Tabufa file virus decryptor and removal tool

Frankly, there are very few ransomware samples out there that create ripples in the security landscape. These are mostly feeble pests that hardly spread in the wild or have terrible implementation of cryptographic algorithms. The new strain called Tabufa, though, stands out from the rest as it is backed by a powerful distribution campaign and boasts uncrackable cipher.
Table of Contents
What is the Tabufa ransomware?
They say everything new is well-forgotten old. While this is an arguable statement, it appears to hold true for the current state of the ransomware industry. How high was the likelihood of a lineage codenamed GlobeImposter, which was mostly active in 2017, reviving in a massive campaign now in 2019? The truth is, this family has made itself felt again in mid-April with the fresh Tabufa variant. Numerous users around the world have been reporting attacks where their valuable files get stained with the .tabufa extension and, predictably enough, become encrypt beyond recovery. This ongoing wave is gaining momentum, and researchers have yet to come up with viable countermeasures. In addition to the above-mentioned file extension, a prominent red flag is the how_to_back_files.html ransom note that suddenly appears on the desktop and inside folders with hostage data.
Tabufa ransomware is reportedly proliferating over a well-orchestrated malicious spam campaign. The unsuspecting users are receiving emails that look enticing enough to open and see what’s inside. The misleading subjects of these messages range from invoices allegedly coming from utility service providers, package delivery notifications – all the way to fake job offers. One way or another, the recipient is duped into opening an attached Office document that tries to play the notorious macros trick and thus download all components of the ransomware from a criminals-run server. As soon as the random-named binary is launched, the Tabufa virus will commence a sneaky scan of the hard disk for dozens of popular file types. It will also scour all connected external drives in order to cover every bit of data that might matter to the victim.
Then, the encryption phase of the attack chain takes root. The ransomware utilizes asymmetric RSA cryptosystem to lock down the files, and unfortunately it does that in a flawless way. In the aftermath of this process, the victim’s personal documents, photos, videos, databases and tons of other files become impossible to open. Furthermore, each one gets appended with the .tabufa string so that a sample object named Graph.xlsx turns into Graph.xlsx.tabufa.
As it has been mentioned, the malicious code also creates a file whose goal is to keep the victim in touch with the criminals. The how_to_back_files.html ransom note, when opened in a browser, provides the felons’ contact emails along while also containing the infected user’s personal ID. The document additionally advises against editing the encrypted files, otherwise the recovery may be unfeasible. An extra tip to decrypt one file for free is supposed to be evidence that the extortion isn’t bluff. To reach out to the attackers, the victim is instructed to send an email with their personal identifier to tabufa@protonmail.com or tabufa@airmail.cc. The offenders will then reply with the ransom demands. The amount of money to be paid for the crooks’ decryptor varies. Some users with several affected hard drives have been told to submit 1.5-1.9 Bitcoin. That’s worth thousands of dollars. Whereas the odds of having to pay a fortune for file recovery is fairly high, there are a few workarounds that might allow you to take a shortcut and restore the skewed data in a different way. See below for details.
Tabufa file automatic removal
Extermination of this ransomware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download Tabufa ransomware remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the file and related infections removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the plague proper. Now you are facing a bigger challenge – try and get your data back.
Methods to restore files encrypted by Tabufa file
Workaround 1: Use file recovery software
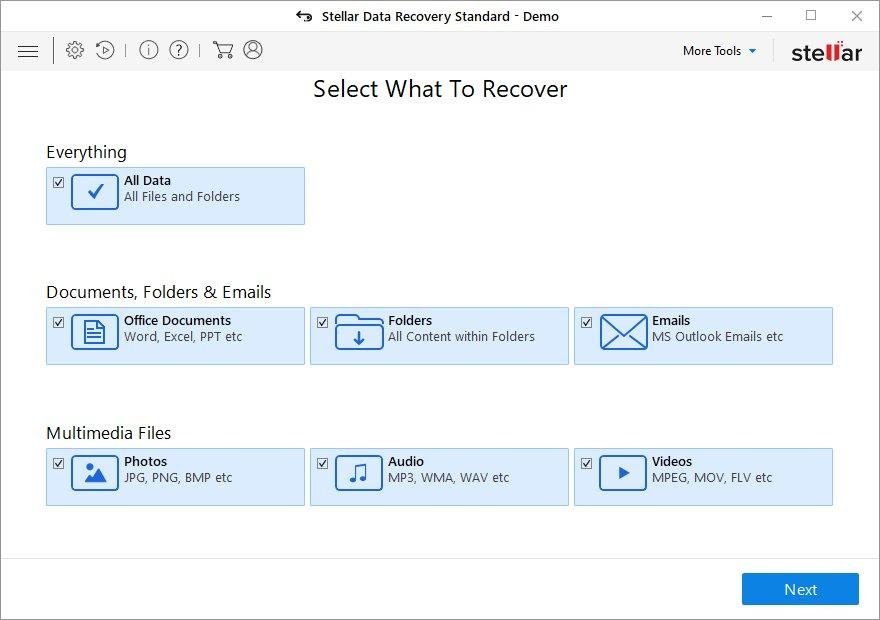
It’s important to know that the Tabufa file creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Stellar Data Recovery for this purpose. The newest version of the file under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Download Stellar Data Recovery Professional
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
-
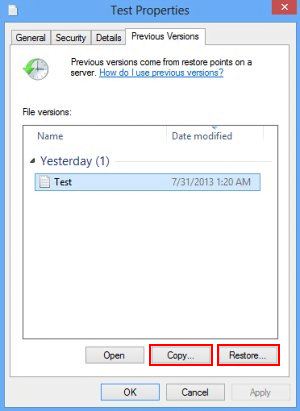
Use the Previous Versions feature
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.

-
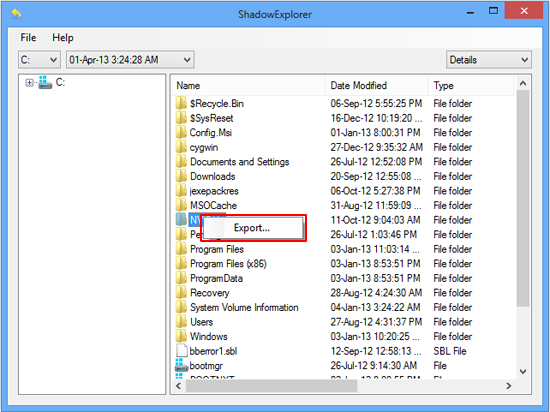
Apply Shadow Explorer tool
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.

Verify whether Tabufa file has been completely removed
Again, ransomware removal alone does not lead to the decryption of your personal files. The data restore methods highlighted above may or may not do the trick, but the file itself does not belong inside your computer. Incidentally, it often comes with other file, which is why it definitely makes sense to repeatedly scan the system with automatic security software in order to make sure no harmful remnants of this file and associated threats are left inside Windows Registry and other locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓