Archive for KnowledgeBase
Posted by Siren on September 28, 2017
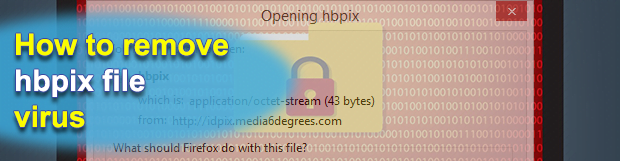
There is an ongoing malware distribution wave that engages a clever drive-by download trick. Users have been reporting an issue where a suspicious file named ‘hbpix’ gets automatically downloaded during their web browsing sessions via Chrome or Firefox. This entity turns out to be a PUP tailored for ads serving and surreptitious tracking of user […]
Read more →
Posted by Siren on September 20, 2017
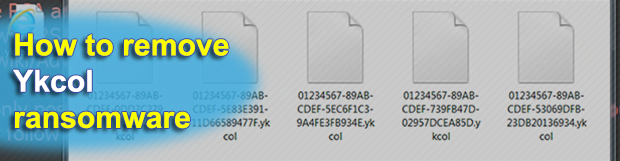
New version releases are a common thing in the ransomware underground. The prolific Locky strain is no exception. Less than a month since the previous iteration called Lukitus surfaced, the architects of this massive campaign have come up with an update. The brand new edition appends the .ykcol extension to ransomed data, hence its catalogued […]
Read more →
Posted by Siren on September 14, 2017
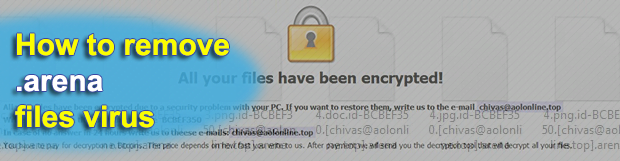
When a blackmail Trojan hits a computer, things get out of hand. The depth of impact depends on how professionally designed a specific strain is, including cryptographic strength and the way the infection handles encryption keys. The new Arena version of the CrySiS/Dharma ransomware is one of the ransomware species you don’t want to encounter. […]
Read more →
Posted by Siren on September 11, 2017
There aren’t many domains as sensitive for the average person as the services of airlines. People naturally want to stay on top of flight schedules as well as the status of booking transactions and payments. Online fraudsters couldn’t have possibly walked by this segment of economy. A recent scam, for instance, distributes malware by duping […]
Read more →
Posted by Siren on August 28, 2017
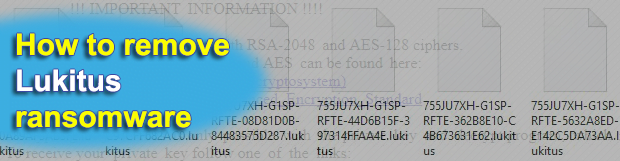
Although the Locky ransomware family is no longer dominating the online extortion business, it is still in game. A recent proof of its longevity is the emergence of a new variant that adds the .lukitus extension to encrypted files and drops rescue notes named lukitus-[random].htm and lukitus-[random].bmp. This article sheds light on all hallmark signs […]
Read more →
Posted by Siren on August 25, 2017
The word ‘CrySiS’ may seem like an awful misspelling, but it makes perfect sense in the context of cybersecurity. Said term designates one of the oldest and largest known families of file-encrypting malware. Also known as Dharma, this underground workshop of digital pests has given rise to dozens of variants during its existence. The newest […]
Read more →
Posted by Siren on August 17, 2017
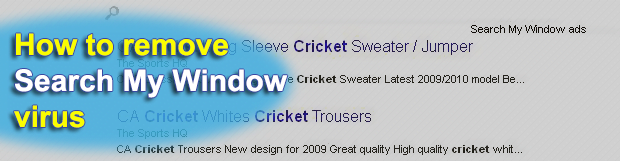
The controversy about online ads is that they can either enhance one’s browsing experience or diminish it considerably. The latter effect is typically associated with PUPs, or potentially unwanted programs, like Search My Window. These types of applications literally flood search results and regular web pages with redundant advertising, thus preventing victims from seeing what’s […]
Read more →
Posted by Siren on August 15, 2017
Malspam is, by far, the main vector of malware distribution nowadays. It has become cybercrooks’ favorite due to its universality – it allows them to spread virtually any malicious program by simply attaching booby-trapped files to such emails. Sometimes these campaigns harness well-known brand names or services to appear more persuasive, as is the case […]
Read more →
Posted by Siren on August 14, 2017
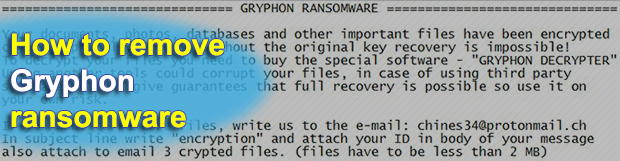
Cybercriminals are well motivated as long as their misdemeanor brings them a pretty penny. This seems to be the case with the new Gryphon ransomware. Having landed on a targeted host, it denies accessibility of the victim’s important files, appends them with the .gryphon extension and holds them for ransom. Learn what lineage this sample […]
Read more →
Posted by Siren on August 11, 2017
When a ransom Trojan gains a foothold on one’s computer, things get out of hand as the infection intelligently spots the most valuable files and scrambles them using cryptography. This classic assault workflow fully applies to the Cry36 virus representing one of the most widespread ransomware lineages circulating in 2017. Peruse this article to get […]
Read more →
Page 12 of 36 «...1011121314...»