Jaff Decryptor System virus: Jaff ransomware removal
A cybercrime group that might be affiliated with the Locky ransom Trojan have unleashed another crypto disaster called the Jaff ransomware. This release deviates from the well-trodden path that the suspected threat actors have gone since February 2016. As opposed to a rock-hard mix of RSA and AES algorithms, the new Locky lookalike uses AES-128 cryptographic standard alone to turn data access attempts into a no-go. When it comes to new features, the digital intruder in question now appends the .jaff extension to files and leaves ransom notes called ReadMe.html/txt/bmp.
Table of Contents
What is the Jaff ransomware?
The Jaff file-encrypting virus bears a strong resemblance to ransomware infections representing the Locky family, one of the dominating lineages of the cryptographic malware epidemic. Although there is a vast variety of suchlike infections in the wild, they all stick with a uniform extortion tactic. Having contaminated a computer, these creepy cyber pests scour local and mapped data repositories for multiple file types, encrypt whatever is found, and suggest an uncomforting buyout deal. With this whole functional similarity in place, some of these offending programs have lame coding and implementation, which allows researchers to come up with free decryption methods. Unfortunately, Jaff isn’t one of these crude strains. It boasts a professional take on handling cryptographic keys, therefore a viable cracking mechanism is yet to be contrived by analysts.
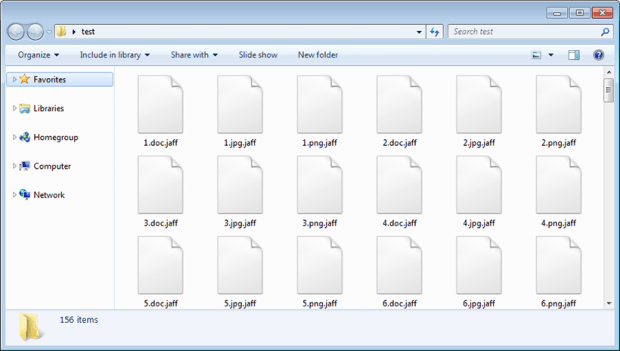
Whereas all the earlier versions of the Locky ransomware have had a great deal of common characteristics, there are hallmark signs that vary from edition to edition. First of all, the threat actors never reuse specific file extensions. The previous variant concatenated the .osiris extension to every filename, but the one in question has its own unique suffix for this purpose. It labels mutilated files with the .jaff string. This tweak is pretty much the only visible effect upon a victim’s personal data – the Trojan does not scramble the original names of encoded files beyond recognition, unlike its predecessors. As far as this sample is concerned, it’s easy to correlate a specific file with its modified counterpart.
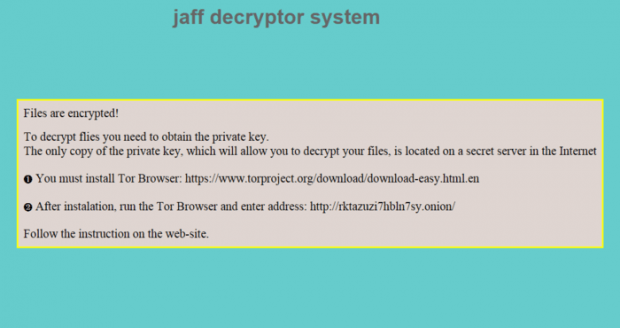
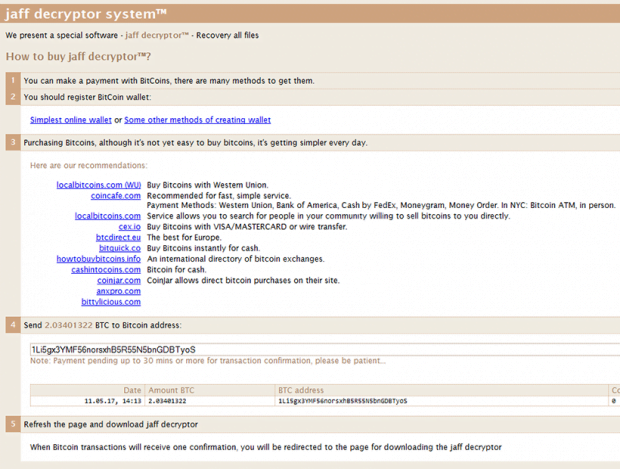
The Jaff ransomware uses a set of troubleshooting manuals to walk victims through the decryption routine. It sprinkles these notes across the contaminated system, including such locations as the desktop and every single folder with inaccessible entries inside. Incidentally, the new desktop background becomes another medium for the infection to explicate the recovery steps. The ReadMe.html, ReadMe.txt and ReadMe.bmp ransom notes tell the victim to download and install Tor Browser, run it, type the unique onion URL provided in any of the help documents, and then follow the instructions on the Tor page titled “Jaff Decryptor System”. Be advised it’s impossible to access said resource via a regular web browser. The malefactors stick with The Onion Router technology to avoid tracking and attribution. The secret page provides the victim with further directions, including the ransom amount and Bitcoin address to submit it. The size of the ransom is somewhere in the range of 1.8-2.3 BTC most of the time. It varies from incident to incident, though.
To stay away from the Jaff virus, users should follow safe online practices. Most importantly, when a suspicious email is received, it’s recommended to pass by and never open the attached file. Jaff distributors use a bevy of catchy email themes to lure people into opening contagious JS, VBA or DOCM files. Some of these rogue subjects include receipts, subscription details, printouts, tracking sheets and the like. The current malspam campaign, which is backed by Locky’s favorite Necurs botnet, uses such themes as Copy_[random number string], PDF_[random number string], Document_[random number string], Scan_[random number string], and File_[random number string]. The catch is fairly commonplace: victims are duped into opening the attached file, which in its turn triggers a Microsoft Office macros-based contamination chain.
In addition to proper online hygiene, the use of up-to-date antimalware suite is another ransomware protection layer. Furthermore, the best risk mitigation strategy is to maintain file backups. If the Jaff ransomware is already on board, be sure to follow the tips below for a start.
Jaff ransomware automatic removal
Extermination of this ransomware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download Jaff ransomware remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the ransomware and related infections removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the plague proper. Now you are facing a bigger challenge – try and get your data back.
Methods to restore files encrypted by Jaff ransomware
Workaround 1: Use file recovery software
It’s important to know that the Jaff ransomware creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Stellar Data Recovery for this purpose. The newest version of the ransomware under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Download Stellar Data Recovery Professional
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
-
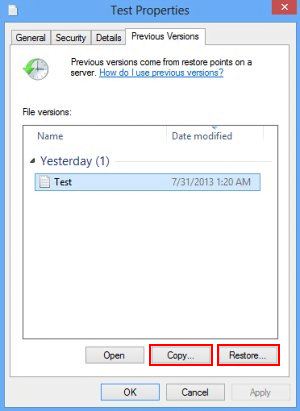
Use the Previous Versions feature
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.

-
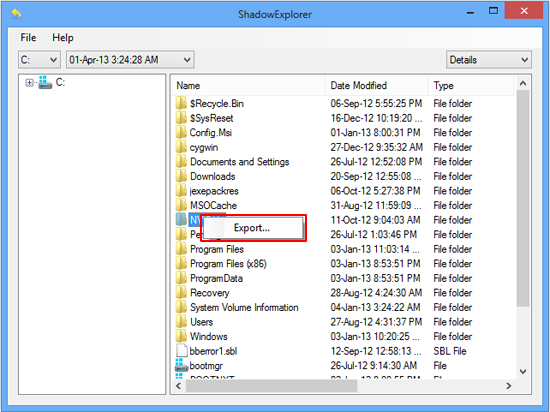
Apply Shadow Explorer tool
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.

Verify whether Jaff ransomware has been completely removed
Again, ransomware removal alone does not lead to the decryption of your personal files. The data restore methods highlighted above may or may not do the trick, but the ransomware itself does not belong inside your computer. Incidentally, it often comes with other ransomware, which is why it definitely makes sense to repeatedly scan the system with automatic security software in order to make sure no harmful remnants of this ransomware and associated threats are left inside Windows Registry and other locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓