San Francisco MUNI hacked with ransomware
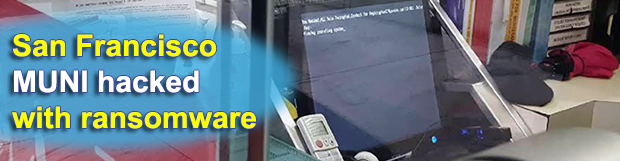
The IT infrastructure of the San Francisco Municipal Transit Agency (SFMTA), also referred to as Muni, has been suffering a deep ransomware impact since last weekend. The perpetrating program called HDDCryptor, also known as Mamba, hit more than 2,000 machines on Muni’s network. The collateral damage is that the infection disabled the agency’s digital fare systems, so passengers could have free rides for a few days. The network remains paralyzed at the time of writing.
This breach, which is reminiscent of science fiction movie plots, reportedly took place on November 25. The fact that ticketing kiosks have been out of order ever since might be good news for the Metro light-rail service users who like freebies, but it’s certainly a disastrous predicament that demonstrates how badly cybercriminals can affect the real-world critical infrastructure. In fact, the compromise of the automatic faring platform is just the tip of the iceberg. The disk-encrypting ransomware also hit Muni’s email and print servers, multiple MySQL database components, CAD workstations, employee machines, lost and found property terminals, as well as personnel training and payroll systems. The attack surface is, obviously, huge.
The compromised machines won’t load the operating system, displaying the following message on the lock screens: “You hacked, all data encrypted, contact for key (cryptom27@yandex.com).” After Muni representatives had sent an email to the address indicated in the ransom note, they received recovery instructions in response from the attackers operating under the name of “Andy Saolis”. The extortionists, who are holding 2,112 SFMTA’s computers hostage, demand 100 BTC for all the AES (Advanced Encryption Standard) decryption keys. The ransom is the equivalent of about 73,000 USD at this point.
Luckily, the cryptom27@yandex.com virus has not affected Muni’s backup servers, so it may be possible to regain access to the currently locked workstations and restore the encrypted critical data. The effectiveness of this recovery route, though, depends on how old the backups are. One way or another, the company has not paid the ransom, nor have they succeeded in regaining access to their disabled servers thus far.
The troublemaker, HDDCryptor ransomware, stands out from the crowd of conventional file-encrypting Trojans in that its impact is twofold. Not only does it encrypt individual files stored on a compromised computer, but it also overwrites the Master Boot Record (MBR) of a compromised computer with a bootloader of its own. In fact, this particular strain is the oldest known ransomware of its kind, but it hadn’t hit the headlines until it started compromising high-profile targets like San Francisco Muni.
The malady mainly propagates via rogue downloads hosted on malicious websites, although some victims have reported spam-based distribution. In light of the increase of HDDCryptor infections, organizations should adopt ransomware-specific personnel training programs so that employees will exercise some extra caution with shady downloads and phishing email attachments.
Posted in: News
Leave a Comment (0) ↓

