No_more_ransom: ransomware decrypter and removal [gayferber@gmail.com upd. 2017]
![No_more_ransom: ransomware decrypter and removal [gayferber@gmail.com upd. 2017]](https://soft2secure.com/wp-content/uploads/remove-no_more_ransom-file-virus.png)
The data-encrypting malware called Shade, which scrambles and blemishes victims’ files with the .no_more_ransom extension, definitely doesn’t lack sophistication. Also known as Troldesh, this digital contagion employs the AES cryptographic algorithm robustly enough to thwart brute-forcing, so anyone infected is confronted with a dilemma of paying the ransom or losing their important files.
Table of Contents
What is the No_more_ransom virus?
The .no_more_ransom string concatenated to one’s valuable files is an unambiguous hallmark sign of the latest Shade ransomware version’s activity. The wording is certainly ironic, because every victim is instructed to cough up a hefty amount of cryptocurrency in exchange for the decryption key and automated recovery service. Additional IOCs (indicators of compromise) in this scenario include the README.txt ransom note, the threat actors’ email address indicated in this decryption how-to, as well as a warning wallpaper on the desktop that replaces the one defined by the user. The infection also makes it difficult to work out which file a specific entry corresponds to, because it substitutes original filenames with a string of 64 random hexadecimal characters.
The ne’er-do-wells distributing the perpetrating entity in question are clever enough not to reinvent the wheel in terms of the pollution vector. Just like most ransomware deployers out there, they stick with the spam route to plant their Trojan onto computers. The current spam wave is powered by a botnet dubbed Kelihos. This malicious network spawns thousands of rogue emails, the subjects of which mainly revolve around banking theme. For instance, it may be camouflaged as an invoice. Each one has a ZIP archive attached to it. A booby-trapped JavaScript or Microsoft Word file extracted from this archive ends up downloading all the ransomware modules behind the scenes.
When executed, the malicious process performs a sort of reconnaissance on the plagued machine. It looks for the most popular types of data and applies symmetric Advanced Encryption Standard to lock the files down with 256-bit AES key. Again, each entry that underwent this adverse effect gets the .no_more_ransom suffix appended to it. A critical byproduct of this attack is the new black desktop background featuring English and Russian text in red font. It reads, “ATTENTION! All the important files on your disks were encrypted. The details can be found in README.txt files which you can find on any of your disks.” The referenced ransom note, in its turn, gives the victim the lowdown on recovery routine.
In particular, it contains a unique personal code and urges the infected user to send it to a specified email address. Be advised the addresses may vary. The ones reported by No_more_ransom virus victims include gayferber@gmail.com, 2Lynness.Taftfera1990@gmail.com, Novikov.Vavila@gmail.com, Yvonne.vancese1982@gmail.com, Lukyan.Sazonov26@gmail.com, files08880@gmail.com, and 7h9r341@gmail.com. Then, the crooks will get back to the victim with specific Bitcoin credentials (wallet address) to submit the ransom. The amount is in the range of 0.5-1 BTC, which is worth about $600-$1200. No automatic free decryptor has been released for the .no_more_ransom files ransomware at the moment, so those infected should build their troubleshooting tactic around general forensic recovery mechanisms, some of which are explained below. And keep in mind that reliable data backup is what can stop cyber extortionists in their tracks.
No_more_ransom ransomware automatic removal
Extermination of this ransomware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download No_more_ransom ransomware remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the ransomware and related infections removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the plague proper. Now you are facing a bigger challenge – try and get your data back.
Methods to restore files encrypted by No_more_ransom ransomware
Workaround 1: Use file recovery software
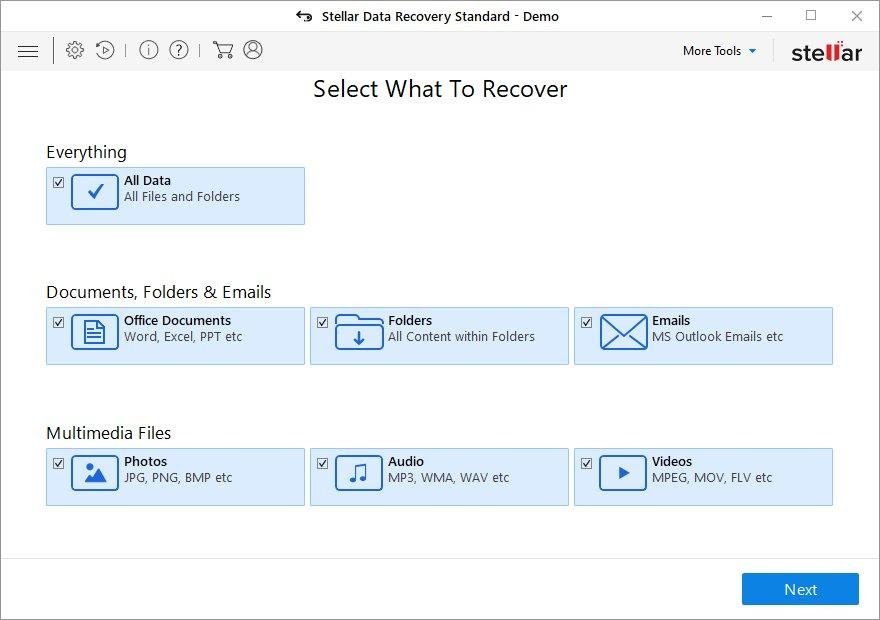
It’s important to know that the No_more_ransom ransomware creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Stellar Data Recovery for this purpose. The newest version of the ransomware under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Download Stellar Data Recovery Professional
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
-
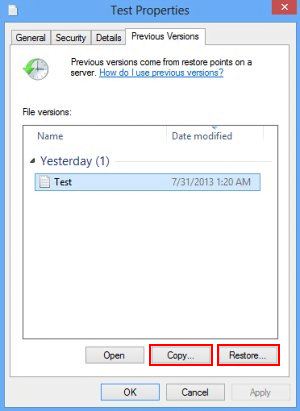
Use the Previous Versions feature
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.

-
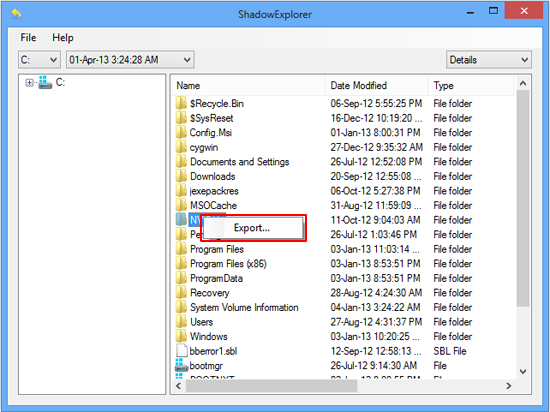
Apply Shadow Explorer tool
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.

Verify whether No_more_ransom ransomware has been completely removed
Again, ransomware removal alone does not lead to the decryption of your personal files. The data restore methods highlighted above may or may not do the trick, but the ransomware itself does not belong inside your computer. Incidentally, it often comes with other ransomware, which is why it definitely makes sense to repeatedly scan the system with automatic security software in order to make sure no harmful remnants of this ransomware and associated threats are left inside Windows Registry and other locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓