Decrypt and remove TrumpLocker ransomware
In a way, the ransom Trojan called TrumpLocker is off the beaten track. Also referred to as The Trump Locker, this strain has a bit of ridicule in it, mixed up with politics and some best-practice data encryption techniques. Expert believe it is a derivative of VenusLocker, an older online extortion family that’s been active since late summer 2016. The successor under scrutiny, however, turns out to be somewhat more complex than its prototype.
Table of Contents
What is The Trump Locker ransomware?
TrumpLocker is a file-encrypting infection that targets Windows computers. It leverages a strong cryptographic algorithm to prevent victims from accessing their important data and then demands Bitcoins for decryption. This file scrambling routine, however, is quite selective. The offending program fully locks down some data types while jumbling up the inner structure of others only partially. The common distribution vector revolves around spam. The ransomware operators rely on a botnet to generate large volumes of rogue emails that carry harmful attachments with them. The attached ZIP files will typically have a JavaScript (.js) or HTA file inside, which, once opened, will trigger the infection chain.
At the initial stage of the attack, TrumpLocker reaches out to its Command and Control server provided that there is an active Internet connection. In response, the C2 submits the public encryption key as well as size of the ransom. Then, the crypto routine proper starts. As it has been mentioned above, this workflow is quite offbeat because the ransomware treats different types of data differently. The infection goes all the way with its file mutilation when locking down files stored in the most popular formats, including .txt, .doc(x), .rtf, .xls(x), .ppt(x), .php, .html and about 50 more. After the distortion job has been completed, these files will get .TheTrumpLockerf suffix concatenated at the end. For a much wider range of files, which are less popular and possibly less important to a victim, the ransom Trojan will only encipher the first 1024 bytes and append .TheTrumpLockerp extension to each. This way, it saves time and resources needed for the encryption.
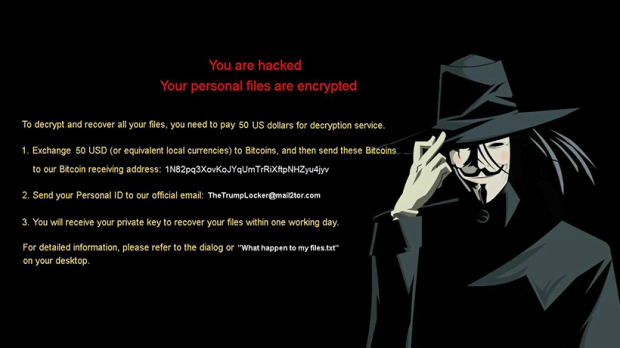
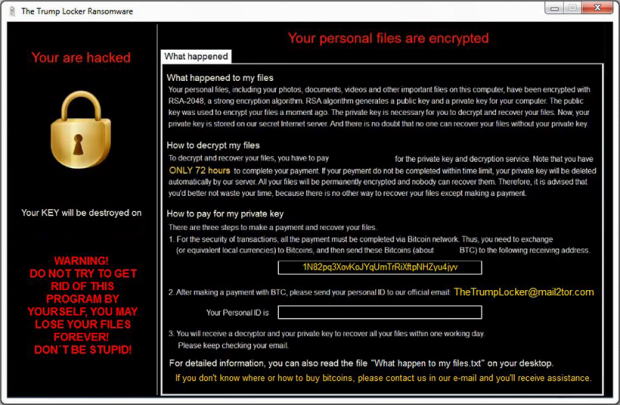
Furthermore, the original filenames get base64 encoded and therefore turn into strings of random 8 hexadecimal characters. The whole crypto chain being performed, the ransomware commences its direct communication with the victim. To this end, it generates a series of ransom notes. One of them is a plaintext file called “What happen to my files.txt” whose contents start with the phrase “Unfortunately, you are hacked”. Then, it replaces the desktop wallpaper with an image explicating the ransom demands. Next, the victim will see a photo of Donald Trump with “You are hacked!!” inscription at the bottom, but this screen is shortly taken over by a payment window. A victim is supposed to submit a 50-150 USD worth of Bitcoin to a BTC address indicated in the recovery how-to’s. Then, the infected user must send their personal ID to TheTrumpLocker@mail2tor.com email address to receive the private decryption key within one day.
TrumpLocker is, obviously, a serious threat that turns files into junk and won’t undo the bad effect until its distributors receive a payment. There is no working free decryptor available at the moment. However, the infection may fail to delete shadow copies of files, so it may be possible to use them for recovery. One way or another, try the tips below first. And the moral of the story is to stay away from suspicious email attachments and maintain data backups.
TrumpLocker ransomware automatic removal
Extermination of this ransomware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download TrumpLocker ransomware remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the ransomware and related infections removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the plague proper. Now you are facing a bigger challenge – try and get your data back.
Methods to restore files encrypted by TrumpLocker ransomware
Workaround 1: Use file recovery software
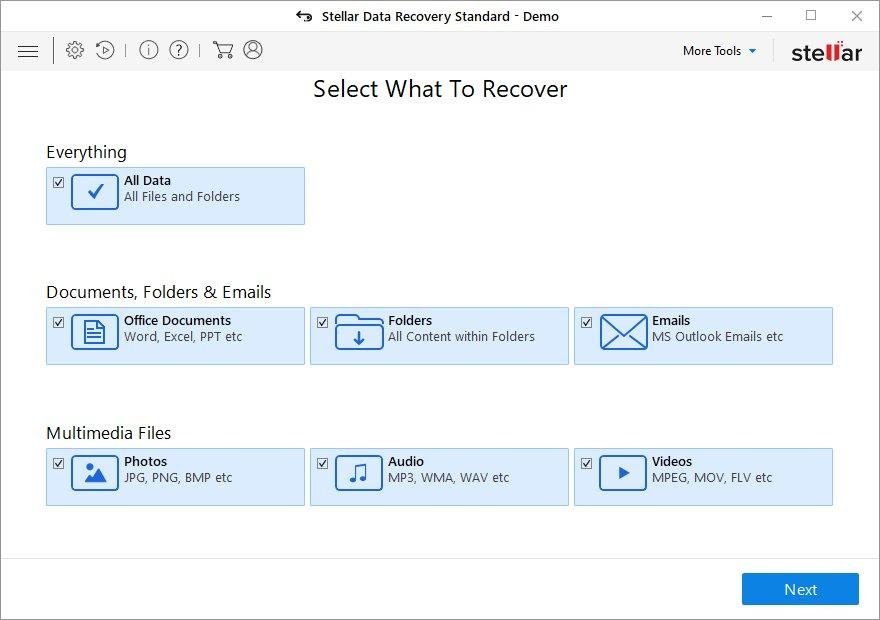
It’s important to know that the TrumpLocker ransomware creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Stellar Data Recovery for this purpose. The newest version of the ransomware under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Download Stellar Data Recovery Professional
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
-
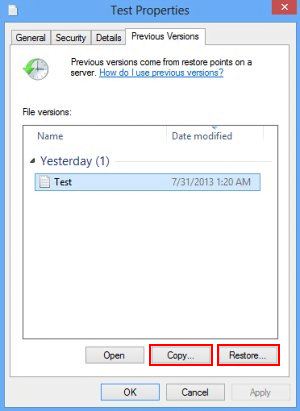
Use the Previous Versions feature
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.

-
Apply Shadow Explorer tool
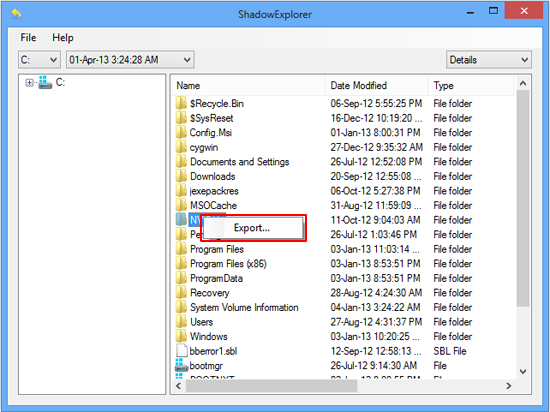
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.

Verify whether TrumpLocker ransomware has been completely removed
Again, ransomware removal alone does not lead to the decryption of your personal files. The data restore methods highlighted above may or may not do the trick, but the ransomware itself does not belong inside your computer. Incidentally, it often comes with other ransomware, which is why it definitely makes sense to repeatedly scan the system with automatic security software in order to make sure no harmful remnants of this ransomware and associated threats are left inside Windows Registry and other locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓