Remove DoubleLocker ransomware from Android device

The concept of Android ransomware isn’t new, moreover, it has been on a steady rise throughout 2017. Most blackmail viruses targeting this mobile operating system lock the screen of infected devices and coerce users into paying up in order to reobtain the access. With the new sample called DoubleLocker, though, cybercriminals broke new ground as its impact is far more serious.
Table of Contents
What is the DoubleLocker virus?
DoubleLocker (Double Locker) is a really innovative Android ransomware strain that causes critical damage and leaves hardly any room for maneuver when it comes to remediation. As opposed to mainstream digital culprits from this category zeroing in on mobile devices, the specimen under scrutiny has added real crypto to its repertoire. It used to be that Android ransom Trojans would simply pull off a fairly prosaic screen locking trick without messing with the stored data. In this scenario, victims are able to get around the lock in a few steps and move on with their day. This has changed with the emergence of DoubleLocker. Its adverse effect is twofold: screen locking plus files encryption.
Security researchers have found ties between DoubleLocker and Svpeng, a notorious Android banking Trojan. The two presumably share the same code, except that the ransomware isn’t equipped with a module for stealing banking data. The infection chain begins with installation of a booby-trapped app pretending to be Flash Player. During the setup, the user is presented with an ostensibly commonplace privileges granting screen. This routine is actually trickier than it appears, because opting into these permissions means that the perpetrating application obtains access to the Accessibility service on the device. The upshot of this is hype is somewhat of a science fiction that came true – DoubleLocker will be able to imitate user taps. This way, it gets into settings and does what’s needed to get administrative privileges.
The above misdemeanor is only part of this Trojan’s modus operandi. Next, it gets down to real damage by setting a new PIN passcode so that the victim is unable to get past the lock screen. To add insult to injury, DoubleLocker also finds and encrypts all data kept on the primary storage of the Android device, blemishing them with the .cryeye extension. To ensure the files become inaccessible for good, the pest leverages symmetric AES cipher to lock each one.
When done wreaking havoc, the ransomware displays a ransom note titled ‘Current state information’. It reads, “Your personal documents and files on this device have just been crypted. The original files have been deleted and will only be recovered by following the steps described below. The encryption was done with a unique generated encryption key (using AES-256).” The note also contains an indicator of how much time is left before the data is completely lost, the deadline being 24 hours. Aside from this, the statistics listed on this screen include the number of encrypted files and the size of the ransom, which is set to 0.0130 BTC (currently worth $73).
Unfortunately, there is no free way to decrypt .cryeye files affected by the DoubleLocker ransomware. Meanwhile, submitting the ransom isn’t a guarantee of restoring encrypted data either. So this particular digital onslaught is a very serious predicament. The only good news, though, is that it’s possible to regain access to the ransomware-stricken Android device. See sections below for details.
DoubleLocker ransomware removal
What you need to do is uninstall the application that’s causing trouble. As it has been mentioned, however, disabling and removing the virus in regular mode is to no avail, so the steps below are must-follow.
1. Boot the device into safe mode
– Press and hold the Power button until the respective screen pops up
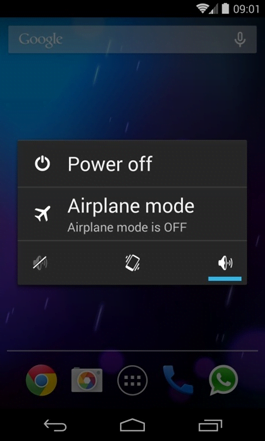
2. Now tap and hold the option that says Power off. Depending on the vendor and the phone model, the methods can vary. If nothing happens as a result of the above manipulations, power down the device, then press and hold the Volume Down and Volume Up buttons simultaneously while it’s starting back up.
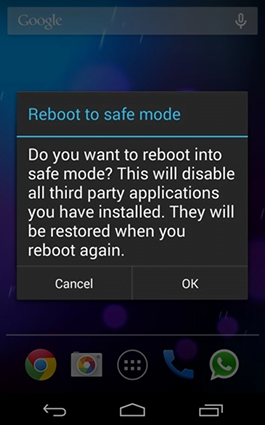
3. Confirm rebooting into safe mode by tapping OK
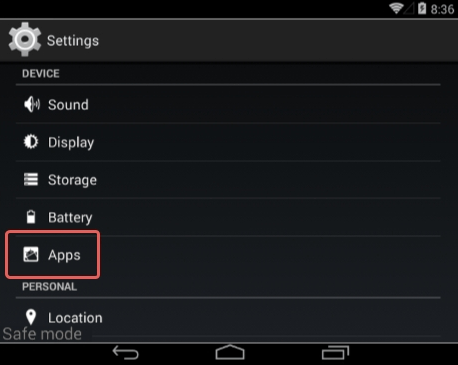
4. When in safe mode, go to Settings and select Apps
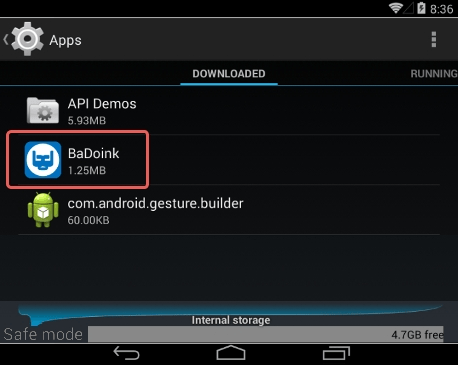
5. Look down the list of programs and locate a suspicious app or apps that were recently installed
6. Tap each potentially unwanted app in turn and select the Uninstall option. If this button is not active, try Force stop first
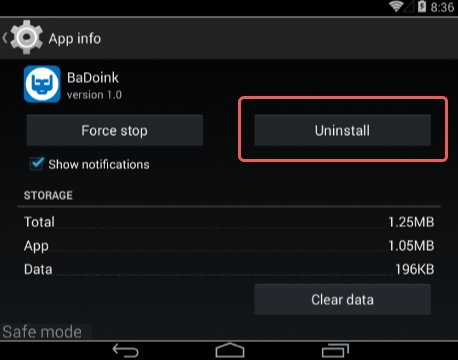
7. Tap OK on the confirmation dialog to uninstall the potentially unwanted app
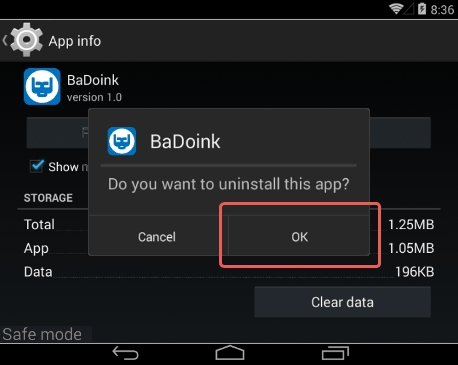
8. Restart into standard mode. The DoubleLocker ransomware should have now vanished from your Android device. You might also want to consider installing a mobile security solution to prevent attacks of this sort further on.
Posted in: KnowledgeBase
Leave a Comment (0) ↓
