 23, 2016
There is a malvertising scam floating around the Internet in pursuit of forcing the downloads of malicious or junk software. The cybercrooks’ scheme is very intricate as it causes Windows issues that appear realistic. The idea is to leverage a piece of malware to wreak havoc with target systems’ graphics and then recommend the victim […]
Read more →
Posted by Siren on July 20, 2016
Technically, the application called KNCTR is supposed to be Itibiti Ventures Inc useful contrivance that allows anyone who installs it to make free telephone calls to the United States and Canada, enjoy continually updated multimedia content, and integrate their social media accounts into a single pane. Although this seems like an incongruous mix, the oddity […]
Read more →
Posted by Siren on July 15, 2016
PC users who are agonizing to remove Ads by Albireo will certainly find this entry instructive. Not all of the infected people are aware that they actually allowed this problem to occur in the first place, involuntarily though. This piece of adware arrives at computers with rogue downloads from unofficial sources. The installation isn’t completely […]
Read more →
Posted by Siren on July 15, 2016
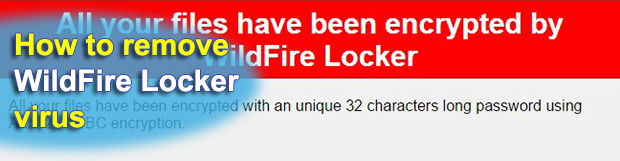
Judging from the name of WildFire Locker crypto ransomware, one might perceive it as a high-profile threat that encrypts victims’ data in the blink of an eye and cannot be defeated. In fact, however, it isn’t unique. It does implement the Advanced Encryption Standard flawlessly, and the user interaction modules are crafted professionally enough. But […]
Read more →
Posted by Siren on July 8, 2016
The updated edition of CryptXXX ransomware, also referred to as Microsoft Decryptor, has introduced a couple of new features. While the predecessor appended a random string at the end of filenames, such as .AF4D3, this one does not affect the look and feel of encrypted data at all. Furthermore, the Trojan now creates ransom notes […]
Read more →
Posted by Siren on July 6, 2016
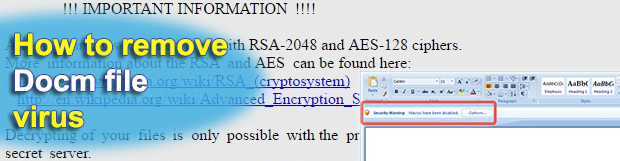
Cybercrooks use several different vectors to spread ransomware, a type of malicious code that takes one’s files hostage by encrypting them. Some samples arrive through the use of exploit kits whose efficiency depends on the presence of vulnerabilities on a targeted computer. Most incidents, though, involve spam emails that contain attachments in different formats. Docm […]
Read more →
Posted by Siren on June 28, 2016
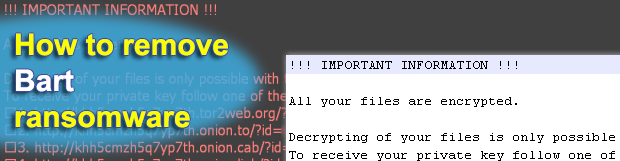
A new breed of Internet scum named the Bart ransomware entered a rapid circulation phase last weekend, with hundreds of Windows computers reportedly affected at the time of writing. Despite the apparent fact that the ransom instructions and the payment page design are nearly identical to those used by another plague called Locky, the principle […]
Read more →
Posted by Siren on June 28, 2016
Monetization of web traffic is a type of activity that cyber threat actors heavily engage in their malicious schemes. This tactic features a twofold benefit for the hackers. It is profitable due to third parties’ interest in the associated advertising opportunities. Furthermore, no one can really sue and prosecute them for hijacking web browsers, because […]
Read more →
Page 22 of 36 «...102021222324...»