Archive for KnowledgeBase
Posted by Siren on March 27, 2017
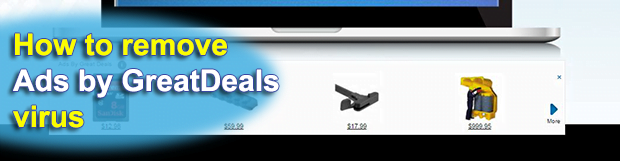
Ads on the Internet are okay as long as they aren’t intrusive beyond reason. In fact, without e-marketing the worldwide web wouldn’t be as fantastic a place as we know it. However, merchants, advertisers and other interested parties should stick with certain regulations so that end users are satisfied. In the case of Ads by […]
Read more →
Posted by Siren on March 17, 2017
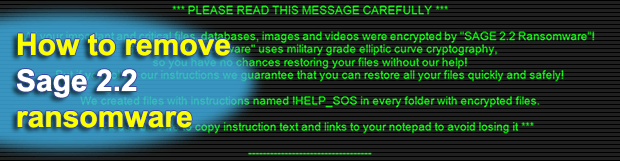
When confronted with a crypto hazard emanating from the Sage 2.2 ransomware, PC users and organizations run the risk of losing their important data if they have no backups. This infection is a prime example of benign technology being abused by unscrupulous individuals. Before the phenomenon of e-extortion emerged, cryptography had been a godsend for […]
Read more →
Posted by Siren on March 9, 2017
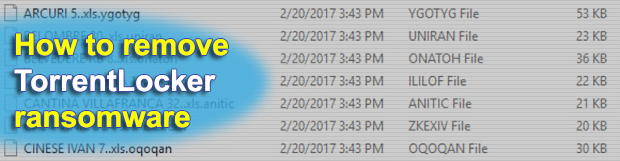
Although TorrentLocker was believed to have gone extinct, it has risen from the ashes. The name of this threat echoes back to 2015, when it denoted one of the most devastating and widespread samples of file-encrypting malware. Now in 2017 the infection has gotten a more powerful extortion toolkit and a new set of external […]
Read more →
Posted by Siren on March 3, 2017
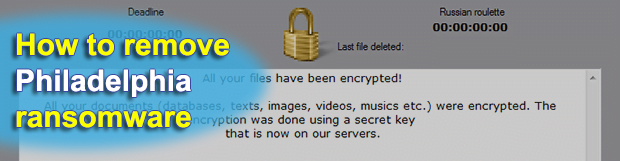
The ins and outs of the Philadelphia ransomware reflect the heterogeneity of the extortion-centered cybercrime underground. This sample is backed by a Ransomware-as-a-Service platform advertised on darknet sites and forums as an extensively flexible service to get the bang for one’s buck. Everyone interested can purchase a copy of the perpetrating program for $400 and […]
Read more →
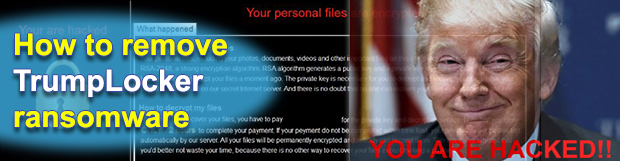
Posted by Siren on February 27, 2017
In a way, the ransom Trojan called TrumpLocker is off the beaten track. Also referred to as The Trump Locker, this strain has a bit of ridicule in it, mixed up with politics and some best-practice data encryption techniques. Expert believe it is a derivative of VenusLocker, an older online extortion family that’s been active […]
Read more →
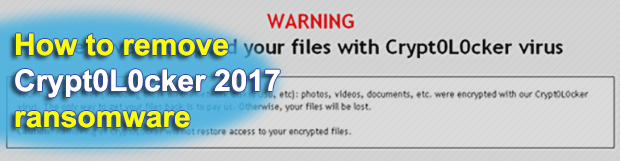
Posted by Siren on February 24, 2017
This article is about one of the longest-lasting online extortion campaigns to date. Originally known as TorrentLocker, the currently active ransomware called Crypt0L0cker has been around since late April 2015. Its authors have been able to get away with their filthy business because they craftily conceal their trail through the use of hard-to-track Bitcoin cryptocurrency […]
Read more →
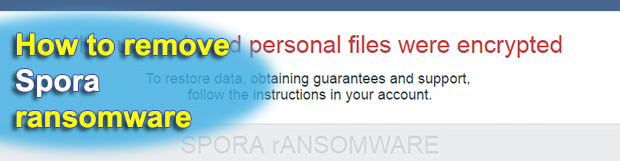
Posted by Siren on February 17, 2017
Whereas the indicators of compromise in the average ransomware attack predicament are usually uniform, different file-encrypting strains still have their unique properties. In the case of the relatively new Spora ransomware, offbeat characteristics are to the fore. It uses a nontrivial cryptographic technique to deny access to one’s data, implements a smart victim gradation tactic, […]
Read more →
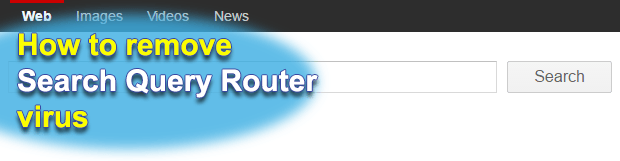
Posted by Siren on February 8, 2017
The fact that adware and browser hijackers are not considered to be severe infections doesn’t mean that they are safe to keep on a computer. Moreover, the impact may get serious as far as one’s privacy is concerned. The potentially unwanted program called Query Router (QueryRouter), for instance, collects personally identifiable data of users aside […]
Read more →
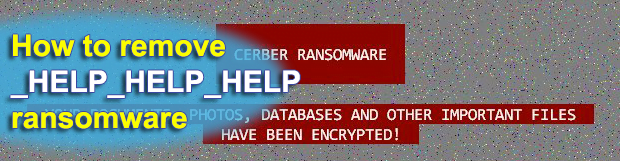
Posted by Siren on February 1, 2017
As the Cerber ransomware is approaching a one-year milestone of its abominable extortion crusade, its authors have rolled out another update to give their brainchild a slightly different look and feel. The fresh 2017 iteration currently on the loose sticks with a red color scheme for highlighting the text of the desktop warning. The most […]
Read more →
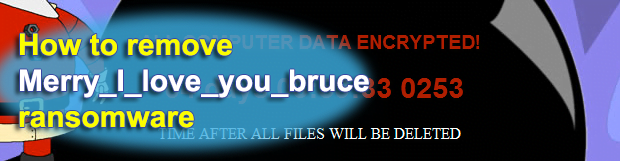
Posted by Siren on January 29, 2017
Ever since the ransomware called Merry X-Mas emerged, which was around last New Year, security analysts didn’t anticipate the campaign to last. No wonder, the Christmas theme comes and goes. But as it turned out, the infection is still alive and kicking as of now. Moreover, its latest mutation has led to the onset of […]
Read more →
Page 16 of 36 «...101415161718...»