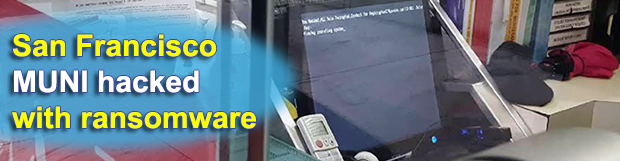
San Francisco MUNI hacker hacked
Most ransomware deployers manage to stay unidentified because they exercise good OPSEC backed by The Onion Router and Bitcoin. The case of the cybercrook who compromised the computer network of the San Francisco Municipal Transportation Agency (Muni) last Friday turned out to be the exception rather than the rule. According to Brian Krebs, a well-known […]
Read more →Posted in: News
Leave a Comment (0) →