LockCrypt ransomware virus – how to decrypt .lock files
With a lot having been said about the decline of ransomware over the past year or so, this phenomenon continues to be a problem. What’s more, some of the old strains are being reanimated out of the blue and the attack campaigns appear to be massive. The infamous LockCrypt sample, for instance, is reaching new distribution heights with the .lock extension variant.
Table of Contents
What is the LockCrypt (.lock) ransomware?
The timeline of the LockCrypt ransomware reaches back to June 2017, when is original variant surfaced in a wave of attacks that relied on brute forcing remote desktop service credentials. The most disconcerting thing about this emergence was that the criminals zeroed in on corporate servers, so they could potentially affect entire networks of Windows computers and demand larger ransoms than most of the competing culprits. Quite a bit of time has elapsed ever since, and the infection has gone through ups and downs, with the latest upswing being underway at the time of this writing. Interestingly, the behavior of this blackmail virus hasn’t evolved conspicuously. It is still making the rounds via hacked RDP, displays the same warning messages and cripples filenames in the same manner, appending them with the .lock string.
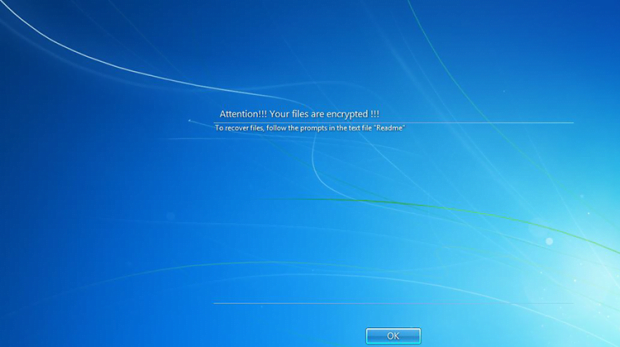
Once the bad code enters a host, it follows a commonplace recovery hindrance route by deleting the shadow copies of the victim’s files – to this end, it executes the ad hoc “vssadmin delete shadows /all” command. It also adds a new registry value in order to establish persistence and ensure that the malicious process is launched at boot time. Then goes the data scan phase, where the perpetrating code looks for potentially valuable files on the contaminated machine’s hard disk, removable media and network shares. Having spotted all the objects that meet the predefined “importance” criteria (Office documents, photos, videos, databases and the like), LockCrypt leverages XOR encryption technique to make the information inaccessible. What happens next is the victim bumps into the logon screen above.
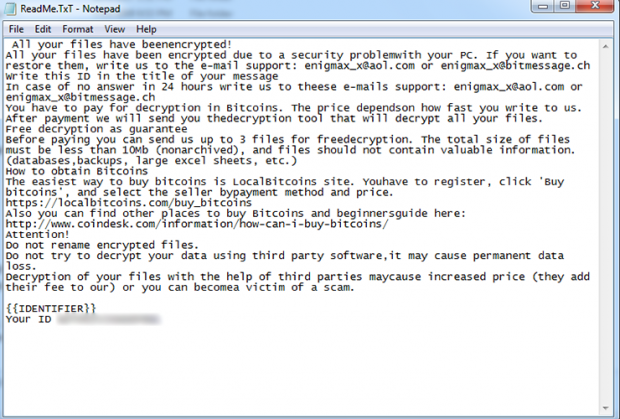
The plagued user is prompted to click OK on that screen, only to realize that the message on it going, “Attention!!! Your files are encrypted!!! To recover files, follow the prompts in the text file Readme” – isn’t a joke. All the important data turns out to be encrypted, and the filenames are mutilated according to the following pattern: [base64 of original filename] ID [victim ID].lock. A sample string will look similar to this: fj8mJhgsehwqMkhIQCw2WVFlbSM-BQ= = ID BNP3bIQFXDGVaLHR.lock. Additionally, there will be a ransom note on the desktop named ReadMe.TxT with a bunch of typos in it. It instructs the infected user to send an email to the attackers, indicating the unique victim ID in the title of the message. In response, the crooks will provide the exact size of the ransom and list the steps on how to pay it. The sum of buyout in this scenario varies, depending on how big the contaminated enterprise network is. It’s usually somewhere between 0.5 and 1 Bitcoin.
If the malefactors carry through with their promises – which isn’t guaranteed at all – they are supposed to provide the decrypt tool and the secret key so that the victim can undo the damage and recover the .lock files that are held hostage. By the way, a few other editions of LockCrypt are in the wild concurrently. These include builds that blemish encrypted files with the .BI_D, .1btc, .2018, or .mich extension. Regardless of the iteration, paying the ransom is not recommended. The tips below should help restore the skewed data and leave the ne’er-do-wells behind the .lock variant of LockCrypt ransomware with their pockets empty.
LockCrypt (.lock) extension automatic removal
Extermination of this ransomware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download LockCrypt (.lock) ransomware remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the extension and related infections removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the plague proper. Now you are facing a bigger challenge – try and get your data back.
Methods to restore files encrypted by LockCrypt (.lock) extension
Workaround 1: Use file recovery software
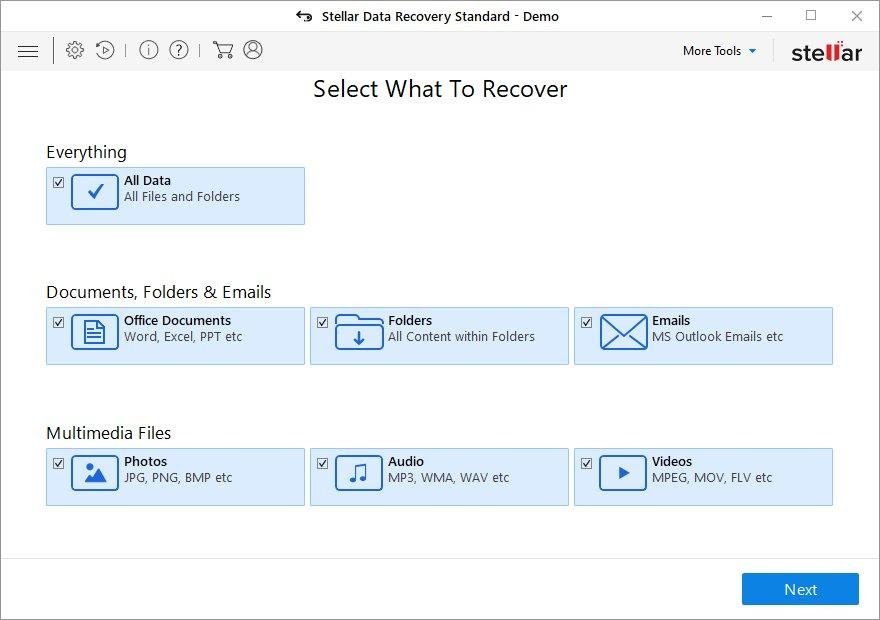
It’s important to know that the LockCrypt (.lock) extension creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Stellar Data Recovery for this purpose. The newest version of the extension under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Download Stellar Data Recovery Professional
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
-
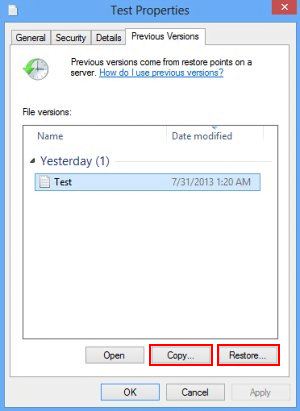
Use the Previous Versions feature
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.

-
Apply Shadow Explorer tool
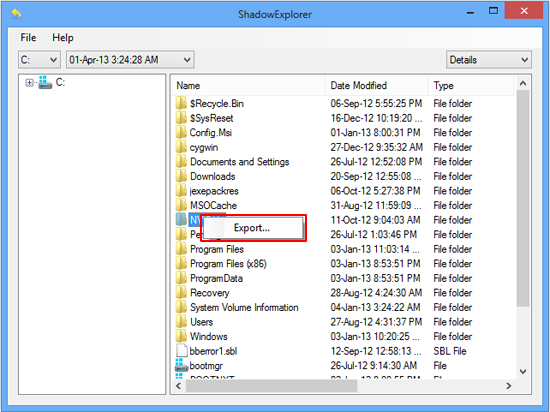
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.

Verify whether LockCrypt (.lock) extension has been completely removed
Again, ransomware removal alone does not lead to the decryption of your personal files. The data restore methods highlighted above may or may not do the trick, but the extension itself does not belong inside your computer. Incidentally, it often comes with other extension, which is why it definitely makes sense to repeatedly scan the system with automatic security software in order to make sure no harmful remnants of this extension and associated threats are left inside Windows Registry and other locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓