Remove CopyCat malware from Android device

The word “copycat” has assumed a brand-new conceptual hue with the emergence of the apropos Android malware. This polysemy is all about malicious code dubbed CopyCat. It is distributed via phishing and trojanized applications, and the subsequent impact is harsh. The malware engages in stealth malvertising, pilfers credits for installed programs, and gets high-level privileges on infected devices.
CopyCat Android malware isn’t new. It was first discovered in spring 2016 and has been since proliferating at a huge pace. The numbers speak for themselves: the infection under scrutiny contaminated about 14 million Android devices and was able to root more than a half of them. The financial turnout of this campaign is probably enviable even for well-off crypto ransomware distributors – the perpetrating program earned its authors somewhere around $1.5 million in fraudulent ad revenues. The geographic coverage of the onslaughts is mostly concentrated in Asia (55%), Africa (18%), as well as North and South America (12%). Interestingly, the attack process gets terminated if the malware identifies that the host device is located in China. This fact might be a clue for attack attribution.
So how does the CopyCat malware propagate? Unofficial app stores pose the main source of the contagion. The threat actors are evidently in cahoots with some of these third-party resources, providing booby-trapped variants of regular applications on a freeware basis. Would-be victims reportedly also get hit by downloading software promoted via phishing scams. If a targeted person happens to let the bad code in, it stays dormant until next reboot in order to tangle the cause-and-effect analysis. Then, CopyCat covertly reaches out to a specific web storage in order to download a pack of exploits. These exploits are required to gain root access on the device. In the event this phase of the attack chain is successful, the virus incorporates itself into Zygote, a built-in Android component tasked with triggering various processes. This way, the offending code can obscurely blemish all running apps with its shady characteristics.
The adverse outcome of this deep intrusion is twofold: it steals ad revenue and installs other malicious entities behind the victim’s back. The former aspect of the breach aftermath, in its turn, can be broken down into defiant display of redundant ads and theft of ecommerce rewards paid by merchants for app promotion. A really top-notch fraudulent mechanism employed by CopyCat is the replacement of genuine referrer ID value with a different one. This means that the malware deployers get credit for every application the user installs on their smartphone or tablet. To top it off, the CopyCat malware also performs some reconnaissance on plagued devices, harvesting such information the model, Android build, and the victim’s country.
All in all, this pest is sophisticated, harmful, and incredibly proficient in obfuscating its activity. Some of the ways to determine whether it is on board are as follows: obnoxious popup ads keep appearing on the screen, and new apps are getting installed once in a while without authorization. If you have noticed one or both of these symptoms, be sure to follow the steps below to locate and remove CopyCat malware.
CopyCat malware removal
What you need to do is uninstall the application that’s causing trouble. As it has been mentioned, however, disabling and removing the virus in regular mode is to no avail, so the steps below are must-follow.
1. Boot the device into safe mode
– Press and hold the Power button until the respective screen pops up
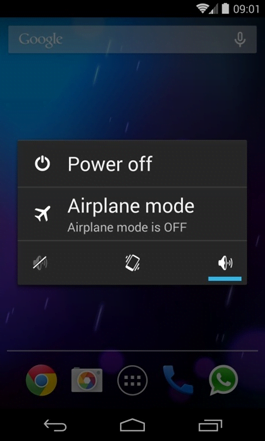
2. Now tap and hold the option that says Power off. Depending on the vendor and the phone model, the methods can vary. If nothing happens as a result of the above manipulations, power down the device, then press and hold the Volume Down and Volume Up buttons simultaneously while it’s starting back up.
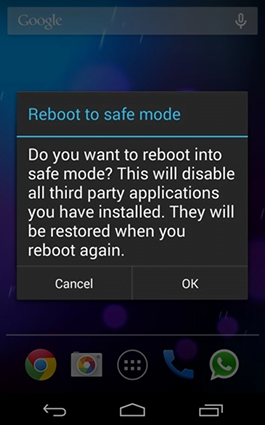
3. Confirm rebooting into safe mode by tapping OK
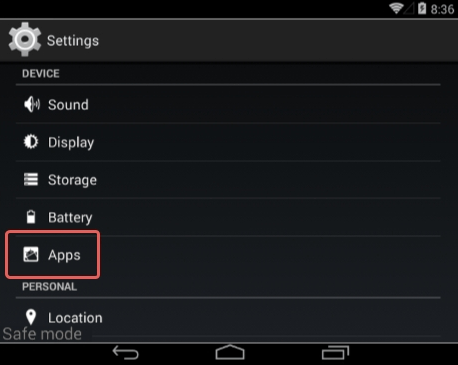
4. When in safe mode, go to Settings and select Apps
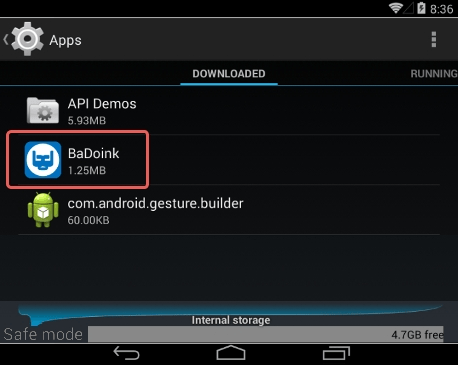
5. Look down the list of programs and locate a suspicious app or apps that were recently installed
6. Tap each potentially unwanted app in turn and select the Uninstall option. If this button is not active, try Force stop first
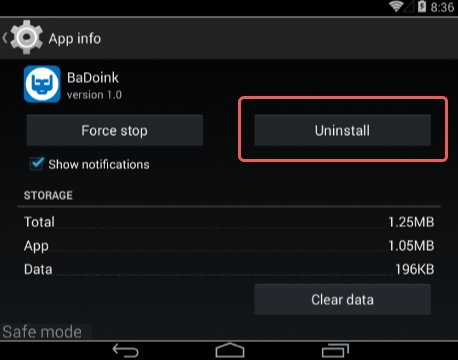
7. Tap OK on the confirmation dialog to uninstall the potentially unwanted app
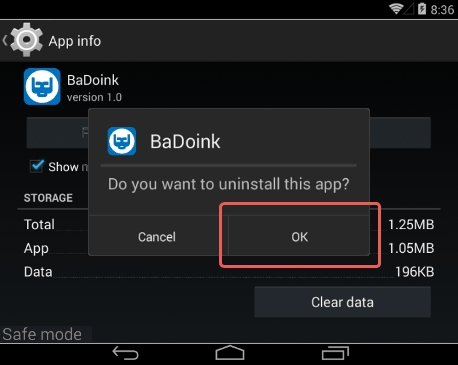
8. Restart into standard mode. The CopyCat malware should have now vanished from your Android device. You might also want to consider installing a mobile security solution to prevent attacks of this sort further on.
Posted in: KnowledgeBase
Leave a Comment (0) ↓
