Cyber Crime Origin: Russia as a Nursery

The article starts explaining why and how Russia hosts probably the most capacious source of malicious programs worldwide.
It’s common knowledge that most of the contemporary computer threats come from countries which do not apply appropriate effort to nip malware developers/releasers. A good or rather the most striking example of such kind is Russia, notorious for mass-spreading of malware, especially such types as ransomware, fake antispyware etc.
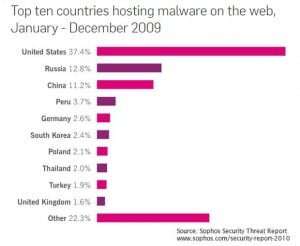 In various malware related ratings, it is among the top ten malware hosting countries: for example, according to Sophos, holding second position worldwide in the rating as of 2010.
In various malware related ratings, it is among the top ten malware hosting countries: for example, according to Sophos, holding second position worldwide in the rating as of 2010.
It is to be noted the above rating only takes into account a number of websites infected as hosted in a specific country. That is not an appropriate criterion, should you try to assess how many developers of malware physically reside in a specific country and how intensively they operate, for, obviously, they can easily create infected websites or infect those existing in any other country. These statistics rather suggest the assumption that it the US that is the main victim of malware, for its infected websites share amounted up to 40% of the worldwide total, and the situation, obviously, remained similar to that in 2013.
It is much harder to track back who makes websites infected than to assess a total of affected websites, but there are hackers who are true to original meaning of this word as they help keep the cyber world free of malware and scam, who have come to Russia to scrutinize its malware market as they believed it was that country that hosted one of the biggest malware nurseries worldwide.
These researches, Fyodor Yarochlin, a native Russian, and a guy who calls himself The Grugq, a US native, have spent more than 1 year in Russia “studying hacking forums”. The self-definition for their study was the Intelligence Gathering Project, so that Fyodor, who knew the language, immersed into the atmosphere of the Russian open access discussion to get to the point of what was going on there. Despite speaking his own language well and understanding virtually all of its deviations and forms, it was not always easy even to Fyodor to accurately explain to The Grugq, a US native, what was up there, so first they encountered plenty of stunts with a sort of “leet” Russian languages that absorbed transliterated in random way and otherwise transformed English words (like “mylo”, literally “soap” in Russian, which means email), criminal jargon and youth slang.
Eventually, they ended up sieving through lots of info, which was rather noise than anything capable of giving them an idea of something really significant, before they focused on top ten domains and purchased access to some genuine hackers’ discussions, which unveiled meaningful figures and trends.
They came across online buyer and seller boards, where people were trying to sell services or products to other guys who wanted to buy specific services or products.
At those boards there were people coming up to say “I need a little bit of traffic for this website so I can do installations.” That is, there were buyers, they wanted to pay for installation you arrange for them. They are also known as traffic buyers. These traffic buyers wanted other guys to send (=sell) traffic to their websites so that they would install their content to the computers behind that traffic. The scheme provided for that every visitor to the buyer’s website that comes from a traffic generated by seller, upon installing a content from buyer’s website, was assessed at the rate of USD 32 for a single installation to seller! 32 bucks at your home with your Mother’s PC!
But let us see what kind of content the hackers pay for stuffing into a target PC at a rate of USD 32 per installation. Typically, this contains an extortion agent, an infection that wants you to pay for various scary and, of course, misleading reasons, e.g. claiming you are running a fake version of Windows. In Russian version, you’ve got to send sms to a specified number in order to unlock your computer; basically, it shuts down your PC until you send them an sms, which is premium rate.
 Another type of cooperation they have discovered at those boards was “partnerka” (original Russian term), “partnership”, which is actually a partnership program. In particular, there is an installation partnership program, which might sound pretty legitimate.
Another type of cooperation they have discovered at those boards was “partnerka” (original Russian term), “partnership”, which is actually a partnership program. In particular, there is an installation partnership program, which might sound pretty legitimate.
In case of partnership, unlike in the event of traffic selling, the payment is associated with content displayed at a website that sells its advertisement services. Through a chain of mediators, it can come so far that NY Times website gets an exploit (a malicious code that exploits vulnerabilities of visiting computer to install malware bypassing user’s authorization) on its pages.
Thus, using these two methods, hackers residing in Russia efficiently distribute their malware into the world’s richest markets. For you to understand the scale, note the top players of such scam get up to USD 100k on a monthly basis, which is 30% of income from the amount of the schemes in which they successfully participate.
Posted in: News
Leave a Comment (0) ↓