Remove eDellRoot certificate vulnerability on a Dell computer
Months after the scandalous exposure of the Superfish adware app being pre-installed on Lenovo laptops, Dell machines sold since July 2015 were found to be shipped with a digital certificate that might get the customers’ sensitive data compromised. Called eDellRoot, this entity is originally intended to facilitate automated support and maintenance of laptops and desktop PCs by Dell, but it can also be exploited for accessing the user’s private data such as passwords, email, etc.
The world’s most trusted manufacturers of consumer electronics turned out to be error-prone in the touchy areas related to their client’s privacy. There’s no reason to question the unintended nature of these occurrences, where the troublemaking solutions are meant to enhance and improve stuff. In the case of the eDellRoot certificate, it is tasked with helping the company’s support servers identify the hardware model in automatic help request scenarios. It is installed by the Dell Foundation Services (DFS), an official application designed for sustaining the general support and serviceability functions.
A research that surfaced lately, however, proves that this certificate can be leveraged for decrypting one’s Internet traffic and stealing personally identifiable information, including banking credentials, account logins and the like.
According to Dell’s press release, the certificate is not used to collect personal information of the user. This fact, though, doesn’t eliminate the possibility of black hat hackers deploying man-in-the-middle attacks by means of it. The customer whose machine was bundled with eDellRoot gets a private key that can be accessed by third parties in certain circumstances, including the cases when the clients use WiFi hotspots with weak authentication parameters. Since this problem is currently isolated to Windows users, Microsoft has reportedly rolled out updates of their security software that are capable of detecting and removing the potentially harmful certificate. However, chances are the deleted object might be reinstalled if the cleanup wasn’t thorough enough.
Unfortunately, as per the most recent insight, the number of affected PCs isn’t restricted to the quantity sold since July this year. The older boxes that received DFS updates from Dell are subject to possible compromise as well. The optimal method to fix the security hole in question is to disable the above-mentioned Dell Foundation Services process while deleting eDellRoot cert, otherwise the issue is likely to reoccur. The service can be re-enabled after the removal. If you think you might be affected, use the steps below to check for the vulnerability and get rid of it.
Table of Contents
eDellRoot certificate automatic removal
The extermination of eDellRoot certificate can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped out from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
2. The scan will come up with a list of detected items. Click Fix Threats to get the certificate removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the infection. However, it might be a good idea to consider ascertaining the certificate is gone for good.
Remove eDellRoot certificate manually
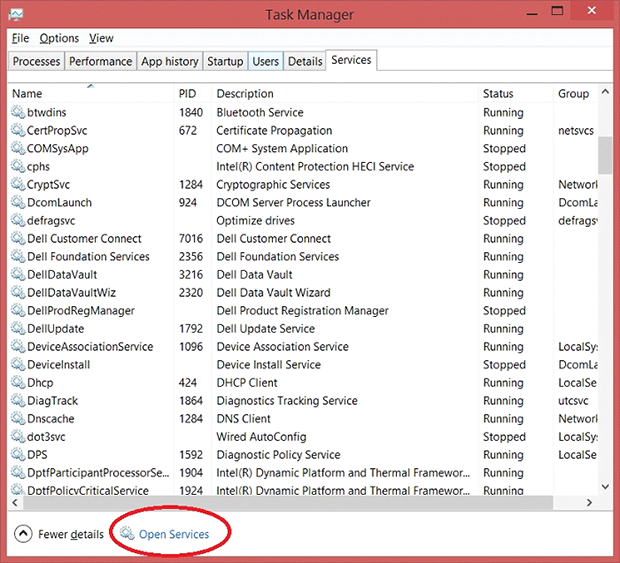
- Open up your Task Manager by selecting the respective entry in the taskbar’s context menu or by simultaneously pressing Ctrl+Alt+Del

- Hit the Services tab in the upper right-hand part of the Task Manager window and click Open Services at the bottom

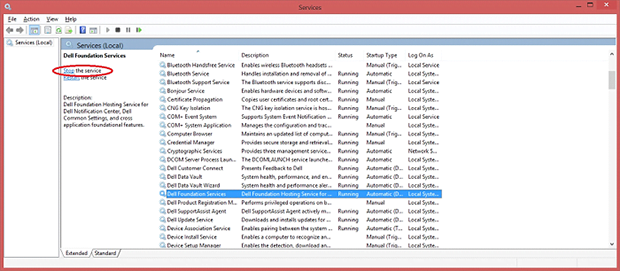
- The system will now display the Services screen. Locate Dell Foundation Services on the list, select this entry and click Stop the service in the left-hand pane

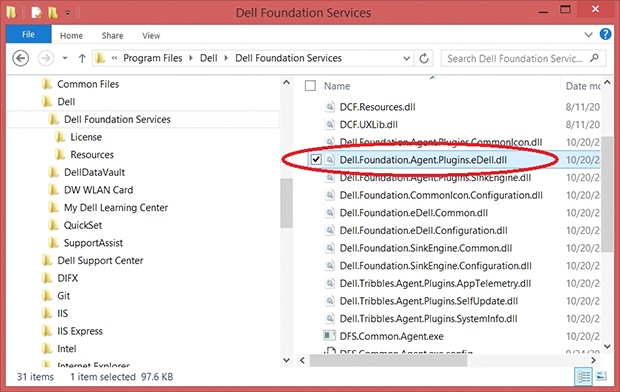
- Go to Program Files\Dell\Dell Foundation Services and delete the file named Dell.Foundation.Agent.Plugins.eDell.dll

- Follow the prompts to complete the deletion
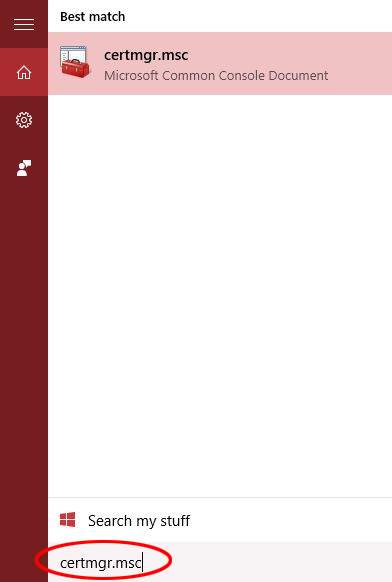
- In the Windows Search box, type certmgr.msc and hit Enter

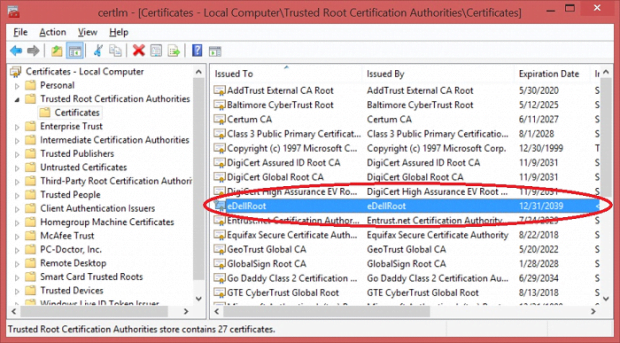
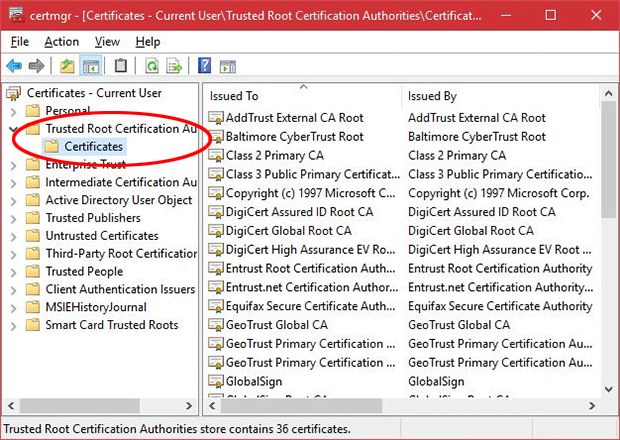
- Go to Trusted Root Certification Authorities – Certificates

- Find the entry for eDellRoot on the list, select it and click the X icon at the top of the screen

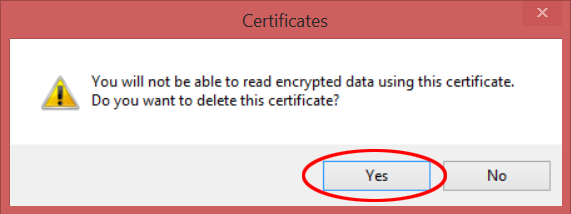
- Click Yes on the popup to confirm the delete transaction

- Return to the Services interface in your Task Manager, find Dell Foundation Services and click Start the service button to re-enable it

- The potentially vulnerable eDellRoot certificate should now be completely deleted from your Dell machine
Verify whether eDellRoot certificate has been completely removed
For certainty’s sake, it’s advised to repeatedly run a scan with the automatic security software in order to make sure no harmful remnants of this certificate are left inside Windows Registry and other operating system locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓