Archive for KnowledgeBase
Posted by Siren on October 29, 2015
New tab, homepage and search settings of web browsers are the most targeted areas as far as adware attacks go. Tweaking these defaults is what suffices malicious application publishers out there to make sure Internet traffic gets driven to multiple lookalike landing pages that bear hardly any informative component. That’s the exact operational vector that […]
Read more →
Posted by Siren on October 28, 2015
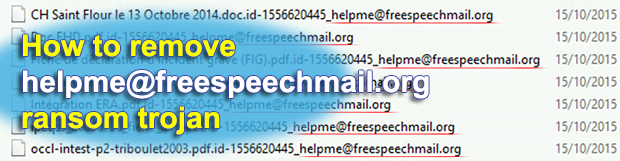
Helpme@freespeechmail.org, an innocuous email address at first sight, is a distinguishing attribute of a new ransomware campaign. As a result of the compromise, the respective string is automatically added at the end of every personal file stored on the computer, including .pdf and .doc objects. Furthermore, file formats can be changed to .fff or similar, […]
Read more →
Posted by Siren on October 26, 2015
The wicked idea of taking someone’s personal files hostage to then extort a ransom is trending in malware deployment workshops. If one of these ransomware programs called TeslaCrypt succeeds in intruding on a computer, it detects and encrypts all user files so that they get appended with a .ccc suffix and cannot be opened in […]
Read more →
Posted by Siren on October 23, 2015
The predicament where a computer program calling itself the Crypt0L0cker says it has encrypted one’s personal files is an awful mishap. To begin with, this ransomware isn’t kidding when making such statements. Secondly, buying decryption seems to be the only applicable method to get the data back. This post explains the anatomy of this malware […]
Read more →
Posted by Siren on October 19, 2015
DNS Unlocker application gets awful feedback while boasting unique VPN services that are allegedly built in. The reasons for this inconsistency aren’t difficult to explain as long as the hidden features of this program get unveiled. This post will give you a perfectly clear idea why this software is tagged malicious and what should be […]
Read more →
Posted by Siren on October 17, 2015
Easy Calendar seems to be an innocuous application for organizing tasks and adding reminders, but it acts as an adware and hence doesn’t belong on a computer. It may appear that no particular hazard should ever emanate from simplistic and lightweight apps like calendars, at least the inherently harmless idea underlying these sorts of programs […]
Read more →
Posted by Siren on September 13, 2015
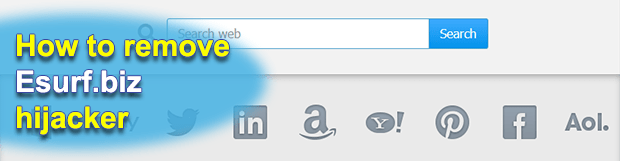
Homepage hijackers like Esurf.biz might appear to be primitive instances of malware at the first blush, but this is nothing but a misperception given the hurdles that the victims run into when trying to remove those culprits. In case of this kind of assault, the web browsers keep resolving the value that the user never […]
Read more →
Posted by Siren on August 14, 2015
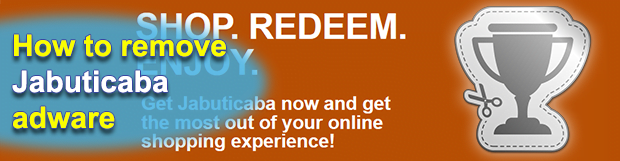
The feature set of Jabuticaba application is a two-edged sword. On the one hand, it provides coupons for various products on the Internet and also allows collecting points for further purchases. On the other, it acts too intrusively when running on a computer and often installs through no consent on the customer’s end. This article […]
Read more →
Posted by Siren on August 10, 2015
With its main focus on enabling users to take screenshots easily, the DownShotFree Toolbar and supporting application accommodate features that not everyone will enjoy. The installation of this package isn’t always an announced event, so the user’s approval isn’t mandatory. What additionally fans the flames is the program’s meddling with one’s homepage and search settings. […]
Read more →
Posted by Siren on August 2, 2015
Whoever might question the reliability and safety of the Strongvault application has got grounds for incredulity. The tool does actually feature online backup of its clients’ data without charging any fees, but a lot of users have been reporting serious system issues and difficulties getting rid of it. Internet activity tracking and ads serving are […]
Read more →
Page 28 of 36 «...10202627282930...»