Dbsync download virus: px.ads.linkedin.com popups removal
The computer threat landscape isn’t homogeneous. There are infections that operate stealthily – rootkits and Trojans make a few good examples. On the other hand, there are digital culprits that act in an outright fashion, adware being by far the prevalent type of malicious code in this niche. The annoying popup virus referred to as dbsync, though, doesn’t seem to make a whole lot of sense when it comes to its goals.
Table of Contents
What is the dbsync download virus?
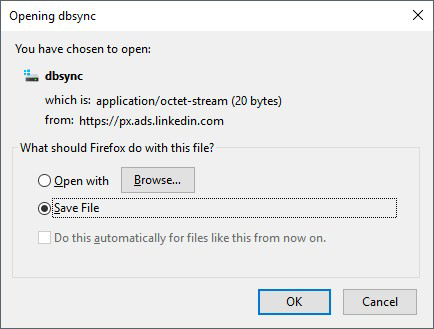
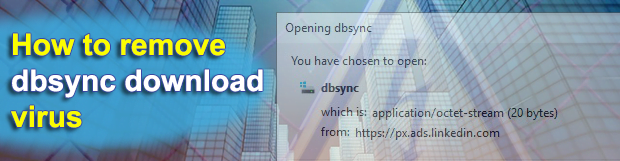
The controversial cyber-entity dubbed dbsync has been the talk of the town over the past few days. A lot of users have been reporting obnoxious popup dialogs that appear all of a sudden and ask them to download said file. To add insult to injury, this isn’t a one-time encounter and the annoying box tends to show up repeatedly even if users hit the Cancel button. The dialog is titled “Opening dbsync” and says the strange file is being downloaded from px.ads.linkedin.com URL. The troublemaking object is labeled as “application/octet-stream” and takes up as little as 20 bytes. It’s noteworthy that this issue mainly occurs in Firefox.
The information provided on the download box, therefore, gives a clue that the pest is served from a LinkedIn ad server, which is somewhat bizarre, given the reputation of the service. A likely explanation of this boils down to the plausible assumption that cybercriminals were able to compromise the legit server belonging to the popular business service in question. Ad networks are juicy targets for hackers, because they allow for large-scale distribution of various malware programs. In this particular scenario, however, there is a bit of discrepancy in place. Although the dbsync file is purported to be 20 bytes long, it turns out empty when saved. This fact doesn’t seem to fit in the malware delivery paradigm.
Aside from the above objective, the gist of the dbsync download popups may be related to measuring certain portions of Internet traffic or imitating user hits in an attempt to monetize them. The thing is, px.ads.linkedin.com looks like an analytics server tasked with tracking user visits. The popups under scrutiny might be a symptom of malware presence on a computer. Specifically, it can be some third-party cookie or plugin that monitors victims’ web traffic patterns and also mimics their hits to the predefined domain – a scheme reminiscent of commonplace browser hijacking. To recap, the dbsync virus is either a malware spreading instrument or a traffic monetization tool operated by unscrupulous black hats. Even if it’s an upshot of a malfunctioning ad server, the issue needs to be solved without delay.
Dbsync download ads automatic removal
The extermination of Dbsync download ads can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped out from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download Dbsync download remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the ads removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the infection. However, it might be a good idea to consider ascertaining the ads is gone for good.
Remove Dbsync download ads using Control Panel
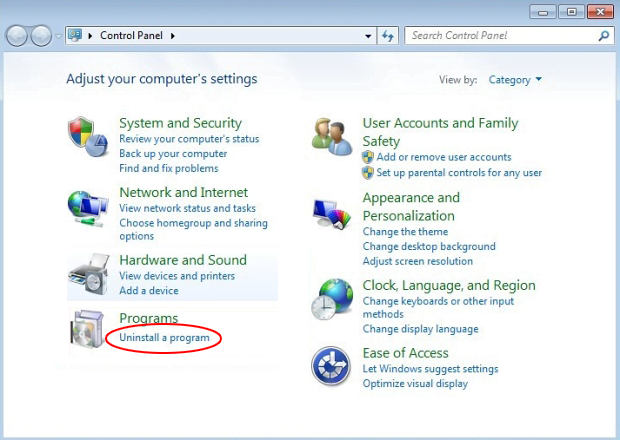
- Open Control Panel. On Windows XP / Windows 8, go to Add or Remove Programs. If your OS is Windows Vista / Windows 7 / Windows 10, choose Uninstall a program

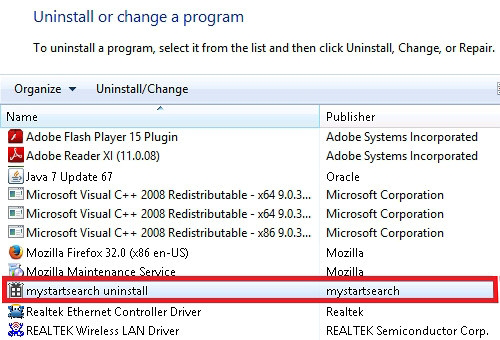
- Look down the list and locate an app that appears fishy. Click the Uninstall/Change (Change/Remove) option to get the intruder removed if spotted

Dbsync download ads removal by resetting the affected browser
Please take into consideration that as effective as it is, the procedure of restoring browser defaults will lead to the loss of personalized settings such as saved passwords, bookmarks, browsing history, cookies, etc. In case you are not certain this outcome is suitable despite its obvious efficiency, it’s advised to follow the automatic removal method described in one of the previous sections of this tutorial.
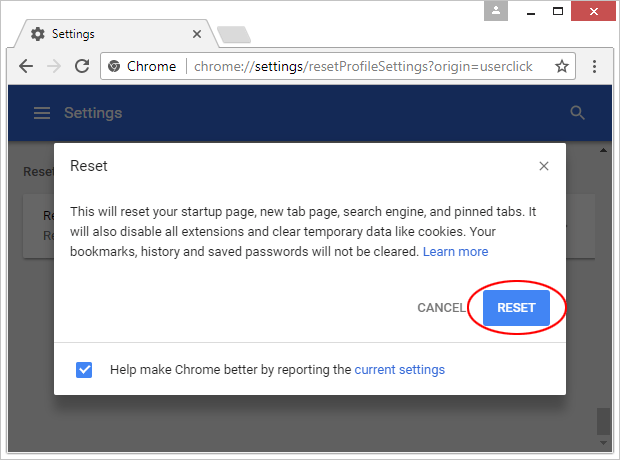
Reset Google Chrome
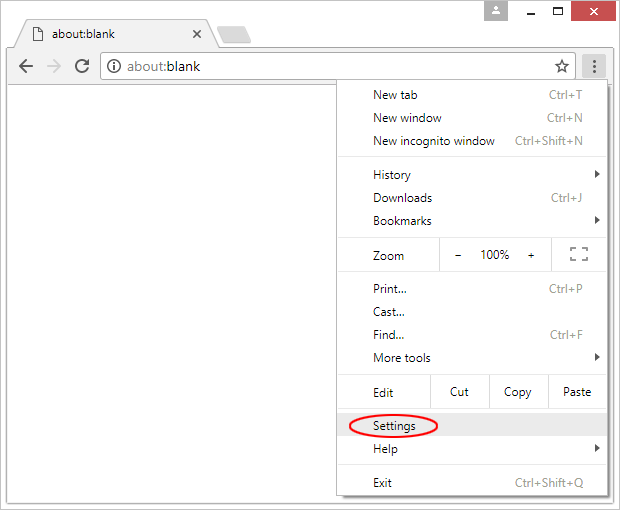
- Click on the Chrome menu icon and select Settings

- Locate the Advanced option under Settings and click on it to expand the menu. Then, pick the Reset button at the bottom

- When a new screen appears, hit Reset once again

- Chrome will now display a confirmation dialog box listing the types of data that will be lost if you proceed. Read the message carefully and, if you’re sure, click Reset

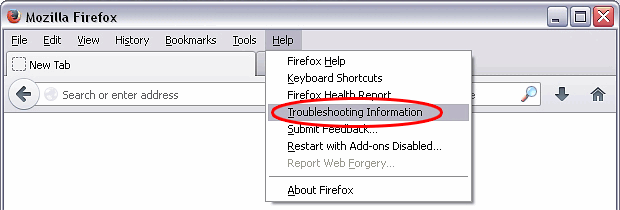
Reset Mozilla Firefox
- Click on Help menu and select Troubleshooting Information from the drop-down list, or type about:support in the URL field

- On the Troubleshooting Information screen, click Refresh Firefox option and confirm the procedure on another dialog

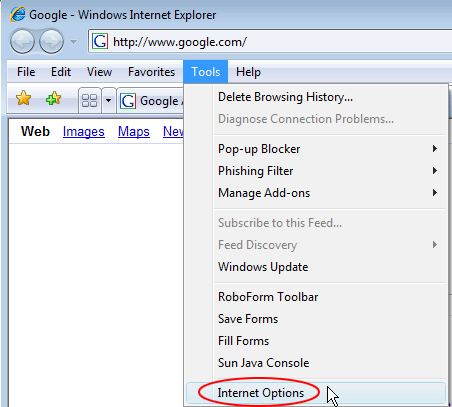
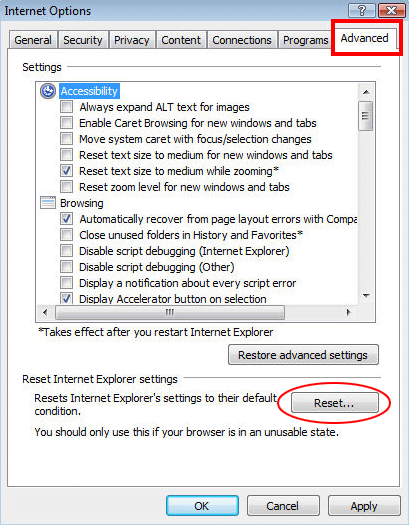
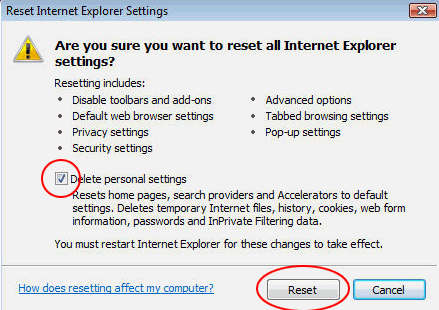
Reset Internet Explorer
- In IE, go to Tools and select Internet Options from the list

- Hit the Advanced tab and click on the Reset option

- IE will now display Reset Internet Explorer Settings box, where you should put a checkmark next to Delete personal settings option and click Reset at the bottom

Verify whether Dbsync download ads has been completely removed
For certainty’s sake, it’s advised to repeatedly run a scan with the automatic security software in order to make sure no harmful remnants of this ads are left inside Windows Registry and other operating system locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓