Archive for KnowledgeBase
Posted by Siren on February 21, 2019
A hijacked web browser is a calamity to the user because a great deal of control over online surfing vectors is no longer at their discretion. This problem originates on the software level, where a mischievous program generically categorized as ‘adware’ gets aboard the computer in a sneaky way. The bad code changes a number […]
Read more →
Posted by Siren on February 21, 2019
What is SecuryBrowse extension virus? SecuryBrowse is a browser add-on distributed with a range of methods. True, it sounds legitimate being available from Chrome Web Store. Meanwhile, the users concerned and IT observers report it unwanted as the adware infiltrates into operating systems using a bundled download method. That is, you rather get one as […]
Read more →
Posted by Siren on February 19, 2019
It is not a secret that popular communication services are unsafe. At any time, your correspondence may be intercepted by law enforcement agencies or hackers. In this article, I will tell what you need to remember when using various means of communication. Voice calls and messages End-to-end encryption can help protect your conversations and messages […]
Read more →
Posted by Siren on February 16, 2019
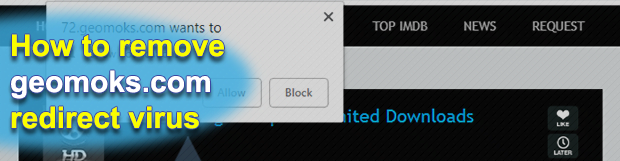
The Geomoks virus keeps up the adverse trend of duping computer users into allowing notifications for dodgy websites. This hoax is currently gaining momentum as it might allow cybercrooks to gain elevated privileges in one’s system, harvest sensitive online information, and execute arbitrary malicious code in the background. The annoying popups on geomoks.com are the […]
Read more →
Posted by Siren on February 12, 2019
The adware climate is constantly getting rainier, with numerous new intrusive samples of browser redirect and popup viruses splashing onto the scene in an unstoppable fashion. A particularly unwelcome trend in this context is that more and more of these infections are assuming cross-platform characteristics, as is the case with the novelcamp.net nuisance that affects […]
Read more →
Posted by Siren on February 4, 2019
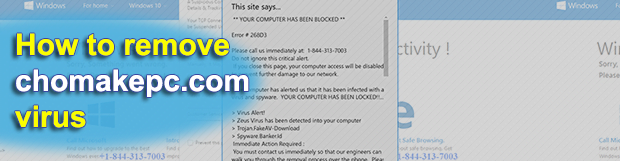
When it comes to the vectors of present-day cybercrime, social engineering can be just as effective as purely malware-based campaigns. If the two are combined, the resulting mix tends to be nasty. This holds true for the tech support scam involving the chomakepc.com domain. In pursuit of easy gain, its operators spread a browser hijacking […]
Read more →
Posted by Siren on January 30, 2019
Malicious code can be multipurpose and affect the host system in several ways rather stick with one vector of compromise. The Occamy.C virus is one of the culprits whose behavior cannot be unambiguously characterized impact-wise. However, its fundamental characteristic is all about the ability to communicate with a remote server. Here are the ins and […]
Read more →
Posted by Siren on January 27, 2019
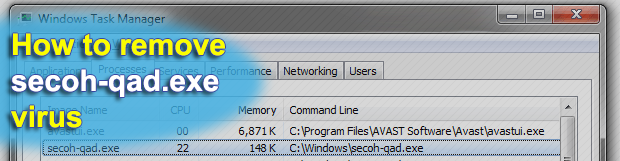
Taking software piracy seriously isn’t everyone’s first priority these days, to say the least. Computer users like to get applications on the cheap or for free. As understandable as it is, this quirk may lead them into a trap. The secoh-qad.exe malware issue demonstrates how dangerous it can be to activate Windows products while bypassing […]
Read more →
Posted by Siren on January 23, 2019
There are computer viruses covert by design that don’t raise any obvious red flags, such as bots and spyware. The one called TheGoodCaster isn’t like that at all. It manifests itself by triggering browser redirects so that the victim keeps visiting rogue sites asking for extended permissions. The goal is to generate ad revenue at […]
Read more →
Posted by Siren on January 20, 2019
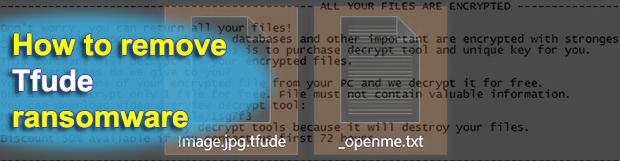
What makes ransomware stand out from the crowd is its critical, or sometimes irreversible, adverse effects. As opposed to other malware deployers, the cybercriminals who run these campaigns don’t zero in on manipulation or information theft. Instead, they target the most precious digital asset of users and organizations – their data. One of the strains […]
Read more →
Page 5 of 36 «...34567...» 
![Remove MySearch.com virus in Chrome, Firefox and IE [upd. Feb 2019]](https://soft2secure.com/wp-content/uploads/remove-mysearch-com.png)