Remove Cry128 / Cry9 ransomware and decrypt locked files
Ransom Trojans that seem to be different on the outside can often be attributed to the same lineage of crypto threats. That’s the case with the Cry128 and Cry9 strains. Each one featuring unique indicators of compromise, the common ground is the CryptON, or Nemesis, ransomware family that gave birth to them.
Table of Contents
What is the Cry128 / Cry9 ransomware?
Cry128 and Cry9 file-encrypting threats share common roots. Just like their malicious brethren Nemesis and X3M, they were created with an identical builder, which is a specially crafted tool facilitating and automating the workflow of generating a ransomware executable. The generic name for this family is CryptON. It began making the rounds in late 2016 and has since spawned a few derivatives. Both of the latest samples from this group scramble one’s data through a robust encryption routine and subsequently engage a despicable extortion mechanism. To lock files down, they leverage a customized version of AES (Advanced Encryption Standard) that operates in Electronic Codebook (ECB) mode. A byproduct of this routine is the generation of 1024-bit encryption and decryption keys, which originally seemed impossible to retrieve beyond payment-based method.
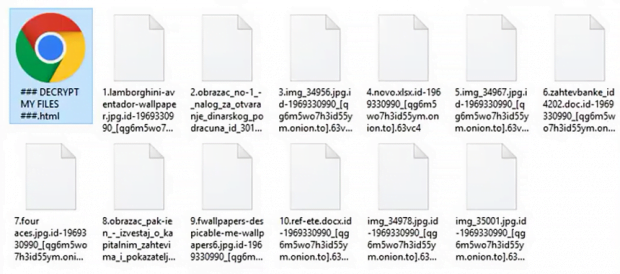
Interestingly, the Cry128 / Cry9 variants of CryptON don’t go equipped with a predefined list of targeted data formats. In other words, the ransomware is configured to encode all files spotted on a computer. The only paths it skips during the HDD and network drives traversing process include Program Files, Windows as well as the folder it is launched from. The motivation behind these exclusions are obvious – the crooks need the machine to work smooth during the onslaught. Having applied the above-mentioned encryption mechanism to deny access to a victim’s personal files, the Cry128 ransomware edition will append one of the following extensions to them: .id_[victim ID]_gebdp3k7bolalnd4.onion._, .id_[victim ID]_2irbar3mjvbap6gt.onion.to._, .id-[victim ID]_[qg6m5wo7h3id55ym.onion.to].63vc4, or .fgb45ft3pqamyji7.onion.to._.
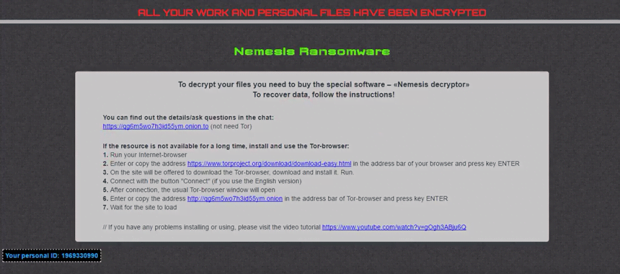
The Cry9 variant, in its turn, tends to concatenate a different set of strings to ransomed files. These include: .[victim ID]-juccy@protonmail.ch, .id-[victim ID], .id-[victim ID]_[nemesis_decryptor@aol.com].xj5v2, .id-[victim ID]_r9oj, .id-[victim ID]_x3m, .id-[victim ID]_[x3m-pro@protonmail.com]_[x3m@usa.com].x3m, and .[victim ID]_[wqfhdgpdelcgww4g.onion.to].r2vy6. As part of the attack, the ransomware won’t fail to drop a ransom note named ### DECRYPT MY FILES ###.html onto the desktop and folders with encrypted information. This how-to instructs the victim to buy special software called “Nemesis Decryptor”. To do it, the infected user has to visit an ad hoc Tor page and follow payment steps listed there. The amount to pay varies from case to case. It ranges from 0.5-1.5 Bitcoin, or about $800-$1,700.
It’s worth mentioning that the Cry128 and Cry9 spinoffs of CryptON ransomware are planted into computers through Remote Desktop Protocol vector. What the malefactors do is they brute-force RDP access credentials to execute the infection. This fact suggests that the attacks may be targeted, and the criminals primarily zero in on organizations or specific users. Fortunately, a well-known security vendor has recently come up with an automatic free decryption technique. If the compromise has taken place and all valuable data has been encrypted, be sure to follow the instructions below.
Cry128 / Cry9 ransomware automatic removal
Extermination of this ransomware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download Cry128 / Cry9 ransomware remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the ransomware and related infections removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the plague proper. Now you are facing a bigger challenge – try and get your data back.
Decrypt Cry128 / Cry9 ransomware with Emsisoft decryptor
Emsisoft security firm has been all-time leader in cracking ransomware infections. The company has got free decryption tools in store to handle CryptON iterations, including Cry128 and Cry9. Before using the software, though, it’s mandatory that the perpetrating code proper be removed via the cleanup steps above, otherwise the data may be repeatedly locked down after successful recovery. Also, be sure to change your RDP password to thwart a relapse in the future.
To proceed, you need to pick a sample encrypted file whose size is 128 KB or more, and its unencrypted copy. Once you have this pair, follow the steps below:
1. Download Emsisoft Decryptor for Cry128 or Cry9 (depending on the strain you are infected with)
2. Select a sample enciphered file and its accessible counterpart, then drag and drop this pair onto the decryptor interface 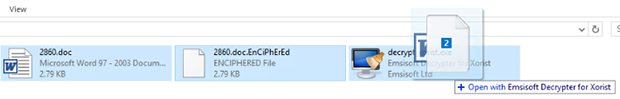
3. The tool will now try to brute-force the decryption key. Be advised the process may be time-consuming 
4. Once the necessary information has been retrieved, the tool will display a “Decryption key found” dialog
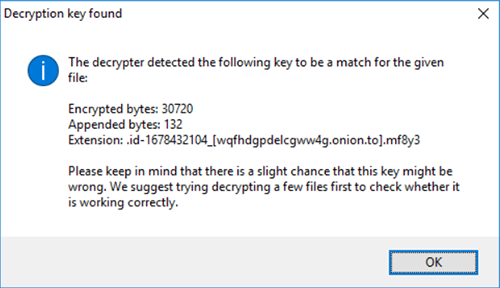
5. After you click OK on the above notification, a window with License Terms pops up. Click Yes to proceed with decryption. Then, the main GUI of the solution will appear 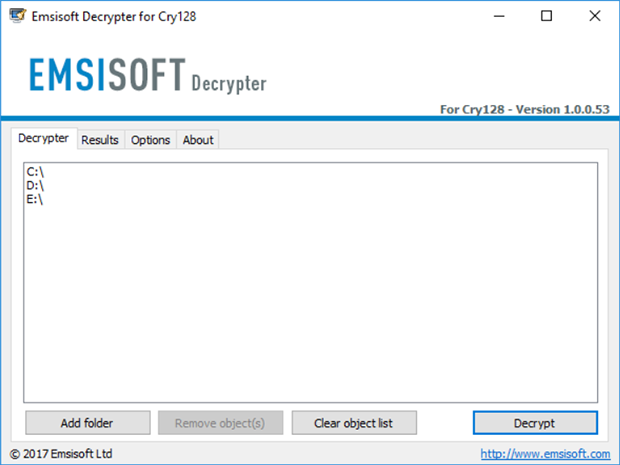
6. By default, the tool processes information inside local drives and connected network drives. Use the Add folder option to add more paths. Now click on the Decrypt button to start data recovery
7. As soon as decryption has been completed, the application will let you know by displaying an appropriate message 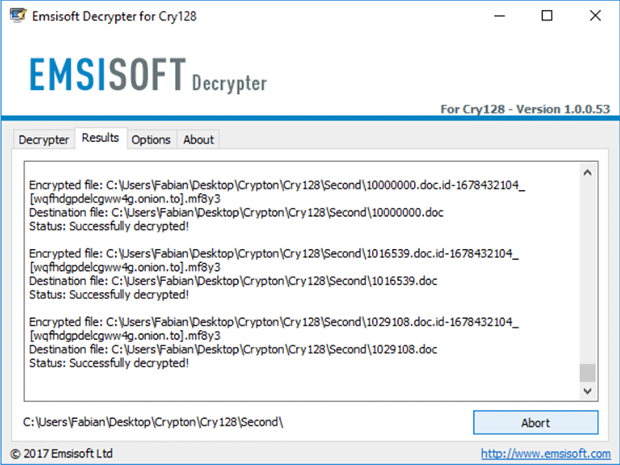
There are incidents, though, where victims don’t have an unencrypted copy of a sample enciphered file, or its size is smaller than required. In this case, Emsisoft Decryptor for Cry128 / Cry9 won’t do the trick. Also, sometimes the tool may be unable to brute-force the crypto key. If you have come across such hurdles, try the following workarounds.
Methods to restore files encrypted by Cry128 / Cry9 ransomware
Workaround 1: Use file recovery software
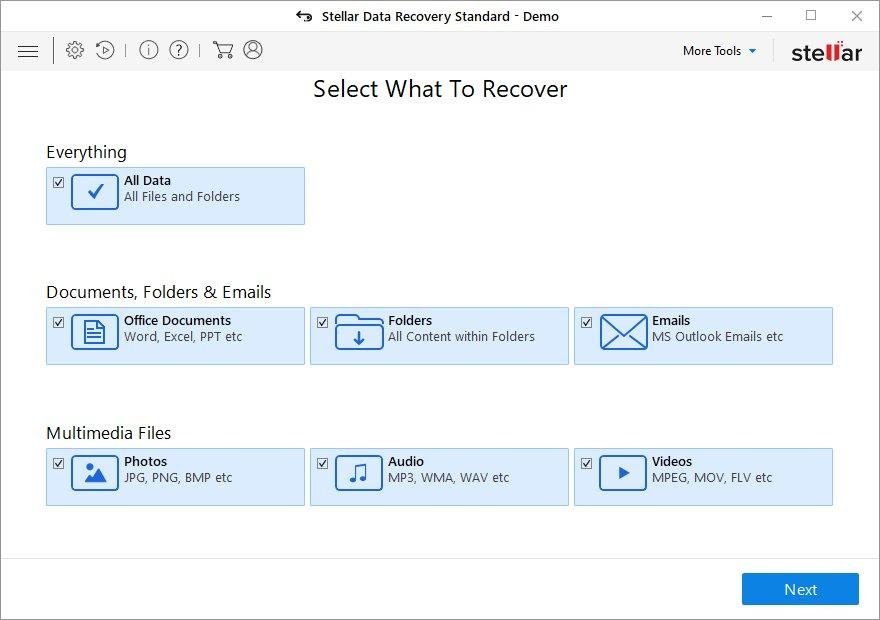
It’s important to know that the Cry128 / Cry9 ransomware creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Stellar Data Recovery for this purpose. The newest version of the ransomware under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Download Stellar Data Recovery Professional
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
-
Use the Previous Versions feature
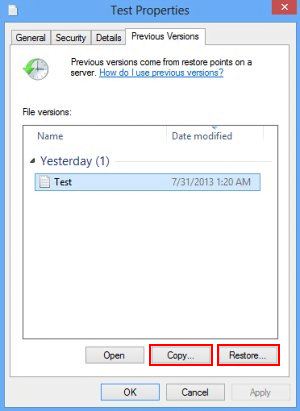
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.

-
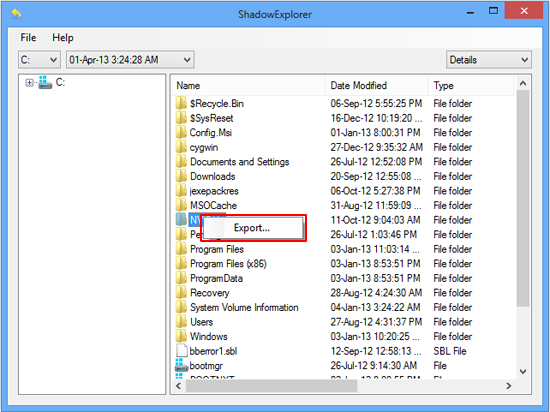
Apply Shadow Explorer tool
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.

Verify whether Cry128 / Cry9 ransomware has been completely removed
Again, ransomware removal alone does not lead to the decryption of your personal files. The data restore methods highlighted above may or may not do the trick, but the ransomware itself does not belong inside your computer. Incidentally, it often comes with other ransomware, which is why it definitely makes sense to repeatedly scan the system with automatic security software in order to make sure no harmful remnants of this ransomware and associated threats are left inside Windows Registry and other locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓