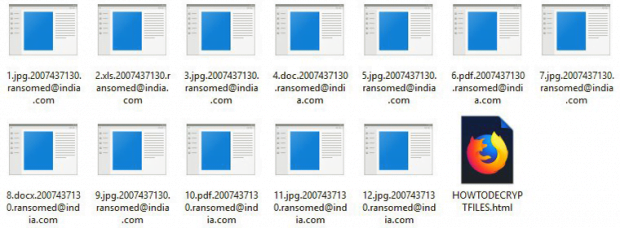
Ransomed@india.com virus: CryptON ransomware decryptor

In spite of all the predictions, ransomware is still alive and kicking. Moreover, there has been a rise in Internet extortionists’ activity lately. New samples are being coined, and old strains are resurfacing with refined attacks. The prolific CryptON lineage, for instance, has spewed out a new variant that appends the .ransomed@india.com extension to encrypted data.
Table of Contents
What is the ransomed@india.com ransomware?
The malicious program that encodes one’s files and blemishes them with the ransomed@india.com suffix is catalogued as the CryptON ransomware. Also referred to as X3M or Nemesis, this culprit hadn’t been heard of for nearly a year until it reemerged with a brand-new edition in mid-May 2018. The comeback hasn’t added much novelty to the infection’s modus operandi. The changes include the above-mentioned string being concatenated to hostage items, as well as an updated ransom note named HOWTODECRYPTFILES.html and a new desktop background alerting victims. More specifically, the original filenames are subjoined with a unique 10-digit user ID plus the email address part of the extension that provides a clue regarding a way to reach the cybercriminals.
The common contamination tactic leveraged by the ransomed@india.com CryptON version comes down to spam. The architects of this campaign have apparently hired a botnet-as-a-service to generate numerous phishing emails and send them out to thousands of users across the globe. By the way, whereas the original mod of this family zeroed in on Portuguese speaking audience, the one in question is indiscriminate in its geographic targeting. Back to the spam issue, the messages look catchy enough to get most recipients curious. The subjects can range from invoices to job offers, just to dupe users into opening the attachment. The embedded objects are the worst part, typically being RAR archives with obfuscated JavaScript entities inside. Some of the attachments are Microsoft Word files weaponized via a VBA macros technique.
One way or another, once the unsuspecting user opens the attached object they thereby unwittingly trigger the computer infestation chain. A payload is surreptitiously dropped onto the host and it downloads the rest of the ransomware modules from a C2 server. One of these components is a public key to encrypt the victim’s personal data. Prior to this phase, though, the ransomed@india.com virus scans the hard disk, attached thumb drives and network shares for files with popular extension in order to form a list of important data stored on these media. As soon as the totality of these items have been spotted, CryptON enciphers them using AES algorithm and then employs the above public RSA key to further encrypt the secret AES code. This is a robust crypto implementation that’s pretty much impossible to crack.
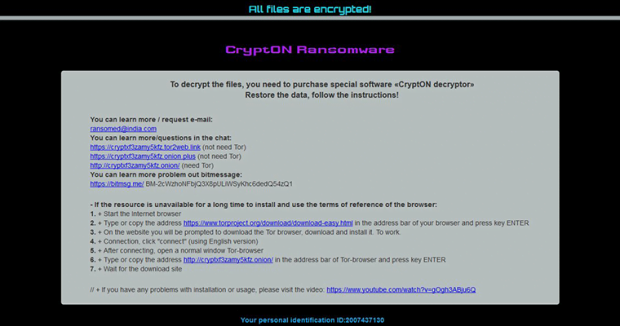
Every folder with ransomed files contains a ransom manual, an HTML object named HOWTODECRYPTFILES. It instructs the victim to choose from the following options to get started on recovery: shoot a message to the attackers’ email address ransomed@india.com; leverage a Tor-to-Web service to chat with the crooks and negotiate the terms and size of ransom; or log into a Tor gateway using the unique ID and learn the details on there. Ultimately, the fix implies a payment in Bitcoin, with the sum being 0.1-0.5 BTC in most cases. It isn’t a very good idea to submit the money headlong. Be sure to try the tips below before even thinking of such an option.
Ransomed@india.com CryptON extension automatic removal
Extermination of this ransomware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download Ransomed@india.com CryptON ransomware remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the extension and related infections removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the plague proper. Now you are facing a bigger challenge – try and get your data back.
Methods to restore files encrypted by Ransomed@india.com CryptON extension
Workaround 1: Use file recovery software
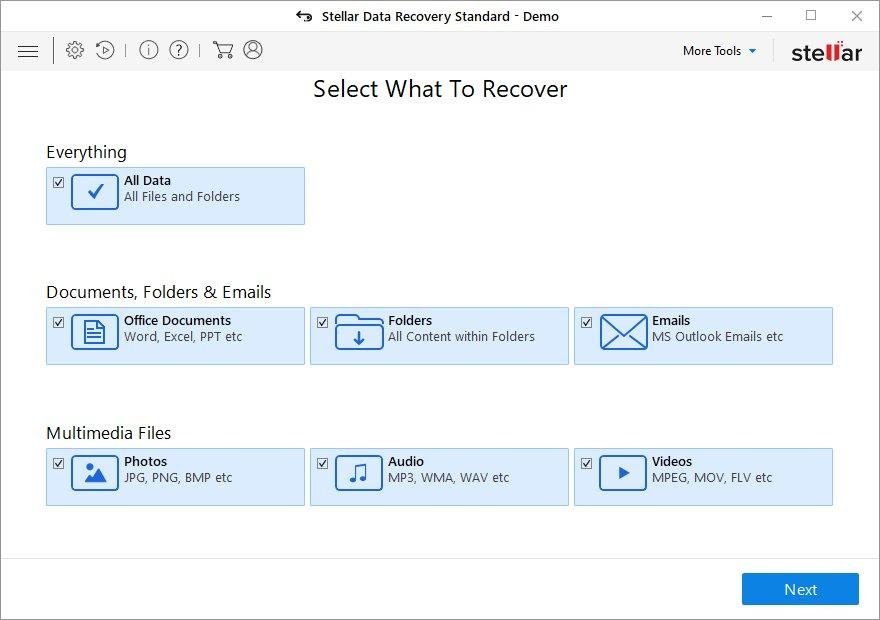
It’s important to know that the Ransomed@india.com CryptON extension creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Stellar Data Recovery for this purpose. The newest version of the extension under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Download Stellar Data Recovery Professional
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
-
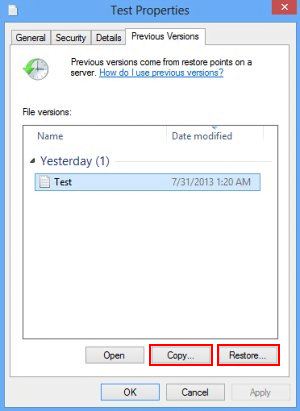
Use the Previous Versions feature
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.

-
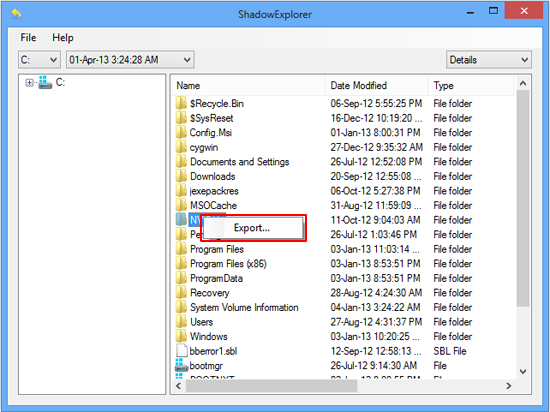
Apply Shadow Explorer tool
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.

Verify whether Ransomed@india.com CryptON extension has been completely removed
Again, ransomware removal alone does not lead to the decryption of your personal files. The data restore methods highlighted above may or may not do the trick, but the extension itself does not belong inside your computer. Incidentally, it often comes with other extension, which is why it definitely makes sense to repeatedly scan the system with automatic security software in order to make sure no harmful remnants of this extension and associated threats are left inside Windows Registry and other locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓