Porn blackmail email scam making the rounds
The ruse of social engineering is one of the oldest, most common and most effective techniques cybercriminals leverage to deceive people online. Sometimes the felons’ goal is to wheedle sensitive information out of victims, but in some scenarios the black hats seek to rip people off. The recent wave of the porn blackmail email scam pursues extortion with a flavor of massive password dumps.
Table of Contents
What is the porn blackmail email scam?
Crafty online fraudsters have come up with an intricate new way to dupe gullible computer users into coughing up money. The scheme in question involves a combo of really delicate and even intimate things. First and foremost, it has to do with sensitive credentials that victims previously used for logging into popular web services. Secondly, the perpetrators have added the adult video theme to the mix, which is something most people feel ashamed of and would rather keep secret. This explosive fusion of manipulative methods is aimed at coercing the target audience into paying a specific amount of cryptocurrency for purported non-disclosure of the embarrassing information.
The porn blackmail spam boils down to sending out targeted emails to users. The subject of such a message includes the recipient’s username and password for a certain Internet service. Most of the time, these are credentials that the person has used in the past and doesn’t use anymore. This is a clue that the crooks are leveraging information obtained from some major data leak ensuing from a high-profile hack. There have been numerous breach incidents of that kind over the last several years, including the notorious Yahoo! compromise that hit the headlines in 2016. One way or another, the indication of genuine login details, even old ones, is a strong factor of pressure and an impetus for some users to fall for the sextortion, which is a term coined to describe these particular types of hoaxes.
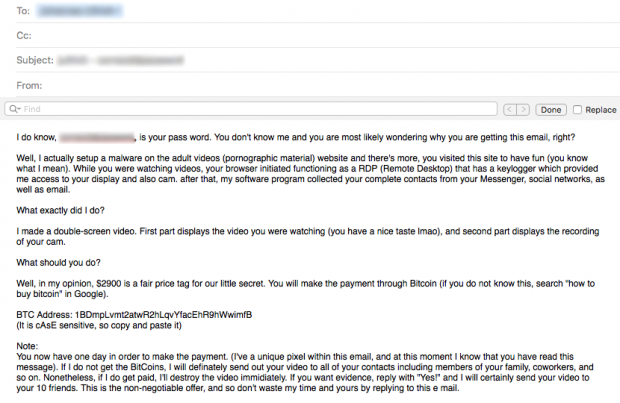
In a nutshell, the misleading email emphasizes that the attacker knows the recipient’s password for some specific account and states that a piece of malware has been installed on their computer. To top it off, this malware is claimed to have stealthily enabled RDP (remote desktop protocol) connection, which purportedly allowed the malefactor to access the webcam and display. What’s more, according to the message, the infection has harvested all of the user’s contacts from their messengers, social networks and email. Then, the con artist claims to have recorded the victim while they were watching porn, and made a double-screen video of the display as well as the “spectator”. The extortion part proper comes down to demanding $2,900 worth of Bitcoin for not sending the referenced video to all of the user’s contacts. The amount may vary, though.
Here’s what the email’s intro says:
I do know {victim’s password} is your password. You don’t know me and you are most likely wondering why you are getting this email, right? Well, I actually set up a malware on the adult videos (pornographic material) website and there’s more, you visited this site to have fun (you know what I mean). While you were watching videos, your browser initiated functioning as a RDP (Remote Desktop) that has a keylogger which provided me access to your display and also cam. After that, my software program collected your complete contacts from your messenger, social networks, as well as email.
What exactly did I do?
I made a double-screen video. First part displays a video you were watching (you have a nice taste lmao), and second part displays the recording of your cam.
Be advised that the wording may be a little different, although the idea is constant – the criminals want a buyout for not letting the user’s family, friends and colleagues know about this little secret. In fact, though, the recipients of such emails have absolutely nothing to worry about. The embarrassing video that the miscreants have supposedly made doesn’t even exist, so the scammers don’t have any incriminating materials. They are bluffing. Furthermore, the ne’er-do-wells never actually enabled remote desktop services on the PC, nor have they accessed the webcam and display. The only thing that’s true is that the black hats have the user’s password for a service they have used in the past or continue to use. This is a general concern related to massive data breaches and ways for major online services to avoid them. To make sure you are on the safe side, though, consider checking your machine for threats that may have arrived with this spam.
Verify whether porn blackmail email has been completely removed
For certainty’s sake, it’s advised to repeatedly run a scan with the automatic security software in order to make sure no harmful remnants of this scam are left inside Windows Registry and other operating system locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓