TeslaCrypt 3.0 – decrypt files and remove the ransomware

The ransom trojan dubbed TeslaCrypt has substantially evolved over the course of almost a year that it has been around. The original variant was detected in late February 2015, and the security industry is now dealing with the 3rd generation of this infection. The tweaks made to its code and operation ever since include the scope of targeted users, the file distortion mechanism utilized, and a number of external representation changes.
Table of Contents
The gist of TeslaCrypt
The initial impression that this sample is going a well-trodden path of lookalike ransomware threats is somewhat erroneous. The infection proved to pioneer in several areas of extortion-based cybercrime. It started off with going after gamers as its first build would spot and encrypt data like game mods and saved video games on contaminated computers. Furthermore, its code wasn’t borrowed from any counterparts and was developed independently. Its latest iteration, TeslaCrypt 3.0, features an advanced encryption key exchange algorithm, which makes it much more problematic for security analysts to come up with a decrypt tool.
TeslaCrypt may be executed on a Windows computer after one of the following events: the user opens a payload-carrying attachment to a phishing email, or they visit a compromised website hosting an exploit kit such as Angler or Neutrino. Either way, the code injection process is hard to notice with the naked eye, and given the complex antivirus evasion techniques it won’t be blocked by one’s installed security solution most of the time. Having left the contamination stage behind, the ransomware scans the hard drive, USB memory sticks if plugged in, network shares and Dropbox mappings. It traverses the above as long as they are drive letters. This scan is aimed at locating the files whose extensions the virus authors hard-coded in the malicious routine. There are about 200 formats that are at risk, including popular ones like Microsoft Office documents, multimedia files and images.
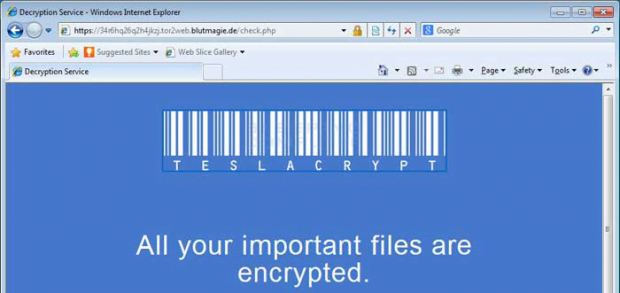
On the next phase of the attack, TeslaCrypt 3.0 encodes the objects found during the scan using AES-256 standard, as opposed to asymmetric RSA algorithm used by the bulk of ransom trojans on the loose. The malware then launches an application that informs the victim about what happened and instructs them on further action to recover the locked data. This app’s interface says:
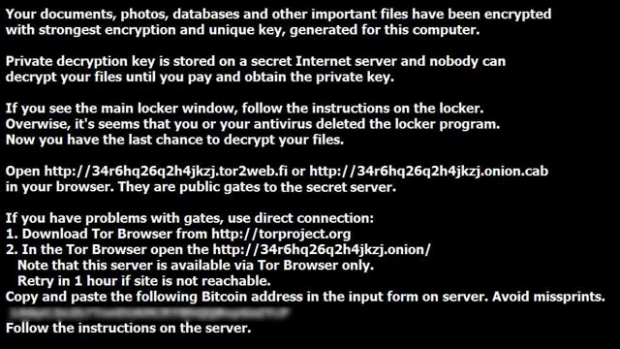
All your important files are encrypted!
Your personal files (including those on the network disks, USB, etc.) have been encrypted: photos, videos, documents, etc. Click “Show files” button to view a complete list of encrypted files, and you can personally verify this.
Encryption was made using a unique strongest RSA-2048 public key generated for this computer. To decrypt files you need to acquire the private key.
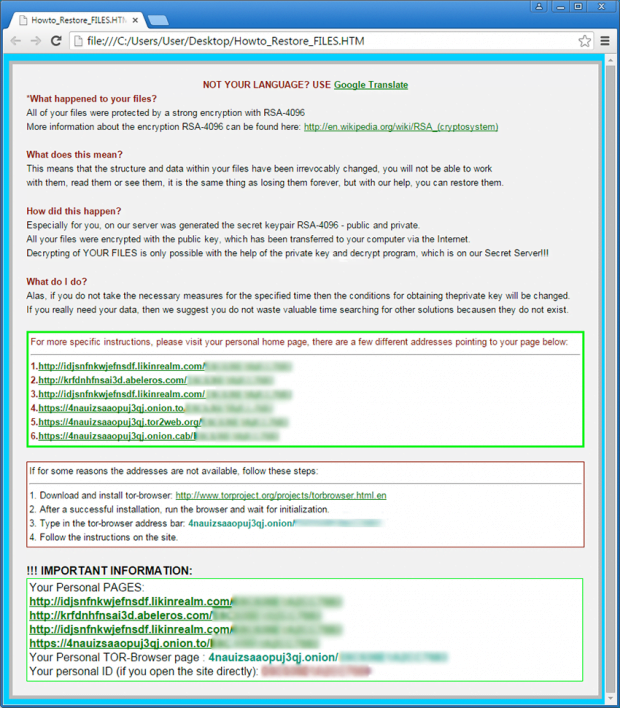
The only copy of the private key, which will allow you to decrypt your files, is located on a secret TOR server in the Internet; the server will eliminate the key after a time period specified in this window. Once this has been done, nobody will ever be able to restore files…In order to decrypt files press button to open your personal page and follow the instruction.
In case of “File decryption button” malfunction use one of public gates:
[URL 1]
[URL 2]Use your Bitcoin address to enter the site.
If both buttons and reserve gates are not opening, please follow these steps:
You must install TOR browser www.torproject.org/projects/torbrowser.html.en. After installation, run the browser and enter address [random].onion. Follow the instructions on the web-site. We remind you that the sooner you do so, the more chances are left to recover the files.There is no other way to restore your files except for making the payment. Any attempt to remove or corrupt this software will result in immediate elimination of the private key by the server.
TeslaCrypt also replaces the current desktop wallpaper to a similar warning notification. Also, it creates ransom instruction documents inside every folder that contains encrypted data. The names of these files vary, depending on the version of the infection. They might the as follows: Howto_Restore_FILES.HTM (Howto_Restore_FILES.BMP, Howto_Restore_FILES.TXT), HELP_TO_DECRYPT_YOUR_FILES.TXT (HELP_TO_DECRYPT_YOUR_FILES.BMP), or HELP_RESTORE_FILES.TXT (HELP_RESTORE_FILES.BMP).
In addition to encrypting the victim’s personal data, the ransomware adds new extensions to the files. The specific string appended to the locked objects depends on the version of the malware. Here is the complete list of these extensions: .ecc, .exx, .ezz, .xyz, .aaa, .ccc, .zzz, .abc, .vvv, .xxx, .ttt, .micro. Therefore, a random file named ‘photo.jpg’ gets transformed to ‘photo.jpg.ttt’, where the final array is variable. Knowing the complemented extension is also important in terms of decryption possibility – experts have created a tool that restores some of these. Read the rest of this article to learn which ones are covered.
In order to reinstate the defiantly encrypted information, the victim is required to follow the ransom directions and pay about 500 USD. The payment should be submitted in Bitcoin to an address which is unique for every infected person.
What to do if you get hit by TeslaCrypt 3.0?
It matters a lot at which point of the compromise you realize that the infection in on board. Anyway, as soon as you notice it be sure to unplug the network connection and shut down your PC right away. Another tip is to abstain from deleting any files until things have been sorted out. If you have a fresh backup of your data offline or in the cloud, then run a reliable antimalware solution and remove TeslaCrypt from your computer before you get down to restoring from backup. In the unfortunate event the attack has gone all the way, look up the file extension added to frozen files and check whether the decrypt solution called TeslaDecoder can help – this information is provided in one of the sections below.
TeslaCrypt Decryption Service site
This ransom trojan recommends its victims to visit a TOR gateway designed to process Bitcoin payments. This page, titled Decryption Service and linked-to in the ransom alerts, contains detailed information on the specific files that were encrypted on the PC and instructs the user on steps that need to be followed for recovery. As it has been mentioned above, the criminals ask for a Bitcoin amount equivalent to about 500 USD per machine. The site also allows the user to get one file restored without payment and contains support features that can be used if something goes wrong on the bad guys’ end.
Will the files be decrypted if you pay the ransom?
The rule of thumb is to refrain from doing the buyout unless there are no other options. If you do end up paying, be advised the process may turn out lengthy as the payment must be verified by the scammers. In return, they will issue the key pair to be used for decryption via the ransomware’s user interface. TeslaCrypt 3.0 authors reportedly provide the prerequisites for file recovery if they receive the ransom, but the idea of supporting the extortionists financially is definitely a disgusting one.
Known versions of TeslaCrypt and the corresponding file extensions
Peruse this subsection to find out whether the ad-hoc decryption tool can get around the crypto implementation and thus recover the locked files.
Version 1: adds .ecc extension to files. The data file and log file are AppData\key.dat and AppData\log.html, respectively. Decryption can be performed with TeslaDecoder.
Version 2: uses .ecc and .ezz extensions. Location of the data and log files is identical to the above iteration. It also creates the following registry key: HKCU\Software\Microsoft\Windows\CurrentVersion\SET. Can be decrypted.
Version 3: characterized by .ezz and .exx file extensions. Data file location is LocalAppData\storage.bin, and the log file is LocalAppData\log.html. The registry entry added is HKCU\Software\Microsoft\Windows\CurrentVersion\Settings\storage. Decryption tool is applicable.
Version 4: appends encrypted files with .aaa, .abc, .ccc, .xyz, .zzz. Creates a random-named registry value under HKCU\Software. No decryption capability unless the private key is available.
Version 5: adds .ccc file extension. This one doesn’t create a data file or log file. Not possible to decrypt without the private key.
Version 6: complements files with .vvv extension. The expert-tailored decrypt tool does not work unless the victim can provide the private key.
Version 7: filenames are appended with .ttt, .xxx or .micro suffix. The decoder cannot restore data without the private key.
TeslaCrypt 3.0 file automatic removal
Extermination of this ransomware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download TeslaCrypt 3.0 ransomware remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the file and related infections removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the plague proper. Now you are facing a bigger challenge – try and get your data back.
Decrypt with TeslaDecoder
Whether or not the encoded information can be decrypted depends on the TeslaCrypt version you have confronted. In case the ransomware has added .exx, .ecc or .ezz string to the filenames, a remarkable tool called TeslaDecoder can be leveraged to recover the data. This utility was developed by a security researcher nicknamed BloodDolly. It automatically finds the private key if it’s on the workstation and then uses this key in order to implement the decryption. To get the job done, follow the steps below:
1. Download TeslaDecoder, extract the ZIP file and run the application

2. The program will let you know if it succeeds in finding the decryption key. If it fails, try loading the file named storage.bin or key.dat manually by means of the Load data file button
3. Use the Decrypt Folder feature to perform test recovery of several files copied to a standalone folder. If it goes well, click the Decrypt All button to recover the totality of your locked files.
Methods to restore files encrypted by TeslaCrypt 3.0 file
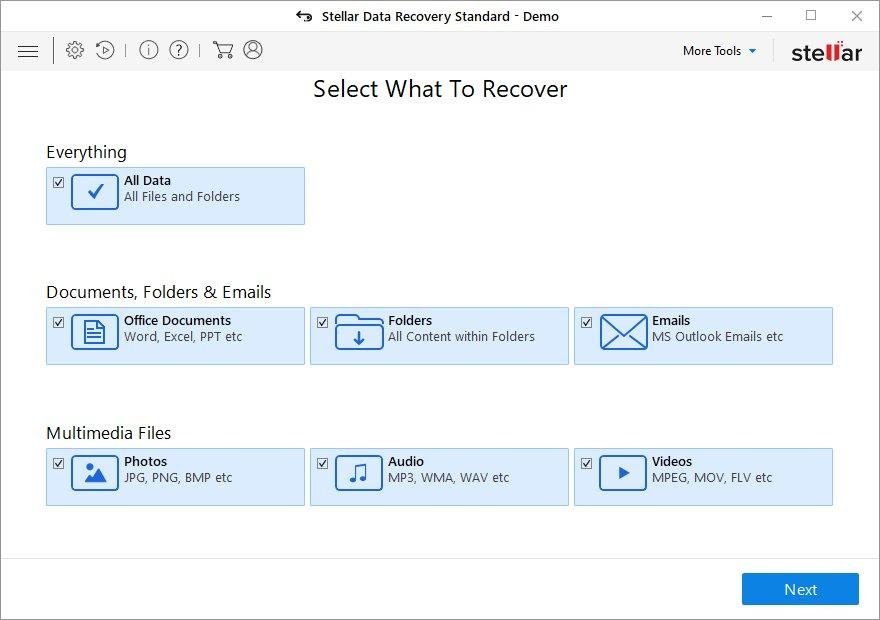
Workaround 1: Use file recovery software
It’s important to know that the TeslaCrypt 3.0 file creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Stellar Data Recovery for this purpose. The newest version of the file under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Download Stellar Data Recovery Professional
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
-
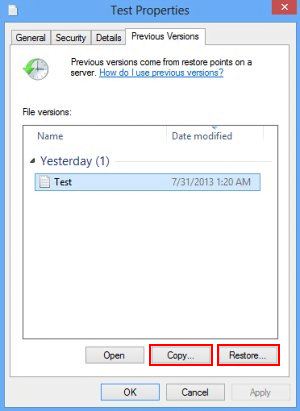
Use the Previous Versions feature
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.

-
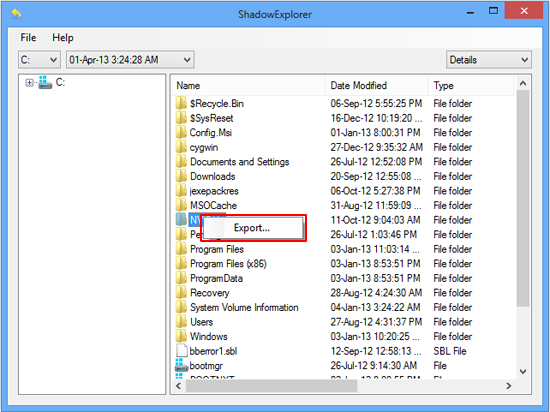
Apply Shadow Explorer tool
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.

Prevention recommendations
TeslaCrypt is one of the most viable ransomware threats to date. Rapid evolution of the built-in features makes it hard for the security industry to catch up with countermeasures. The criminals in charge have been busy addressing the weak links in the trojan’s code as a response to occasional disclosures of these vulnerabilities by antimalware labs and enthusiasts. Newer variants of this crypto infection are using improved key exchange principles so that the use of TeslaDecoder is to no avail. Given this continuous progress of the malady, methods to prevent the attack come to the fore.
The most important tip is to store a secure backup of your files. Thankfully, there are quite a few inexpensive or even free cloud services at your disposal to upload data. Offline backup on external media isn’t as convenient, but it’s a good way to protect your information as well. To thwart the code injection proper, do not open attachments in fishy emails as they pose a widespread distribution model when it comes to ransomware. Also, keep your software up to date so as to get potential vulnerabilities patched and hence avoid contamination via exploit kits. And finally, use a trustworthy security suite that features behavioral analysis.
Verify whether TeslaCrypt 3.0 file has been completely removed
Again, ransomware removal alone does not lead to the decryption of your personal files. The data restore methods highlighted above may or may not do the trick, but the file itself does not belong inside your computer. Incidentally, it often comes with other file, which is why it definitely makes sense to repeatedly scan the system with automatic security software in order to make sure no harmful remnants of this file and associated threats are left inside Windows Registry and other locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓