Encryption for Everyone. Part 2

Now we are going to talk about asymmetrical encryption. We were talking about symmetrical encryption, where we’re basically just using a password to protect a file. And that’s really great if Alice and Bob know the password and if they can share it. What if Alice and Bob have never met? They’ve never met, somehow they are soulmates, and they want to get this message across, but they’ve never met. So, how can they agree on a password when they don’t know each other?
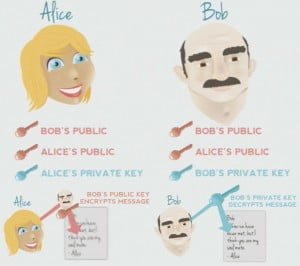
They are going to use something called asymmetrical encryption; the greatest example of this is called PGP. What we do is we make a key, and this key is broken into two pieces. You have a public key and a private key.
The private key would sit on your laptop, whereas the public key would be uploaded to what’s called a key server, which is a public repository for all these people’s keys. So you can go to a key server, search: “I am Bob”, pull down this key, find Alice, pull down her public key.
So, that’s what they do: they trade these keys, and Alice will end up with Bob’s public key. She has her public key and she has her private key. Bob, on the other hand, will have his public key, her public key, and his own private key. Because of this, Alice can encrypt a message using Bob’s public key, since she knows it, and then send it to him. Then when he gets it, because of the way that the keys work, he will decrypt it with his private key that is only accessible to him on his machine.
Again, this is another way of keeping data private, and if you’ve got in the middle of this conversation somehow, she would just be gibberish. Creating keys is probably the first step, and there are a bunch of different programs you can use. For Linux, again, you can use GnuPGP, for MAC – GPGTools, Gpg4win – these are all graphic GUI things. If you don’t like GUIs – I’m not that big of a fan – there’re command line tools on most versions of Linux and UNIX; I think you can just type in: “gpg –gen-key”, and that will walk you through it. It will ask you a series of questions like your name, your email address to do the encryption job.
If you really just want a one stop shop, I recommend using Thunderbird, and there is a plugin called Enigmail; it will handle all of the key creation, it will upload it to the key servers, and it also lets you find your friends and download their keys, and store and manage the keys. It’s really nice, it’s basically a one stop shop for encrypting any kind of email.
Web-based clients are kind of interesting, because they don’t natively support encryption. For instance, Gmail, because of how Google searches your email to put in relevant ads, they do not want you to encrypt it through their web interface, because then they cannot pull out the ads, so they don’t natively support it. However, you can use a program like Thunderbird which will pull down your email, let you compose, let you send, decrypt and encrypt emails. You can also do it manually: if you encrypt a message, copy-paste it in there, and send it, somebody can then pull it out and decrypt it, and vice versa. They just don’t manually support it as well as something like Thunderbird.
Encryption is really all about privacy, and an important aspect of that is what you are putting out there. It really does not do a whole lot of good to encrypt something and to keep something super secret if you are putting the same information in public space. You know, we talk a lot about privacy and privacy concerns, and then at the same time we go and post very intimate, very private things on Facebook and Twitter and social networking. I don’t think those are necessarily bad things, but they are something to consider, especially if you are worried about privacy to the point that you are encrypting stuff, then you have to also think about what you are putting out in the public sphere. A good rule of thumb that I have heard and that I use is if you don’t feel like you could safely write it on the back of a postcard and send it through the mail, then it probably should be encrypted. And if you don’t feel comfortable and safe sending that through the mail, you probably shouldn’t be saying it in an online presence that’s not protected with the same safeguards as encryption. So I think encryption is very good and privacy is very important, and privacy will always work as far as you take it.
And that’s really all I have, I have some links here; the Cryptoparty has more walking-you-through guides. I covered all that stuff very-very briefly because I really want to take some questions if you have them. The Cryptoparty guide has a download guide that will walk you through setting up Enigmail, setting up Thunderbird, setting up these and that sort of things, and the beginner’s guide to encryption is good, just an overall view. I bought two books up there that are very good resources; I think these are the books that you should read…
Any questions?
Question: Why encrypt things?
Answer: In general, why not? That’s more of a philosophical question, you see.
Question: How do you know whether you payment transactions via, for example, PayPal, are properly protected?
Answer: That’s another good point I should bring up. If you are putting your credit card or any information online, you should always look in the corner of your browser, most of them now have a little green box that says HTTPS. Because if you’re sending your credit card and other sensitive information, you need to make sure that’s HTTPS. So if you look in your browser at the corner you will have usually a green box that says HTTPS and lets you now that it is secure and that your information is then encrypted from your computer to their server.
Question: Which encryption method would you advise for those who just want to store things securely on their computers?
Answer: Are you using any kind of disk encryption? TrueCrypt? Yeah, that is really good place to start, especially if you are taking information from, you know, file server or a network somewhere, and putting it on your laptop –we hear stories all the time of somebody losing their laptop or their laptop gets stolen, and it has, you know, two billion Social Security Numbers and credit card numbers; and you think: “Why does that person have all that information on there?” Encryption is a very good place for that because you are preserving the confidentiality of that information.
Question: How good are services like Dropbox for keeping your files safe?
Answer: Things that are on the rise, like DropBox, even Google Docs and that sort of stuff – they don’t natively support encryption at all times, but they will support encrypted files, so if you put an encrypted file up on Google Drive, you might not be able to decrypt it there, but you can download it and decrypt it, and that will work. And that will, you know, maintain your privacy and that sort of thing, but … yeah, I think TrueCrypt is very good for that sort of thing. But it sounds just like being aware that I have these confidential things on my hard drive and I really want to keep them secure and safe; and that you are using TrueCrypt, it sounds like you are doing the right thing.
If there’re no more questions, I’d like to say thanks to Notacon; I would also like to thank Ian Gillespie, the designer at Hurricane Labs, for the great slides. For technical questions and all the LOLcat picture jokes, whatever, that’s my email: dru@hurricanelabs.com. And thank you!
Also Read:
Posted in: News
Leave a Comment (0) ↓