CrySiS ransomware decryptor: decrypt .xtbl and .crysis files
Ransomware operators appear to be realizing the risk of being exposed and prosecuted. This pressure is being heated up by the fairly successful activity of Chainalysis, a relatively new startup aimed at tracking Bitcoin transactions. This initiative may lead to effective attribution of ransomware attacks through chasing the cryptocurrency paid by victims. The breaking news in this context is the release of master decryption keys by the authors of Crysis, one of the prevalent crypto maladies out there. The above reasoning for this is a speculation rather than a fact, but it’s one of likely causes for ransomware developers to abandon their campaigns.
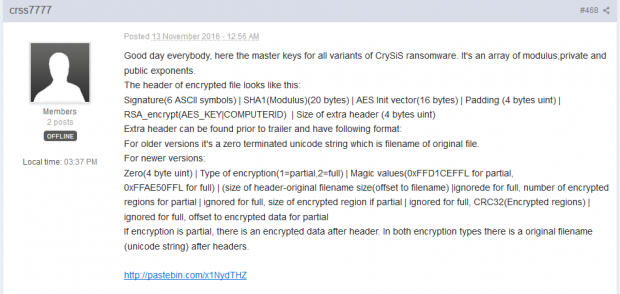
This event is the exception rather than the rule. The only similar past incident we can recall has to do with the TeslaCrypt ransomware, whose makers published the universal file recovery key for their perpetrating program in late May 2016. The crooks behind the Crysis ransomware decided to follow suit and made the master keys readily available for everyone infected. A user nicknamed crss7777 posted the following information in a dedicated Crysis thread at Bleeping Computer forums on November 13.
Whatever this mysterious individual’s motivation was, he provided a link to a Pastebin page that contains the decryption keys for all versions of this ransom Trojan. The post also includes information about the header of an arbitrary encoded file and encompasses some basic instructions to start the restoration process.
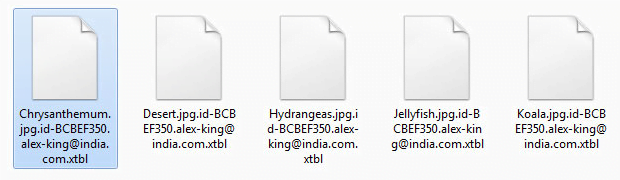
Before we proceed to the actual decryption routine, it makes sense to describe some characteristics of the ransomware in question. Crysis proliferates via spam that delivers contagious documents disguised as payment reports, receipts and the like. The attachments are mostly Microsoft Word documents that display a prompt to enable macros once opened. The infection then exploits a known macros vulnerability to deploy the attack. The ransomware encrypts the victim’s personal files and appends a new extension with the .xtbl or .crysis string at the end.
The extensions concatenated to Crysis-encrypted files are in the following format: .id-[random hexadecimal chars].[email address].xtbl. For instance, an image named “nature.jpg” can assume a shape similar to “nature.jpg.id-ACDEB350.alex-king@india.com.xtbl”. Other known email addresses constituting this array include vegclass@aol.com, freetibet@india.com, redshitline@india.com, bitcoinrush@aol.com, centurion_legion@aol.com, donald_dak@aol.com, alex.vlasov@aol.com, milarepa.lotos@aol.com, johnycryptor@hackermail.com, johnycracker@hackermail.com, redbleepline@india.com, meldonii@india.com, ecovector3@india.com, legioner_seven@aol.com, or datastorm@india.com. The ransomware also changes the desktop wallpaper to an alert image and creates ransom notes called Readme.txt.
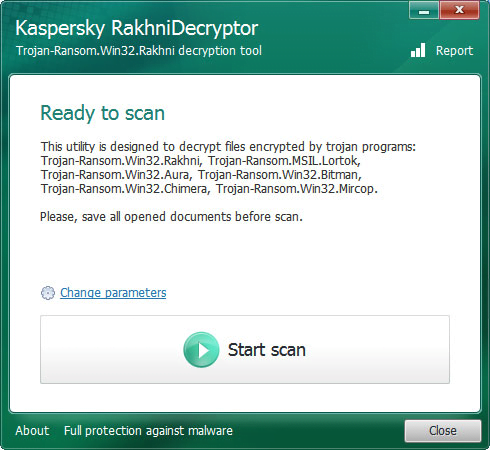
Now that it’s clear what a Crysis attack looks like, it’s time to have a look at how the recently released master key can help decrypt the .xtbl files. To the average user, the information published by the ransomware dev on Pastebin looks like a Chinese puzzle. Fortunately, there is a user-friendly solution that does the trick automatically. A tool called the RakhniDecryptor by Kaspersky Lab is the missing link in this data recovery process. The researchers have included the master decryption keys in the latest version of this utility.
How to decrypt .xtbl files locked by the Crysis ransomware
First, download Kaspersky RakhniDecryptor. It comes as a 4.9 MB compressed folder. Extract the actual decryptor from this ZIP archive and launch it. Importantly, make sure the product version is 1.17.8.0 or newer – the previous editions won’t be able to restore .xtbl or .crysis files. Check the version number by clicking the About button on the tool’s GUI.
Now click the Start scan button on the RakhniDecryptor interface. You will see a window titled “Specify the path to one of encrypted files”. In this pane, browse to a folder with inaccessible .xtbl or .crysis entries and select one such file. It can be an encrypted Microsoft Office document, an audio or image file, a ZIP archive or a PDF item. Be advised the tool doesn’t support TXT files, so ignore them.
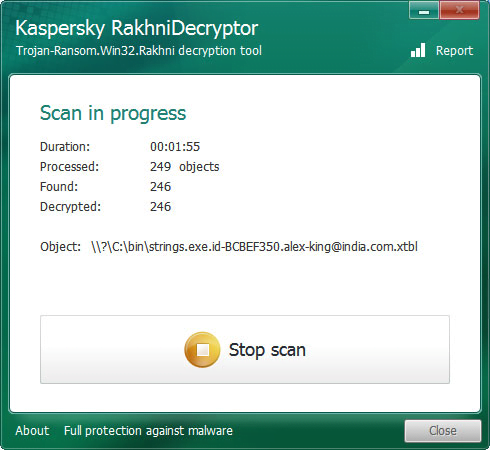
Having selected an object that meets the above criteria, click Open in the bottom right-hand part of the interface. The application will then start scanning the computer for files encrypted by the Crysis ransomware and decrypting them.
Keep in mind that the scan and decryption may be time-consuming. But the wait is worth it. The interface provides detailed scan progress information, including the duration, the number of files found and decrypted, and the path to an item being currently processed. Having completed the scan, RakhniDecryptor will return a full list of files it was able to decrypt.
To wrap up, it’s worth mentioning that cases like this are extremely rare. It’s not reasonable to expect that online extortionists behind different ransomware strains will be releasing master decryption keys like the authors of Crysis did. So be sure to have a response plan for predicaments like crypto ransomware assaults. Back up your important data, keep your antimalware up to date, patch Adobe Flash Player and Java regularly, and follow safe practices with spam email attachments.
Posted in: News
Leave a Comment (0) ↓