The Concept of VPN – Virtual Private Networking


Eli the Computer Guy
VPN allows computers or entire networks to connect to each other over the Internet securely, so if you have an office in Seattle and it needs to connect to the office in Washington D.C. securely, you would use VPN.
VPN is a client-server architecture, so there are VPN servers and VPN clients, and the software allows the VPN clients to securely connect to VPN servers. This article is going to consider that; it is going to talk about the clients, the servers, the theory – how all this works, and then practical application in the real world.
VPN technology is not nearly as complicated as most people think. There is a lot of theory behind how VPN works that is very complicated, sophisticated, hard to understand, but for you to actually use VPN technology requires basically just to click Connect, enter your password, and it’s done. That is normally as complicated as routines performed by the average user. The stuff behind it is much more complicated.
So, this guide is going to be on VPN, virtual private networking, which allows computers or networks to connect to each other over the Internet.
Virtual Private Networking – How It Works
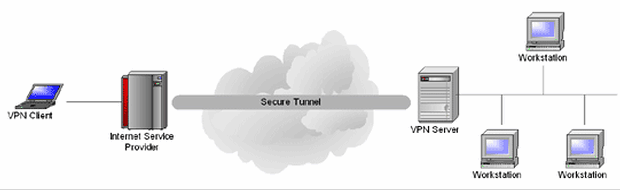
Understanding VPN and how it works requires us to go back and understand how the Internet was created, what was created in the first place. As you probably know, the Internet was created by the US Military so that the Army could try to maintain communications during the time of a massive nuclear attack, so, you know, if you are going to movies and watch about Army getting nuclear bomb going off in New York.
What the military was worried about is not if one military weapon goes off, they were actually concerned about the situation of 20, 30, 100 weapons going off. What would happen if 50 major cities in the U.S. suddenly got vaporized, just no longer existed? So, how would military units communicate with each other? The reason they worried about this is because in the old style of communication, basically with telephone system, all communication went through central hubs. So, if you are in Seattle trying to contact somebody in another city, your telephone communication will go through things called central offices in order to get to the target city.
Well, on a normal bright shiny day this system works fine. The problem is that if one of these central offices is taken off by a nuclear warhead, there is no way to easily reroute this communication to get to the target city. Thus Soviet could bomb us, and if they could destroy a few of these central offices, our communication infrastructure would fall apart. Basically, military units on the West Coast cannot talk to military units on the East Coast, etc., which is a very bad thing.
So, what the military wanted is they wanted a way to communicate that would be self-healing, that would be very easily, very quickly restorable, so that if central hub was destroyed, communication would remain online. That is where they came up with the idea of the Internet. So, the Internet routes all communication through things called routers.
If you’re in the U.S. now, there are tens, probably hundreds, who knows – maybe millions of those routers sitting in the Internet. So, if you are in Seattle using the Internet to connect to somebody in D.C. you go through any number of these routers.
Basically, there is a first router, it passes you to second, the second passes you to third, third to fourth, etc., all the way to D.C. It is so important, because if nuclear bomb goes here and destroys this router, this system will automatically rebuild new communications. So, if first communication path gets destroyed, your communication may go through other routers to D.C. You see, if a huge junction, let us say, ten thousand of these routers are destroyed, you can still communicate with D.C. If hundreds of thousands are destroyed, as long as these are not critical ones, these would all heal themselves and be able to communicate with whoever you are trying to communicate with.
The problem of this from the computer security standpoint is that you have all these routers, and these have data traffic going through them. So, not only router A moves traffic to router B, but all the data actually go through it, files go through it.
If you are a hacker and you somehow are able to get to this router, you can collect all the information that is going through and put it back together and see what people are doing. You know, if pictures are going through this router, you can grab and look at those pictures, as well as you can do the same with confidential info.
This is called Man-in-the-Middle attack. If you are learning about hacking, basically a Man-in-the-Middle attack is when two people are trying to communicate and you get into the middle of their communication stream and you just read everything that is going on by.
When the Internet was created, from the physical security standpoint it was really very good, because if a nuclear bomb went off and half of these routers were destroyed, communication would still exist.
From a computer data security standpoint, it was really very insecure, because if you could get into these routers of these servers, you could look and grab all the information that was going through. That was why they came up with virtual private networking.
Virtual private networking allows you to connect over the Internet securely. So how it does it – well, there are a couple of security tools.
1. Tunneling protocol.
It uses tunneling protocol, which sets up a tunnel as you are trying to connect to e.g. D.C. This tunnel is between you and D.C., covering all the routers that you go through so there is a communication.
2. Encryption
Then, inside the tunnel it (VPN) encrypts the information, so you create a tunnel around the information that you are sending, and then you encrypt all the information in the tunnel to the people you are sending it to. This is important, because if there is a hacker sitting on the router able to see all the traffic going through, the first security means you get around is this tunnel that protects your encrypted data. Well, if there are sophisticated hackers they can penetrate into that tunnel. Even if they infiltrate the tunnel in order to try to grab your data, your data is still encrypted. So, even if they get that data, that does not mean a whole lot to them because it is encrypted.
3. Multiple paths available in case of attack; automatic shutdown and recreation of tunnel
The third thing that makes VPN very secure and very good is that, as mentioned before, there are all these routers, and as you are trying to go to point A, B on the Internet, you may go through any number of these routers to get to where you are going.
Well, the cool part with VPN is that if there is a part of this tunneling protocol and a hacker here tries to penetrate this tunnel, this tunnel will try to detect penetration. So this, say, goes well, but then tunnel suddenly detects somebody trying to penetrate it, so that the tunnel automatically shuts itself down and will recreate itself through another set of routers.
If a hacker tries to penetrate your tunnel in some point, the entire tunnel shuts down, and the tunnel finds another path through the Internet.
If a hacker is at your router, you simply move to another so he is no longer able to grab your information.
That is how VPN works. You get a tunneling protocol that basically is a data tube that runs all the way through the Internet. That tunnel, or tube, tries to protect your data. Then, inside that tube all of your data is being sent, but sent encrypted, so even if somebody manages to penetrate the tunnel, all the data is encrypted. That is, if somebody gets it, it is still not actually disclosed.
Beyond that, as stated above, if somebody penetrates the tunnel, the entire tunnel will drop and try to recreate itself.
This is how VPN works, and we need it, because originally the Internet is not safe in terms of data security.
Also Read:
Posted in: KnowledgeBase
Leave a Comment (0) ↓