Youthful Exploits of an Early ISP. Part 2

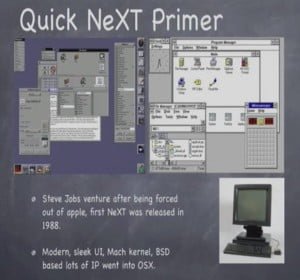 Kevin Nassery: The NeXT stuff was really cool for me to see because it was probably the first UNIX system I had shell on, and this was the first time we were exposed to UNIX. And it was kind of eccentric and cool. Here I put up just a picture side by side of the Windows comparative at the same time – this was, like, 1993-1994, you know, Windows for workgroups, 3.1.1, and a lot of people were running 3.1 – compared to the next graphical interface which actually wasn’t X Windows based, it was a proprietary interface; but next to something that Steve Jobs started after he got forced out of Apple; so if you can imagine the iPhone esthetic and everything being brought into commercial-class UNIX workstations – that’s pretty much what NeXT was. It had a really modern, sleek UI.
Kevin Nassery: The NeXT stuff was really cool for me to see because it was probably the first UNIX system I had shell on, and this was the first time we were exposed to UNIX. And it was kind of eccentric and cool. Here I put up just a picture side by side of the Windows comparative at the same time – this was, like, 1993-1994, you know, Windows for workgroups, 3.1.1, and a lot of people were running 3.1 – compared to the next graphical interface which actually wasn’t X Windows based, it was a proprietary interface; but next to something that Steve Jobs started after he got forced out of Apple; so if you can imagine the iPhone esthetic and everything being brought into commercial-class UNIX workstations – that’s pretty much what NeXT was. It had a really modern, sleek UI.
The thing that was kind of jaw-dropping for me is when I saw the graphical disk partitioner, because disk partitioning at the time in DOS or UNIX or anything else was always, like, fire up fdisk, manage these archaic tables and stuff like that. And here you get the disk represented as a pie chart, and you could kind of slide and whatever you wanted. It was pretty cool, if not pretty useless because we don’t have that today. But you had a lot of neat things.
Probably the biggest pain that I remember about the interface was that you actually had no really great browser candidate. OmniWeb was available, and that’s actually made by the same people that make OmniGraffle today. But there weren’t a lot of great browsers, so what they had – and you couldn’t even compile it to run on NeXT – but what they did use was a commercial piece of software that added X Windows Server capability to NeXT, called CoXIST so that they could render some of that stuff off of the SGI or other systems and remote-display it on. I guess I should say also it’s kind of weird for me to think, back then all these core UNIX systems were simultaneously being used as workstations for the admins and everything like that. There was no separation of duty between where you sat and the server supportability.
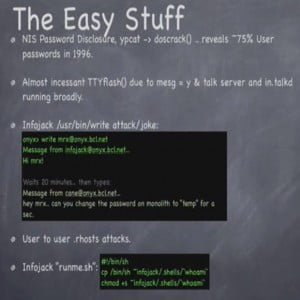 So, kind of the easy stuff; and as a younger person at the time getting into computers and UNIX and starting to walk the line of stuff that felt safe to do or was at least simple enough to do – the password trust was using YP or NIS, basically password sharing, so you could get a copy of the shadow file by compiling ypcat and then running it. And actually at the time the best cracking software I had or knew about for available for DOS 6.2, so I would use Trumpet Winsock, dial-in, do this stuff, download the file, then reboot back into DOS – you know, exit Windows, get into DOS – and run this cracking program overnight until my Dad would tell me that he had to do some work or something; and there was no way to pause it and stuff. About 75% of the user passwords were dictionary crackable even on that DX2-66 with that 4-5 MB password file.
So, kind of the easy stuff; and as a younger person at the time getting into computers and UNIX and starting to walk the line of stuff that felt safe to do or was at least simple enough to do – the password trust was using YP or NIS, basically password sharing, so you could get a copy of the shadow file by compiling ypcat and then running it. And actually at the time the best cracking software I had or knew about for available for DOS 6.2, so I would use Trumpet Winsock, dial-in, do this stuff, download the file, then reboot back into DOS – you know, exit Windows, get into DOS – and run this cracking program overnight until my Dad would tell me that he had to do some work or something; and there was no way to pause it and stuff. About 75% of the user passwords were dictionary crackable even on that DX2-66 with that 4-5 MB password file.
Games we played with each other in just terms of annoyance – the talkd servers were pretty universally deployed, where if you knew what the hostname was you could look and see who’s logged in using the Finger protocol; and if you wanted to send a chat request to them – we had this network chat in talkd thing – the secret was that all of the terminals were really sensitive to binary character sets getting sent to them (and this might happen to people even today if you cat the wrong file or something like that, you’ll see your terminal character set get screwed up). So we used to use that by connecting to those systems using the tool called Flash.C. It would connect to those systems and put those binary characters into the user ID request field of the submitting user, and send it to the target user, and it would just screw up people’s terminals.
One of our buddies did this thing – I don’t know how many people are familiar with UNIX rights; we don’t use it that much anymore, but still today on a UNIX system if you are a root user or whatever, you can send something to the terminal. This guy sent a message to our friend who was working with staff, and then just waited. So that way he had that line open to them and he waited for a long time and then just typed and sent the data as a forgery of what the message request would look like from cane, and then told them to change the root password. It didn’t work but it was pretty clever, and that was a pretty big gap in right. I probably haven’t received a legitimate right message for 12 or 13 years.
Still, a really big time for IP level trust with .rhosts files; this was pre-Mitnick, where Mitnick actually used that IP sequencing attack and kind of popularized and notarized that thing. So there was a lot of user-to-user trust mechanism set up where you could use rlogin and configure it so that you could jump between servers on your own account pretty easily. And occasionally we’d gain access to something and then use their rlogin trust just to expand our network of hosts.
This guy also had a pretty cute thing because there was a lot of snooping in people’s shell accounts and things like that at the time. He just left a file in his home directory called ‘runme’, and it would wait until non-expecting other shell account users would snoop in his home directory. And when they ran it, it would make a copy of bin/bash, set it to SUID then and submit it to a file, that list of shells that he kept. So, once people were kind of snooping around – if you’re stupid enough to run this ‘runme’ script, he would have your shell access. And I think he said at one point he got around 10-15 shells. I’ll turn it over to Dop.
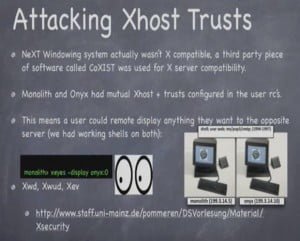 Mike “Dop” Dopheide: So, Kevin talked about the NeXT Windowing system and how it wasn’t compatible with X Windows stuff, the admins would get used to displaying that scape off of other systems. Back then they were still using Xhost and they got really complacent in using Xhost +, things like that. And I guess in the 1996-1997 time frame, there were these three commands – Xwd, Xwud, and Xev. The first two would dump the screen – just your X display, whatever it was that was being seen by whoever was using X – to an image file, and its companion would then uncompress that or whatever and display it to you.
Mike “Dop” Dopheide: So, Kevin talked about the NeXT Windowing system and how it wasn’t compatible with X Windows stuff, the admins would get used to displaying that scape off of other systems. Back then they were still using Xhost and they got really complacent in using Xhost +, things like that. And I guess in the 1996-1997 time frame, there were these three commands – Xwd, Xwud, and Xev. The first two would dump the screen – just your X display, whatever it was that was being seen by whoever was using X – to an image file, and its companion would then uncompress that or whatever and display it to you.
So, whatever was on the shell, whatever images they were looking at, news groups they were reading – it was all available to us. And the Xev was even more interesting because it would just intercept any accidents between the X server and the X client, which means we could then get keystrokes for any of their X terminals. This is how we captured a lot of the root passwords and stuff that were floating around in the network, just because of simple Xhost +. And then we’d obviously just set Xhost + in other people’s shells at that point.
Kevin Nassery: Yeah, it was just that they set Xhost + for the entire world to remote display stuff, but there was a permanent trust established between Monolith and Onyx, where each one (the display) mutually trusted the other one. We had shell accounts on both, so you could use that to remote display an event capture thing to the other system and gather those things – just Xev -display the remote host, and exploiting that trust.
Mike “Dop” Dopheide: That stuff is still available, I included the link to it in case you want to break your stuff and see if anyone finds out. But it was pretty fun. I still use some of those root passwords because there’s a small group of us, like me and maniac, and we know what those passwords are so we can set those passwords for each other and say: “Hey, use Monolith password to log into this.” And then we can communicate that.
Kevin Nassery: This stuff kind of went away due to practical reasons once SSH came and had the automated XOFF forwarding stuff to do it securely. XOFF by hand was a bit of a pain though to configure and do it the right way. That’s probably why you don’t see as much of this even where people are doing full X displays running X servers. You know, the XOFF is so easy to use, and it made it easy to say: “Give that remote system XAuthority.”
Mike “Dop” Dopheide: Yeah, and it was a big problem back then because people didn’t understand all of this, so people would say: “Well, how do I get my Netscape to display over here so I can do my homework?” If you tried to google it – or I guess you’d “lycos” back then – the answer all over the web would be “Xhost +, everything works.”
Kevin Nassery: And this of course is also susceptible to IP sequencing attacks in terms of IP spoofing because you are just trusting by IP host or authenticating things.
Also Read:
Posted in: KnowledgeBase
Leave a Comment (0) ↓