T9000 malware: how to detect and remove the virus
A new cyber threat dubbed T9000 is targeting individual users and organizations through tactics featuring a high level of obfuscation. Some researchers consider this backdoor to be a tool meant exclusively for industrial espionage, but the patterns of its propagation prove a much broader attack surface. It was found to surveil victims’ Skype conversations and mine personally identifiable data. Naturally, this malicious routine puts people’s sensitive information at risk.
T9000 backdoor is believed to be a technically enhanced successor of the advanced persistent threat called T5000. The latter was associated with a Chinese cybercriminal ring that chiefly propagated in countries of the Asia-Pacific region and harvested classified governmental data. The new variant is more sophisticated in several ways: it is able to get around detection by the overwhelming majority of commercial antiviruses; it locates confidential files and inconspicuously transmits them to the C2 server; and it gets unrestricted access to the infected person’s video and text communication over Skype. As far as antimalware evasion goes, the refined backdoor is configured to perform recurrent checks for the most popular security suites at different stages of the compromise. If an AV is detected, the infection employs ad hoc techniques to conceal its presence.
The code injection mechanism relies on human error for the most part. The attackers are conducting a phishing campaign, where the would-be victims get incoming emails disguised as something worth opening. These messages have an attachment, which is a contagious RTF document. The innocuous-looking file is stuffed with exploits that the criminals can easily take advantage of. Once this object is loaded, the offenders are able to harness vulnerabilities in Microsoft Office components. As a result, T9000 backdoor bypasses the user’s attention as well as all defensive barriers, taking a firm grip on the machine without any appreciable signs of it.
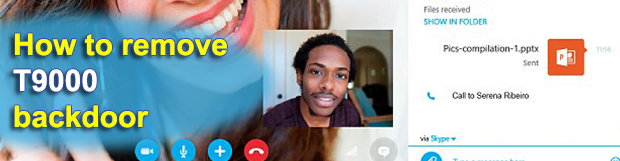
T9000 is primarily an activity tracking entity, so it won’t cause any direct harm to the compromised computer proper. In the meanwhile, hazards to private information stored, generated and processed on the workstation are immense. The backdoor traverses local drives in search of items that may be of potential interest to the criminals, including intellectual property and military secrets. A particularly disturbing characteristic feature of the malware is its capability to watch Skype video calls. Interestingly enough, the infection doesn’t get the corresponding access automatically. Instead, it literally asks for authorization, but does it in a covert fashion. Users get a popup request saying “explorer.exe wants to use Skype”, and in case this access is allowed, the victim’s private conversations may become public knowledge.
Once again, it’s very problematic to detect T9000 backdoor virus, not to mention the removal part. To get the cleanup job done, users should apply software that’s efficient enough to identify this particular threat.
T9000 backdoor automatic removal
The extermination of T9000 malware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped out from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
2. The scan will come up with a list of detected items. Click Fix Threats to get the backdoor removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the infection. However, it might be a good idea to consider ascertaining the backdoor is gone for good.
Posted in: KnowledgeBase
Leave a Comment (0) ↓
