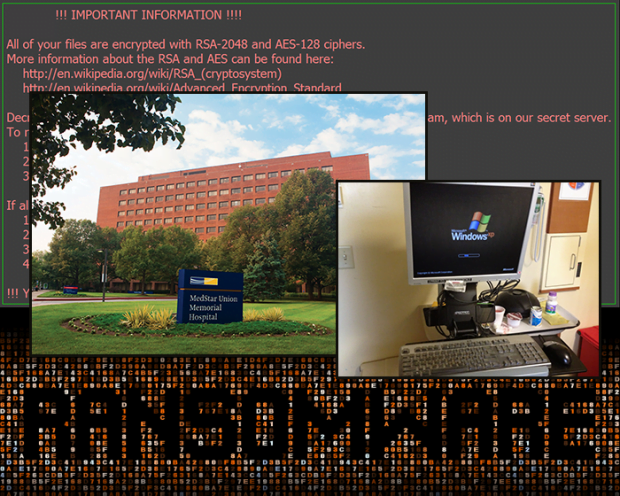
Medstar hospital under ransomware attack

Healthcare providers are being increasingly targeted by cybercriminals. A series of recent attacks against U.S. hospitals have shown just how vulnerable these types of organizations are in the face of ransomware, a type of aggressive computer malware that encrypts data and extorts a ransom for recovery.
Servers of the MedStar healthcare company suffered a compromise in late March, rendering a number of hospitals exposed to a crypto onslaught. In particular, the extortion campaign hit Baltimore’s Union Memorial Hospital and several other Maryland-based MedStar entities. This caused critical operational outages and put patient records at risk. The remote racketeers asked for a total of 45 Bitcoins for decryption of the locked files, which is the equivalent of an astonishing 19,000 USD. The perpetrators tend to use cryptocurrency in their extortion schemes, because ransoms are then extremely hard to track and affiliate with the recipients.
According to cyber investigators’ reports, the infection to blame for this incident is Samsam, also referred to as MSIL/Samas.A. Having scrutinized its code patterns and signature information, the Federal Bureau of Investigation issued a so-called “Flash” message to other players in the healthcare domain, providing them with basic prevention tips and asking for assistance in tackling the problem.
The Samas ransomware primarily targets servers running outdated editions of JBoss, a piece of software heavily used by businesses. Unless patched on time, this application server contains vulnerabilities that allow unimpeded execution of remote code. Interestingly, the crypto virus in question has exploited security loopholes included in the open-source penetration testing toolkit dubbed JexBoss, which is supposed to help pentesters spot weak links in JBoss servers. As per an expert estimate, there are currently more than 2 million networks potentially vulnerable to the same exploit as in the MedStar hack.
The anatomy of the Samas ransomware attack is as follows:
- On the initial stage, the aforementioned JexBoss toolkit is leveraged to hit an organization’s JBoss server.
- The infection furtively installs a SOCKS proxy in order to mask intranet interactions with systems.
- Samas harvests user credentials so that it can propagate further throughout the network. The Hyena network scanner is also used for finding more computers to hit.
- The stealthily collected user credentials are used to inject the ransomware code into the target systems.
Unfortunately, the MedStar incident isn’t the only one involving the healthcare system exposure to MSIL/Samas.A ransomware. The Methodist Hospital based in Henderson, Kentucky suffered an attack a week earlier. The management allegedly ended up paying 17,000 USD in ransoms to restore data and get the infrastructure up and running. Another company, Prime Healthcare Management, Inc., also underwent a similar onslaught lately, which resulted in a shutdown of the systems of two hospitals in California.
It’s a controversial question whether or not such sensitive organizations should pay ransoms under these circumstances, especially when people’s lives are at stake. It’s therefore absolutely critical for entities in the industry to adopt mitigation techniques in order to contain the infection and fully restore server functionality in the worst case scenario. Data backups come to the fore in this context. The above-mentioned Prime compromise demonstrates how important countermeasures are – to their credit, they didn’t pay the ransom and were able to completely recover from the assault.
Ransomware is, obviously, getting more sophisticated in a number of ways. It used to target individual users but is now focusing on companies to make more money with less effort. Since data decryption is hardly feasible across most of these attacks, organizations should invest more in prevention. Security awareness training of the personnel and implementation of robust IT protocols might do the trick of turning a company into a moving target.
Posted in: News
Leave a Comment (0) ↓