TeslaCrypt releases Master Decryption Key

TeslaCrypt, one of the most potent ransomware stains operating since early 2015, has gone extinct. That’s certainly some good news for those who fell victim to it and the thousands of users who could yet be compromised over these sophisticated attacks. TeslaCrypt originally kicked off as a crypto malware campaign that targeted computer gamers but evolved into a threat encrypting a vast range of its victims’ personal data stored on hard drives as well as mapped network shares and Dropbox mappings.
This ransom Trojan would slither into Windows computers through the aid of exploit kits, including Neutrino and Angler, and via phishing emails with booby-trapped attachments. Having encrypted one’s files, it would append filenames with one of the following extensions: .ecc, .ezz, .exx, .aaa, .abc, .ccc, .xyz, .zzz, .vvv, .ttt, .xxx, or .micro.
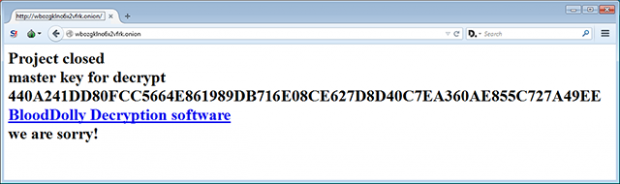
As of May 18, the malefactors behind this ransomware announced project closure. The Tor site that was once the decrypt service came to display a message that read:
“Project closed. Master Key for decrypt 440A241DD80FCC5664E861989DB716E08CE627D8D40C7EA360AE855C727A49EE.
We are sorry!”
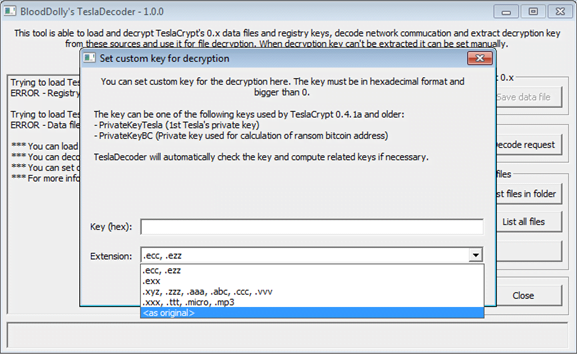
Later on, the perpetrators modified their message and included a download link to TeslaDecoder, an automated recovery tool developed by a security researcher who goes by the handle BloodDooly.
Now that the universal decryption key has been released, all it takes the victims to restore their data is download BloodDolly’s TeslaDecoder v1.0.0, launch the tool, select the Set key feature, use drop-down menu to select the extension that the ransomware added to encrypted files, click Set key and select Decrypt all. This will automatically recover all files locked by TeslaCrypt.
According to a preliminary verdict of malware watchers, the operators of TeslaCrypt haven’t dropped the ransomware business altogether. Instead, they reconfigured their malicious infrastructure and switched to a new campaign dubbed CryptXXX, which harnesses the Angler exploit kit to infect computers, encrypts data with RSA-4096 cryptosystem and creates ransom notes titled de_crypt_readme.html (.txt, .bmp). Whereas file-encrypting infections are constantly changing and merging, the best precaution remains the same – file backups still pose the number one strategy to mitigate the damage.
Posted in: News
Leave a Comment (0) ↓