How to remove Onion ransomware virus and decrypt .onion files
The worst part about the average ransomware attack is that the victim gets locked out of their personal data. While it’s usually not problematic to get rid of the malicious code itself, important information stays inaccessible until the infected user redeems it by paying up. The newest variant of the Dharma ransomware species follows this particular path, encrypting files and appending the .onion extension to them.
Table of Contents
What is the Onion ransomware?
As mentioned above, the .onion file extension is an indicator of compromise accompanying the latest Dharma ransomware operation. This family of crypto viruses has got a heck of a background, with ups and downs as well as unexpected dumps of master decryption keys that occurred two times over the past six months. Regardless of the edition, this vicious digital contagion has been consistently applying a robust cryptographic mechanism that thwarts decryption. In other words, when confronted with it victims are in trouble and run the risk of losing all personal archives, documents, images, databases, videos and other types of data.
The Onion ransomware, which is the way it is referred to, affects files in several ways. First and foremost, it employs a combo of RSA and AES ciphers to make it impossible for the plagued user to access the information. Neither opening nor editing the encoded entries is feasible as a result of such an impact. Secondly, the Trojan also tweaks the outer look of targeted files. It takes the original filename and suffixes them with a string according to the following pattern: id-[victim identifier].[attacker’s email address].onion. For you to get a better idea of the outcome, here’s a sample manifestation of an arbitrary data entry hit by the pest: Q1_Report.pdf.id-6A563F28.[volantem_diem@aol.com].onion. The ID is unique for every user, and the email varies from campaign to campaign. A few other such addresses that came into researchers’ spotlight include volantem_diem@zoho.eu, felix_dies@aol.com and nicecrypt@india.com.
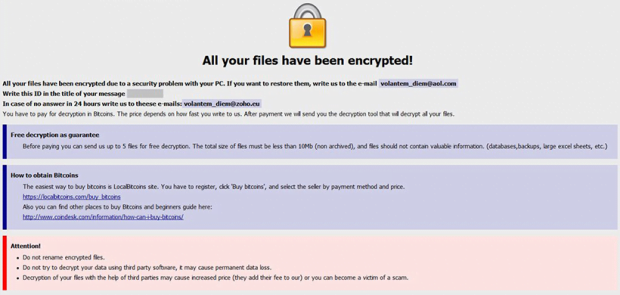
To let the victim know what exactly is going on and how to go about the predicament, the Onion ransomware drops one or several help files onto the desktop and inside folders encompassing locked data. This ransom note is named Info.hta, with a likely additional plaintext counterpart being Readme.txt. The warning message in both goes, “All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail volantem_diem@aol.com,” where the address corresponds to the specific extortion sub-campaign. The user is supposed to write their personal ID in the title of the message, send it and wait for a response with more detailed steps. In a nutshell, the decryption boils down to submitting a ransom of 0.5-1 BTC to the crooks’ Bitcoin wallet. After this payment has been confirmed, the threat actors will supposedly provide the decryption tool. They also claim to be able to restore up to five not-very-important files prior to the payment as long as the victim asks them to.
The .onion file extension virus is distributed via malicious spam. A botnet involved in this process generates bulk emails with contagious files attached to them. These attachments are usually ZIP archives with a JavaScript file inside, which in its turn fires up a PowerShell command to execute the infection on a recipient’s computer. So watch out for fishy emails that pretend to be invoices, ISP complaints, utility bills, job offers and similar arresting subjects – never open the files they carry. The part below includes some more ransomware prevention advice and provides the entirety of troubleshooting techniques in case this specific Trojan is already inside and has turned files into inaccessible .onion entries.
Onion ransomware automatic removal
Extermination of this ransomware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download Onion ransomware remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the ransomware and related infections removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the plague proper. Now you are facing a bigger challenge – try and get your data back.
Methods to restore files encrypted by Onion ransomware
Workaround 1: Use file recovery software
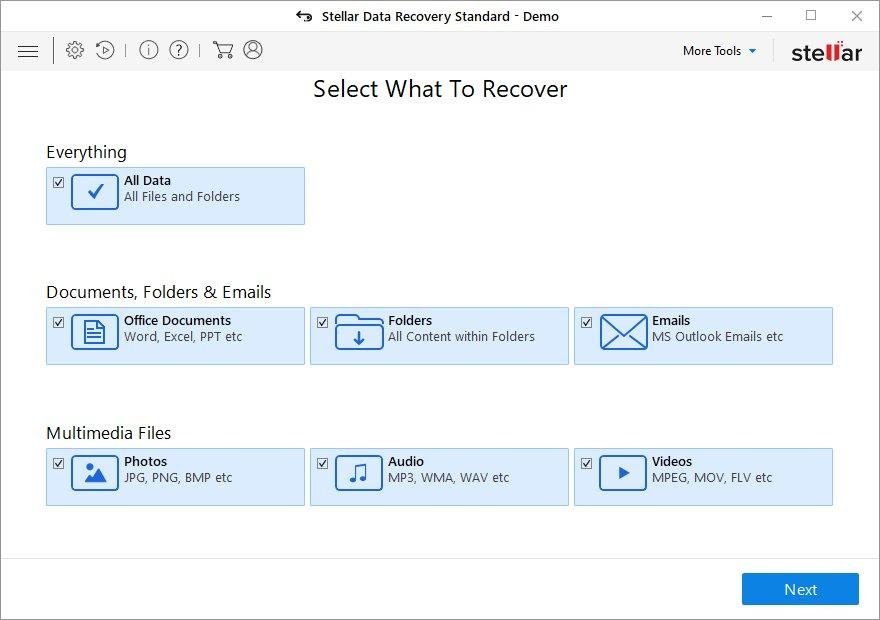
It’s important to know that the Onion ransomware creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Stellar Data Recovery for this purpose. The newest version of the ransomware under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Download Stellar Data Recovery Professional
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
-
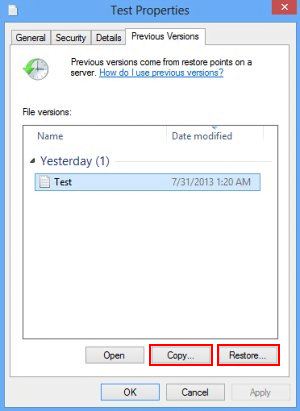
Use the Previous Versions feature
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.

-
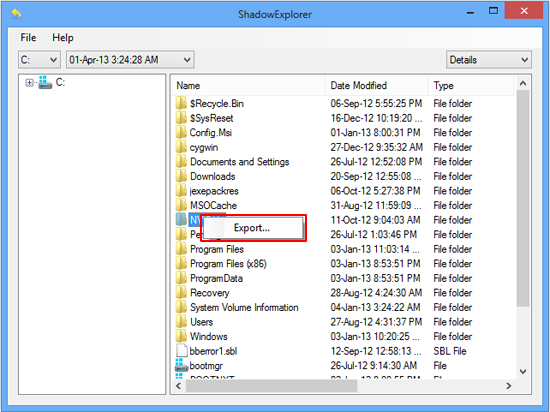
Apply Shadow Explorer tool
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.

Verify whether Onion ransomware has been completely removed
Again, ransomware removal alone does not lead to the decryption of your personal files. The data restore methods highlighted above may or may not do the trick, but the ransomware itself does not belong inside your computer. Incidentally, it often comes with other ransomware, which is why it definitely makes sense to repeatedly scan the system with automatic security software in order to make sure no harmful remnants of this ransomware and associated threats are left inside Windows Registry and other locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓