Archive for KnowledgeBase
Posted by Siren on July 30, 2017
There are perpetrating programs that impair computers directly in various ways. The infection called Trojan.Pidief.X, though, happens to be different. Its objective is to promote other malicious code. Furthermore, its activity involves a great deal of manipulation reminiscent of classic social engineering techniques. The harmful component is camouflaged as a benign PDF file, so users […]
Read more →
Posted by Siren on July 30, 2017
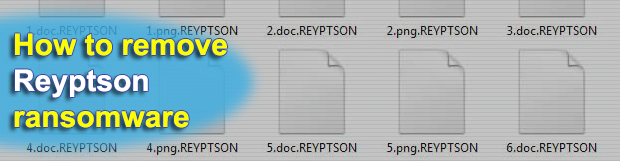
Ransom Trojan rarely deviate from the well-trodden extortion route. The new sample called Reyptson is one of the very few that leverage offbeat tactics when deploying its infection chain. It performs some extra reconnaissance on a contaminated computer, harvesting the victim’s email credentials in order to self-spread via spam automatically generated from the host. What […]
Read more →
Posted by Siren on July 25, 2017
Most of the extortion taking place online revolves around two things: applying crypto and locking the screen. The brand new Android ransomware called LeakerLocker utilizes one of above components and adds a unique one to the mix. It locks the home screen of an infected Android device and threatens to disclose the victim’s personal data […]
Read more →
Posted by Siren on July 25, 2017
The word “copycat” has assumed a brand-new conceptual hue with the emergence of the apropos Android malware. This polysemy is all about malicious code dubbed CopyCat. It is distributed via phishing and trojanized applications, and the subsequent impact is harsh. The malware engages in stealth malvertising, pilfers credits for installed programs, and gets high-level privileges […]
Read more →
Posted by Siren on July 19, 2017
According to recent reports on computer threat landscape, the Cerber ransomware family is the dominating one in its niche of cybercrime. It holds the top position owing to a number of characteristics. First off, the distribution channels have been consistently well-thought-out. Secondly, its code boasts anti-virtualization features to prevent analysis, and the crypto is uncrackable. […]
Read more →
Posted by Siren on July 12, 2017
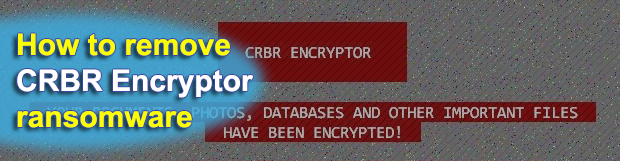
The ubiquitous ransomware epidemic continues to dodge conventional defenses when plaguing users around the globe. The theme of code inheritance is in vogue with cyber extortionists for a reason. This way, they fine-tune their malicious programs to make them increasingly elusive and more difficult to crack. That’s what happened in early July 2017 with the […]
Read more →
Posted by Siren on July 12, 2017
Ideally, it’s up to the user to define web surfing preferences. Configuration flexibility of the present-day browsers is certainly an incredibly convenient hallmark simplifying one’s online experience. However, the whole handiness goes down the drain if a third-party application takes over these settings. This is the case with the potentially unwanted program (PUP) called Cleanserp. […]
Read more →
Posted by Siren on June 26, 2017
In a cyber world full of predators like crypto ransomware and banking Trojans, there is also room for lower-impact infections. Browser hijackers, for example, do not affect victims’ data but cause a great deal of problems as they redirect Internet traffic to unwanted places. One of these threats called Bigpicturepop performs the function of an […]
Read more →
Posted by Siren on June 15, 2017
It’s not only legit software that’s subject to regular updates – malicious code like ransomware is far from being a stationary target, so it tends to undergo tweaks once in a while too. The extortion-oriented strain known as CryptoMix has recently given rise to a new variant that appends the .MOLE02 extension to enciphered files. […]
Read more →
Posted by Siren on June 14, 2017
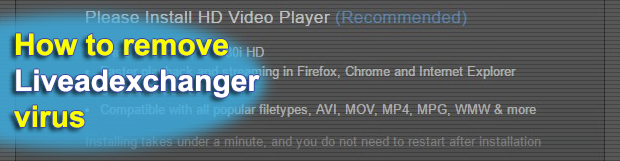
Just like commonplace tangible products, Internet traffic is a commodity that can be bought and sold. This property makes it an indispensable entity used in various online monetization frameworks. Unfortunately, such schemes can be both legit and malicious. In the case of browser redirects via Liveadexchanger.com, the profit is shady by all means. What is […]
Read more →
Page 13 of 36 «...101112131415...»