.adobe extension ransomware decryptor
There are plenty of perils lurking on the World Wide Web. Compared to most of them, crypto ransomware is in the top of the hierarchy when it comes to the adverse effects. It locks down the victim’s personal data and won’t render it accessible again unless a buyout takes place. The .adobe file extension variant of the Dharma ransomware is one of the competently made samples that deserves a separate sectioning.
Table of Contents
What is the .adobe ransomware?
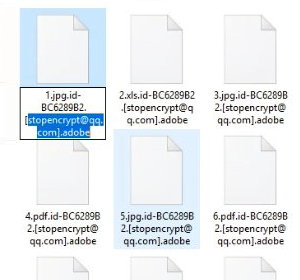
The .adobe file ransomware shouldn’t be confused with the major software vendor everybody knows. It denotes a blackmail virus whose authors simply elected to use the term as the extension appended to the names of hostage files. Whether it’s an attempt to add some strange ambiguity to the attack or just a whim to stand out from the rest, this tactic generally fits the mold of online extortion. While blemishing data items with this suffix, the infection also prepends it with a string that includes the victim’s unique ID plus the adversary’s email address. To demonstrate the outcome, let’s imagine an image named 1.jpg undergoes the malicious crypto impact. It will be ultimately transformed into an entity that looks like this: 1.jpg.id-FB3128B1.[stopencrypt@qq.com].adobe. The plagued user will obviously notice the change while being able to tell which file it is.
Whereas the ID part varies from prey to prey, the email address is another dynamic attribute that can be different than the one in the above example, designating a specific Dharma (CrySiS) ransomware distribution campaign. By the way, this strain is doing the rounds on a RaaS (Ransomware as a Service) basis. It means multiple cybercriminal groups are spreading it independently, only to share the ransom revenue with the proprietors of the bad code. Just like the previous .combo version of the Dharma pest that was in rotation until recently, the .adobe file edition is associated with several hacker syndicates. Consequently, along with the contact string indicated above, the email address can as well be one of the following: decrypt@fros.cc, btcdecripter@qq.com, payransom@qq.com, abido@protonmail.com, avflantuheems1984@aol.com, mercarinotita@qq.com, kush888@cock.li, and manpecamet1974@aol.com. Again, even with a different email string, this is the exact same iteration of the ransomware lineage under scrutiny.
One of the peculiar quirks of the .adobe ransomware is that it is installed onto Windows computers by means of RDP hacking. For those uninitiated, the majority of ransom Trojans arrive at hosts with malspam (malicious spam). Contrary to this technique, the crooks in charge of the baddie being described employ Internet-wide scanning tools to spot remote desktop connections. Then, they try to brute-force the RDP credentials or use the dictionary attack method to guess them. If the compromise succeeds – which is unfortunately the case on a massive scale – the perpetrators manually drop the payload and execute it without any red flags being raised.
| Threat name: | .adobe |
|---|---|
| Decryptor: | Download now |
| Type: | Ransomware |
| Threat family: | Dharma-CrySiS |
| File extension: | .adobe |
| Windows process name: | BulkFileChanger (32bit) |
| Ransom emails: |
|
| Ransom note: | FILES ENCRYPTED.txt |
| Distribution: | Rogue files attached to email messages |
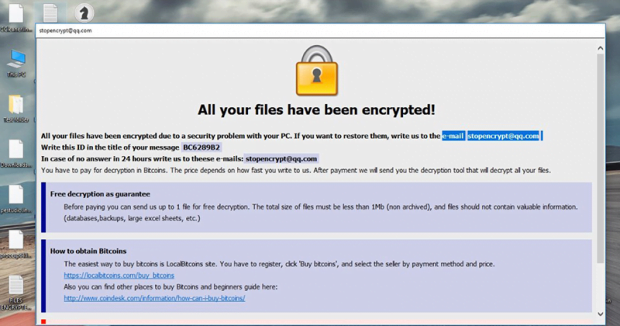
Having slithered its way into a computer, the .adobe ransomware first looks for potentially valuable information on it. It peeks into the hard disk as well as network drives and removable media if it’s currently inserted. Once the list of likely-important files is compiled, the culprit leverages a complex cryptographic mechanism to mutilate them. It utilizes a mix of symmetric AES and asymmetric RSA cipher to do it. After the crypto part is done, the .adobe file virus drops two different editions of so-called ransom notes onto the machine. One is named FILES ENCRYPTED.txt – it ends up on the desktop and inside encrypted directories. The other is an HTML application named Info.hta. This one is displayed automatically and includes more details regarding the criminals’ demands. The title of the latter version matches the email address in filenames, and the contents instruct the user to send a message to the felons.
In response, the malefactors are going to provide the size of the ransom along with the Bitcoin address to send it. The amount tends to be somewhere around 0.1-0.5 BTC, depending on the target. If it’s an enterprise network that’s hit, the sum will be higher. Before rushing into coughing up the ransom, though, victims should take a few important things into account. First off, no one guarantees that the data will be restored in this scenario. Secondly, even if the private decryption key is submitted, the villains behind the .adobe ransomware will get extra funds to move on with their filthy business. So consider using every alternative way imaginable before making the controversial deal. Below are the options worth giving a shot.
.Adobe extension automatic removal
Extermination of this ransomware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download .Adobe ransomware remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the extension and related infections removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the plague proper. Now you are facing a bigger challenge – try and get your data back.
Methods to restore files encrypted by .Adobe extension
Workaround 1: Use file recovery software
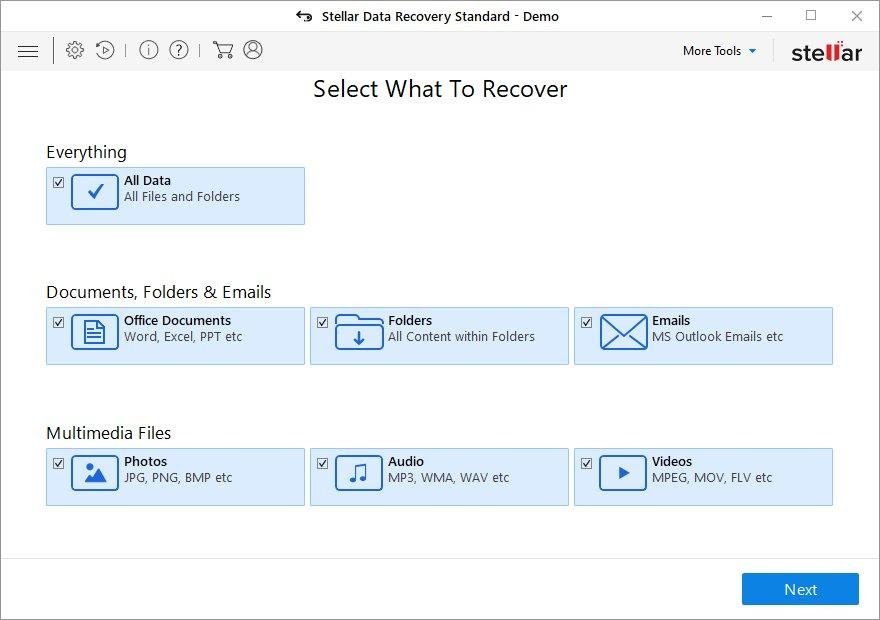
It’s important to know that the .Adobe extension creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Stellar Data Recovery for this purpose. The newest version of the extension under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Download Stellar Data Recovery Professional
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
-
Use the Previous Versions feature
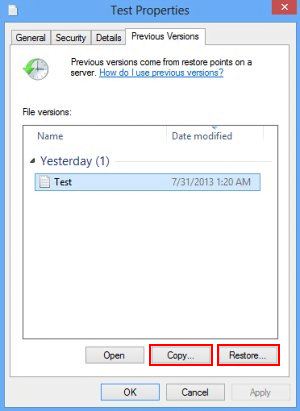
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.

-
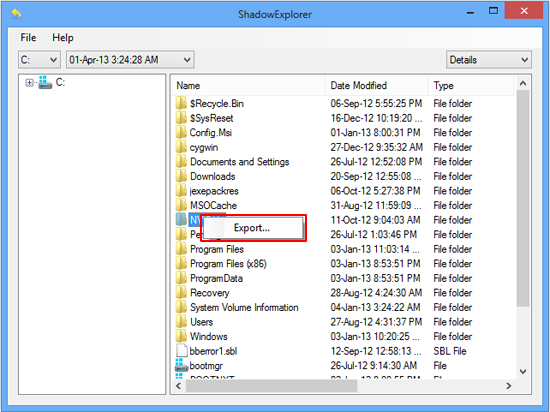
Apply Shadow Explorer tool
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.

Verify whether .Adobe extension has been completely removed
Again, ransomware removal alone does not lead to the decryption of your personal files. The data restore methods highlighted above may or may not do the trick, but the extension itself does not belong inside your computer. Incidentally, it often comes with other extension, which is why it definitely makes sense to repeatedly scan the system with automatic security software in order to make sure no harmful remnants of this extension and associated threats are left inside Windows Registry and other locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓