Dharma ransomware: decrypt .dharma and [crannbest@foxmail.com].wallet files
![Dharma ransomware: decrypt .dharma and [crannbest@foxmail.com].wallet files](https://soft2secure.com/wp-content/uploads/remove-dharma-ransomware.png)
The ransomware plague is on the rise these days. File-encrypting viruses come and go, but new ones take over to prop the inheritance. One such family is probably the most dynamic one to date. Originally referred to as the CrySiS strain, it morphed into Dharma in late fall 2016. Encrypting victims’ data and appending the .dharma, .wallet, or .zzzzz extension to every file, this specimen has become a major cybersecurity concern.
Table of Contents
What is the Dharma ransomware?
Dharma is a conventional denomination of a far-flung ransomware family. As mentioned above, it is a successor of the CrySiS infection that had been terrorizing home users and organizations throughout last year. The predecessors’ story ended with someone releasing master decryption keys so that victims could regain access to their scrambled data. In the case of the Dharma ransomware, a similar thing happened at the beginning of March 2017, but the relief for those infected is only partial. The recently leaked recovery keys only work for the ransomware edition that concatenates the .dharma suffix to encoded files. Meanwhile, there are several more variants, including ones that use the .zzzzz and .wallet extensions instead.
The ransom Trojan in question is characterized by a number of unique attributes accompanying this particular extortion model. First off, the ransomware uses several different extensions namely .dharma, .wallet, and .zzzzz. Perhaps each one is used for a specific sub-campaign of the malware distribution. Secondly, the original filenames do not undergo any sort of tweaking, but they are followed by a certain email address plus one of the above-mentioned suffixes. For example, a file called Photo.jpg will be transformed into Photo.jpg.[crannbest@foxmail.com].dharma or similar. Overall, the list of widespread email addresses used by the virus includes (these strings will appear in square brackets):
- crannbest@foxmail.com
- braker@plague.life
- bitcoin143@india.com
- amagnus@india.com
- base_optimal@india.com
- payforhelp@india.com
- supportforhelp@india.com
- supportforyou@india.com
- opened@india.com
- tombit@india.com
- google_plex@163.com
- mr_lock@mail.com
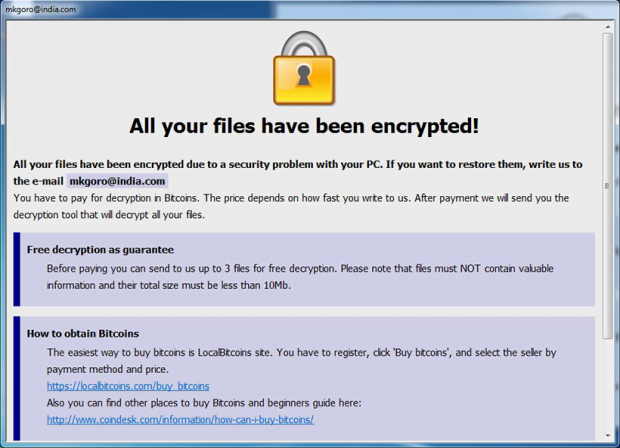
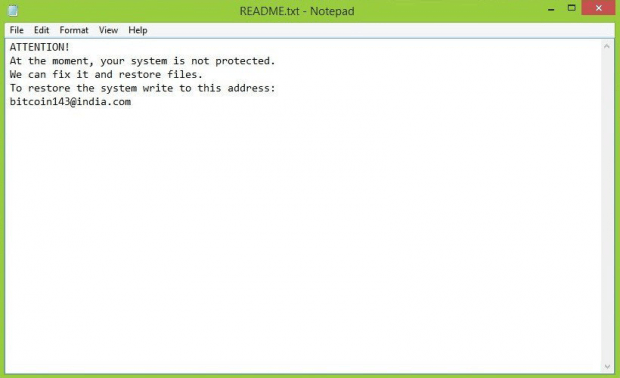
Another indicator of compromise is a combo of ransom notes. The Dharma ransomware creates help files called Info.hta and Readme.txt, which instruct victims regarding decryption steps. The former is an application whose window says, “All your files have been encrypted due to a security problem with your PC,” and urges the victim into contacting the crooks as soon as possible. The latter text file’s contents are fairly concise, reading, “Attention! At the moment, your system is not protected. We can fix it and restore files.” In either case, the recovery process boils down to sending an email to the address indicated in these ransom notes, and then following the instructions received in response to the message.
The size of the ransom may fluctuate from 0.5-2 BTC, although some victims have reported larger fees being requested. It’s unclear how exactly the pricing is formed, so it may be different in every extortion incident. Fortunately, those infected with the .dharma file extension version of this ransomware can get their data decrypted for free. That’s courtesy of antimalware labs that updated their decryption tools to support this particular variant, and owing to a stranger – perhaps one of the cybercriminals – who released the master decryption keys. However, users who are confronted with the .wallet or .zzzzz extension edition of the Dharma virus still have to seek a solution elsewhere. The tips below may help recover some of these files without you having to submit Bitcoins to the online sleazeballs.
Dharma ransomware automatic removal
Extermination of this ransomware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download Dharma ransomware remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the ransomware and related infections removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the plague proper. Now you are facing a bigger challenge – try and get your data back.
Methods to restore files encrypted by Dharma ransomware
Workaround 1: Use file recovery software
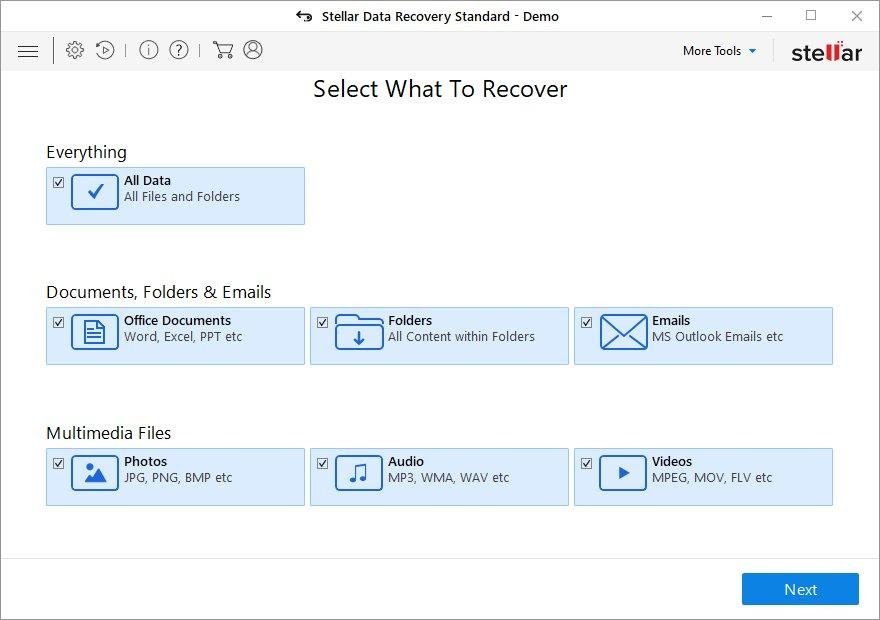
It’s important to know that the Dharma ransomware creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Stellar Data Recovery for this purpose. The newest version of the ransomware under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Download Stellar Data Recovery Professional
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
-
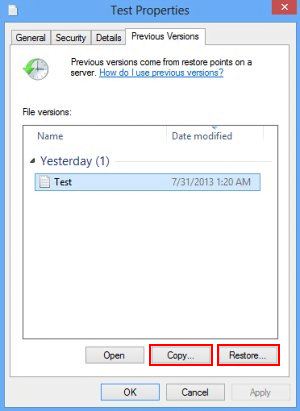
Use the Previous Versions feature
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.

-
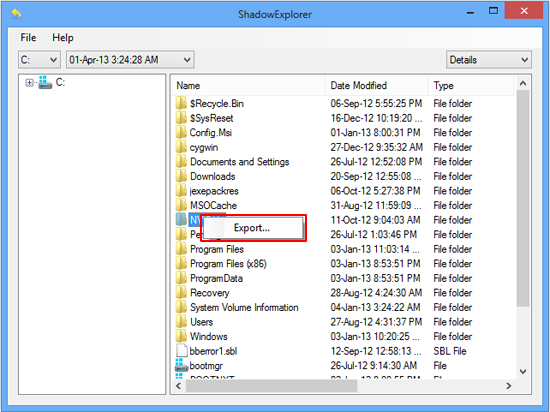
Apply Shadow Explorer tool
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.

Verify whether Dharma ransomware has been completely removed
Again, ransomware removal alone does not lead to the decryption of your personal files. The data restore methods highlighted above may or may not do the trick, but the ransomware itself does not belong inside your computer. Incidentally, it often comes with other ransomware, which is why it definitely makes sense to repeatedly scan the system with automatic security software in order to make sure no harmful remnants of this ransomware and associated threats are left inside Windows Registry and other locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓