How to remove Shortcut virus from USB PenDrive on PC
A somewhat hackneyed discourse about the polymorphism of malware may seem like a grade school level of perceiving the state of cybersecurity, but this doesn’t contradict its truthfulness in any way. The so-called Shortcut virus, also referred to as the USB flash drive virus, fully demonstrates that PC infections are all adware, banking trojans or ransomware.
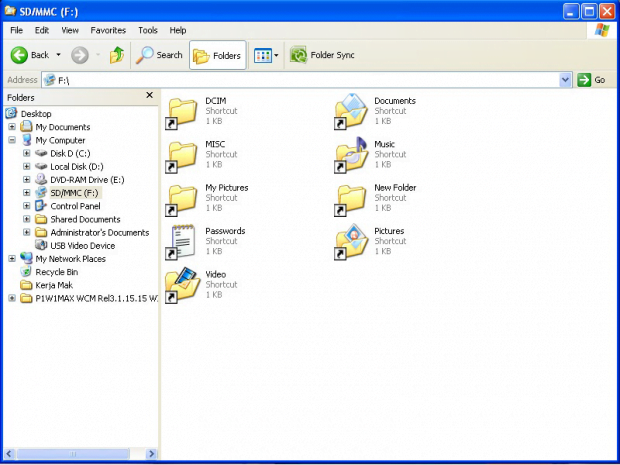
How about the quandary where folders and files on a USB pen drive suddenly turn into namesake shortcuts? Or even worse, what if the representation of data components stored in some directories of the hard drive undergoes a similar tweaking as well? This sure sounds like quite a mishap. An issue like that has got a name. The Shortcut virus, which has been a moderately widespread infection for over a year at this point, affects the file display mode so that the victim’s information becomes inaccessible. Every folder hit by this malware becomes 1 KB large and won’t open when double-clicked. The “Open with…” feature available in the context menu won’t do the trick, because none of the alternative software can render the respective contents in human-readable form.
Looking for motivation in the activity patterns of a random digital threat is what helps disclose and understand its creator’s plan. This approach, when applied to the Shortcut virus, turns out to lack efficiency as the goal isn’t distinct or clear whatsoever. Making folders and files on a USB memory stick, an SD card or an HDD volume transformed into shortcuts is a strange tactic unless the hackers ultimately demand something in exchange for reverting things back to normal, for instance a ransom. This isn’t the case here, however, as the user doesn’t receive any alerts or money extortion screens.
It’s not until an in-depth code-level insight into this pest has been conducted that the underlying guile becomes obvious. The Shortcut virus can reach a remote server managed by the criminals. A possible consequence of this is identity theft, where personally identifiable data can be mined and sent over to interested parties. It’s quite probable, therefore, that the naughty manipulations with the shortcuts might be nothing but a cover that distracts the infected person from some of the more harmful things going on.
This threat tends to replicate itself over time. The obfuscated Visual Basic script adds potentially harmful entries to the system Registry, and its permanent execution is secured by the respective unsanctioned changes to Windows startup settings. Given the multiple places in the OS affected by this mischievous code, effective troubleshooting is beyond the standard removal track.
Table of Contents
Shortcut adware automatic removal
The extermination of Shortcut file can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped out from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
2. The scan will come up with a list of detected items. Click Fix Threats to get the malware removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the infection. However, it might be a good idea to consider ascertaining the adware is gone for good.
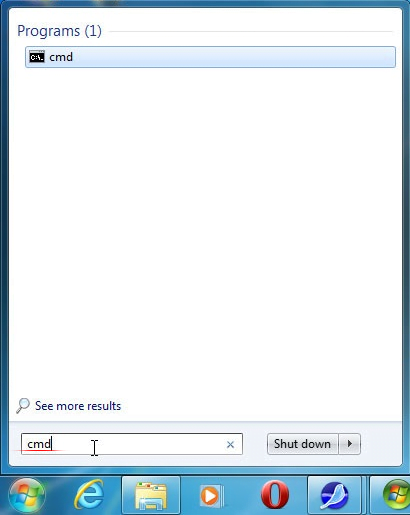
Run command to correct the display of data
- Go to Start and type cmd in the Search area. Hit Enter to open the command prompt

- Type the string below in the command line. The f attribute is a variable denoting the affected drive’s name in system hierarchy

- Press Enter for the command to take effect
Verify whether Shortcut adware has been completely removed
For certainty’s sake, it’s advised to repeatedly run a scan with the automatic security software in order to make sure no harmful remnants of this file are left inside Windows Registry and other operating system locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓