Docm file virus phishing emails spread Zepto ransomware
Cybercrooks use several different vectors to spread ransomware, a type of malicious code that takes one’s files hostage by encrypting them. Some samples arrive through the use of exploit kits whose efficiency depends on the presence of vulnerabilities on a targeted computer. Most incidents, though, involve spam emails that contain attachments in different formats. Docm denotes one of the typical formats employed in such breaches.
Zepto ransomware, which is believed to be next in line to the niche of the Locky hoax, has got an entirety of cyber extortion properties under the hood. It uses an unbreakable mix of cryptosystems to make sure the infected person cannot open any of their personal files. It also leverages a robust command and control infrastructure, where links between components are established in a highly secure way due to The Onion Router technology. Meanwhile, the mechanism used to deliver the harmful loader hadn’t been too widespread until recently. The criminals have been conducting a large-scale phishing offensive, where unsuspecting users receive messages that look interesting enough to open and see what’s inside.
An example would be an email allegedly sent by someone claiming to be a sales director, reading, “Attached please find the documents you requested,” or “Image data has been attached to this email.” The attachment turns out to be a .docm file. This is a type of Microsoft Word document that can carry obfuscated scripts in the Visual Basic for Applications programming language. These VBA components can be used to execute malicious code on the PC behind the scenes.
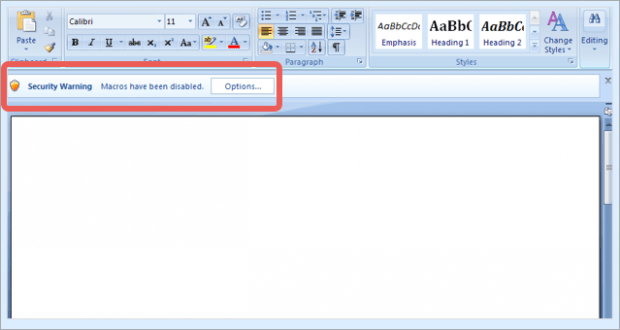
Strangely enough, the random-named docm objects involved in these attacks return a blank MS Word document. Similar campaigns in the past used to leverage files where users could actually see some unintelligible content. One way or another, the document will display an alert that says, “Security Warning, macros have been disabled,” and prompt the would-be victim to click Options and toggle their security settings.
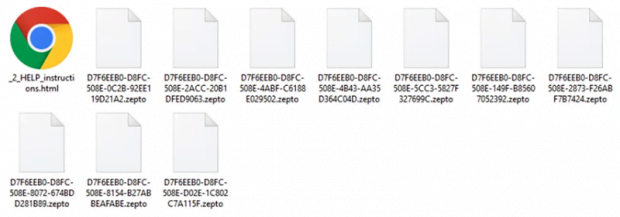
As soon as the unwary user follows this recommendation and enables macros in the docm file, the Zepto payload will instantly do its job and install the ransomware silently. When on board, the virus will scan the hard drive, removable drives and network shares for popular categories of files. The infection encodes everything detected in the course of this scan with AES-128 and then encrypts the AES key with RSA crypto. This will prevent the victim from opening these data. The Trojan also modifies the way the affected files look, concatenating the .zepto extension to them and turning filenames into 32-character strings that have nothing in common with the original names.
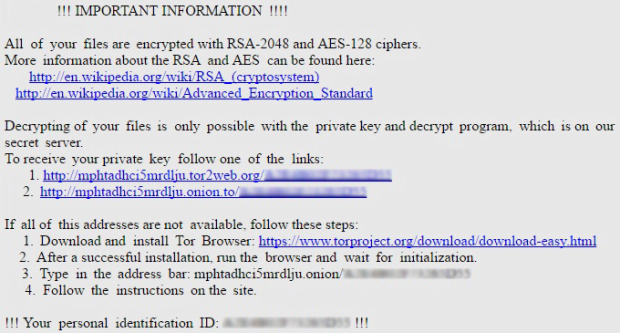
For the compromised user to find out what to do next, the Zepto ransomware changes the desktop wallpaper to _HELP_instructions.bmp image and drops the _HELP_instructions.html note in every repository with encrypted data. These directions urge the person to navigate to the Locky Decryptor Page using a specified Tor gateway, and pay 0.5 Bitcoin for the private RSA key and the downloadable decrypt tool. This, of course, is a terrible bargain, but some users have given in and submitted the equivalent of about 300 USD to rescue their valuable files. Not all of these cases have reportedly ended well – some people never received their decryptor. This is why it’s a bad idea to trust ransomware makers who infected the computer in the first place. There are much more judicious options.
Table of Contents
Docm file automatic removal
Extermination of this ransomware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download Docm phishing remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the ransomware and related infections removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the plague proper. Now you are facing a bigger challenge – try and get your data back.
Methods to restore files encrypted by Docm file
Workaround 1: Use file recovery software
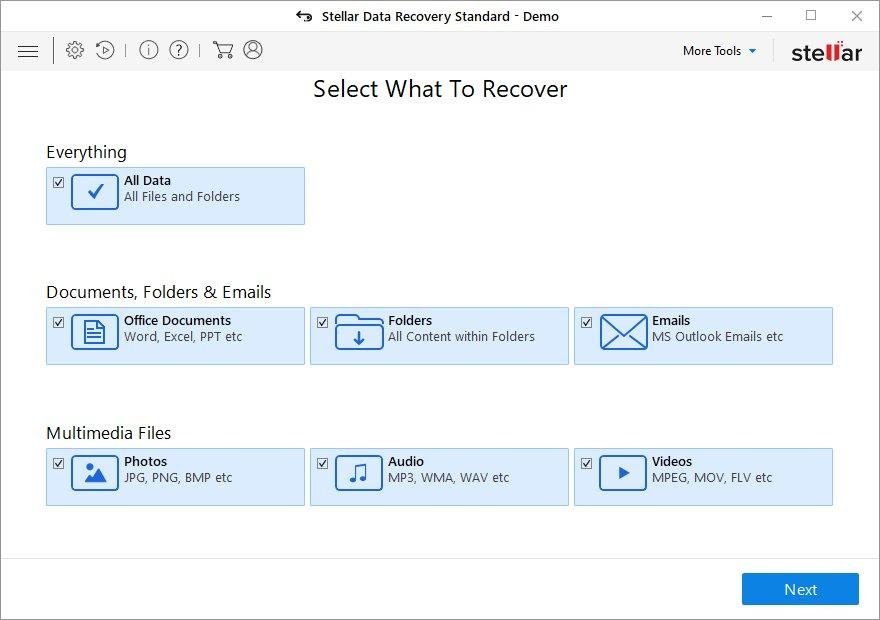
It’s important to know that the Docm file creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Stellar Data Recovery for this purpose. The newest version of the file under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Download Stellar Data Recovery Professional
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
-
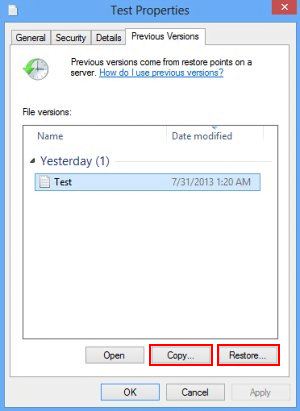
Use the Previous Versions feature
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.

-
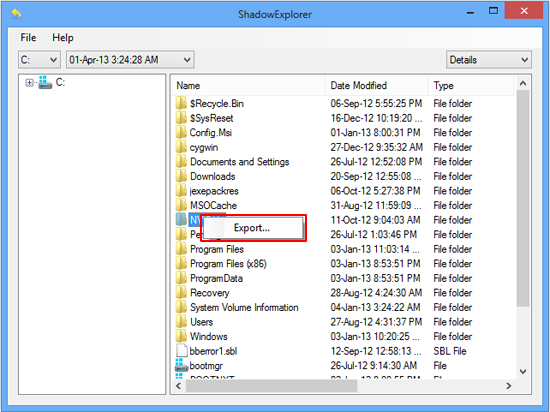
Apply Shadow Explorer tool
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.

Verify whether Docm file has been completely removed
Again, phishing removal alone does not lead to the decryption of your personal files. The data restore methods highlighted above may or may not do the trick, but the ransomware itself does not belong inside your computer. Incidentally, it often comes with other file, which is why it definitely makes sense to repeatedly scan the system with automatic security software in order to make sure no harmful remnants of this file and associated threats are left inside Windows Registry and other locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓