Sage 2.2 ransomware removal: decrypt .sage virus files
When confronted with a crypto hazard emanating from the Sage 2.2 ransomware, PC users and organizations run the risk of losing their important data if they have no backups. This infection is a prime example of benign technology being abused by unscrupulous individuals. Before the phenomenon of e-extortion emerged, cryptography had been a godsend for the purposes of secure communication. Malicious programs like Sage 2.2 turned this state of affairs upside down.
Table of Contents
What is the Sage 2.2 ransomware?
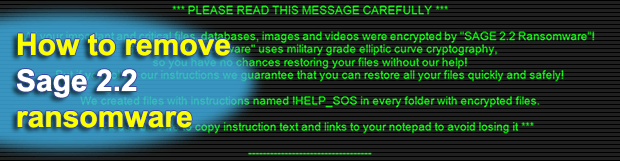
Sage 2.2 denotes a malicious computer program representing the second generation of a pervasive ransomware family. It sticks with a fairly commonplace attack cycle as for this category of perpetrating code. Having intruded on a Windows workstation through spam, it encrypts most of a victim’s personal files and displays recovery instructions presupposing a payment. The compromise is accompanied by a number of strain-specific attributes. Every encrypted file gets the .sage extension concatenated to its original name. Here is an example of this transformation: a spreadsheet called Timeline.xlsx assumes the shape of a no-longer-accessible Timeline.xlsx.sage object. Furthermore, the desktop of an infected machine gets occupied by a dark image in the background, with eye-catching warning text in it providing preliminary decryption steps.
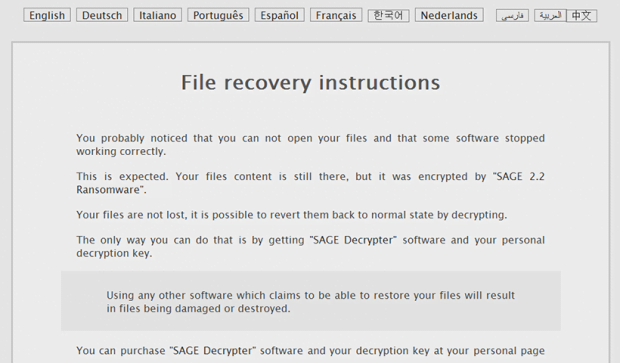
Ransom notes pose another inalienable component of the average file-tweaking onslaught. In the case of Sage 2.2 ransomware, the names of these extortionists-borne manuals have changed as compared to ones dropped by previous iterations of the infection. HTA files called !HELP_SOS, which are created by the current edition, are definitely hard to overlook. Not only do they emerge on the desktop, but they also show up inside every folder with encrypted files. What is more, the above-mentioned desktop wallpaper mentions !HELP_SOS.hta files in the context of data recovery avenue. When one of these is opened, a program interface titled “Decryption Instructions” pops up. It is interactive to an extent, enabling the infected user to select their preferred language before proceeding.
The ransom note’s contents are quite concise. It reads, “You probably noticed that you cannot open your files and that some software stopped working properly. This is expected. Your files’ content is still there, but it was encrypted by SAGE 2.2 Ransomware.” The message goes on to say that the only way to restore data is to purchase what’s called the “SAGE Decrypter” software and the personal decryption key. This is nothing but defiant extortion. Ultimately, the ransom manual recommends the infected person to follow a link provided in it, which leads to a Tor page named “User Cabinet”. Said online resource contains the price for recovery, which amounts to a Bitcoin equivalent of 2000 USD. It also has an embedded time lock system that displays how much time is left before the 7-day deadline expires and the ransom doubles.
As far as the propagation goes, Sage 2.2 ransomware is backed by spam. Misleading emails with malicious ZIP or JS files attached to them are the primary source of contagion. Therefore, it’s highly recommended to exercise caution with fishy messages from unfamiliar senders that end up in one’s email inbox. By the way, this rule of thumb applies to the majority of modern ransom Trojans. If the infection happens to have already messed up all important data on any given computer, the following tips may help mitigate the damage and restore some files.
Sage 2.2 ransomware automatic removal
Extermination of this ransomware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download Sage 2.2 ransomware remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the ransomware and related infections removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the plague proper. Now you are facing a bigger challenge – try and get your data back.
Methods to restore files encrypted by Sage 2.2 ransomware
Workaround 1: Use file recovery software
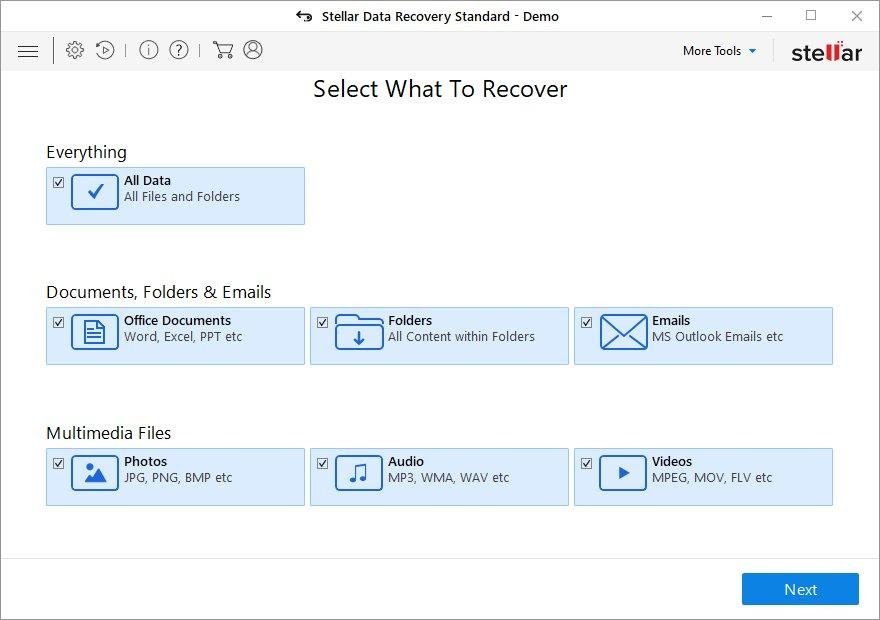
It’s important to know that the Sage 2.2 ransomware creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Stellar Data Recovery for this purpose. The newest version of the ransomware under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Download Stellar Data Recovery Professional
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
-
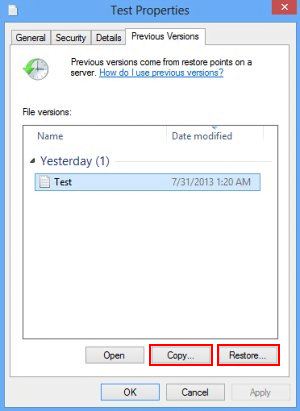
Use the Previous Versions feature
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.

-
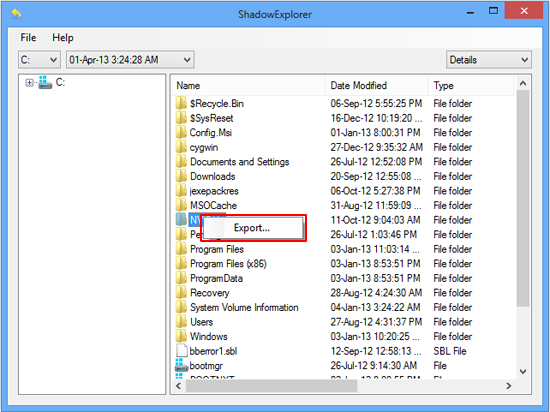
Apply Shadow Explorer tool
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.

Verify whether Sage 2.2 ransomware has been completely removed
Again, ransomware removal alone does not lead to the decryption of your personal files. The data restore methods highlighted above may or may not do the trick, but the ransomware itself does not belong inside your computer. Incidentally, it often comes with other ransomware, which is why it definitely makes sense to repeatedly scan the system with automatic security software in order to make sure no harmful remnants of this ransomware and associated threats are left inside Windows Registry and other locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓