How to remove Trojan.Pidief.X malware

There are perpetrating programs that impair computers directly in various ways. The infection called Trojan.Pidief.X, though, happens to be different. Its objective is to promote other malicious code. Furthermore, its activity involves a great deal of manipulation reminiscent of classic social engineering techniques. The harmful component is camouflaged as a benign PDF file, so users are quite likely to fall for the trickery without suspecting a peril.
Table of Contents
What is the Trojan.Pidief.X virus?
Trojan.Pidief.X denotes a malicious entity heavily used by cybercriminals to distribute certain types of computer infections. Just to be clear from the get-go, it should be emphasized that this malware does not manifest itself under said name; instead, that’s how security suites tend to flag it if detected in a system. The “Pidief” part is there for a good reason – the kernel component of this fraud is a booby-trapped PDF file that appears harmless on the face of it. It may look like a commonplace invoice, job offer or resume, but as soon as an unsuspecting user opens it, an additional object is dropped onto the target PC behind their back. Specifically, the opportunistic infection ends up inside the Temp folder. It is a random-named file with the .docm extension.
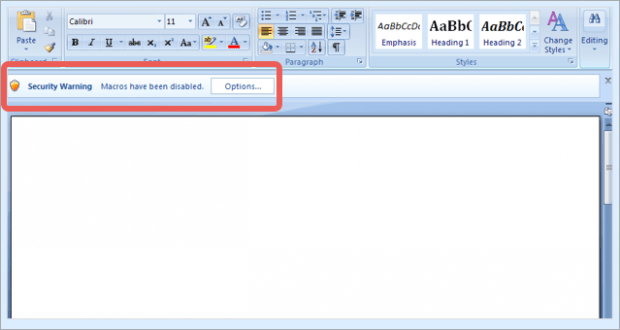
The gist of this whole scheme is to dupe the user into opening the above-mentioned DOCM file. It is a Microsoft Word document with embedded VBA macros. While being originally useful, macros have gained notoriety for allowing remote execution of dangerous code. This is precisely what happens in the Trojan.Pidief.X attack scenario. For an inconspicuous security loophole to appear in the system, it suffices the victim to simply open the trojanized .docm file. Which additional piece of malware infiltrates the machine via this hype is a matter of who operates the campaign. It may range from PUAs (potentially unwanted applications), to info-stealing threats, all the way to ransomware that will encrypt all important data on the PC and demand Bitcoins for decryption.
Contagious PDF files with Trojan.Pidief.X on board tend to be distributed via spam. The large volumes of rogue emails are typically generated by botnets such as Necurs. Again, the attached documents pass themselves off as something potentially luring, so recipients willingly open them out of curiosity. Due to the obfuscated malware dropper’s activity, the associated infection then gains a foothold on the computer. To recap, Trojan.Pidief.X pursues the goal of disseminating harmful code, so it definitely does not belong in a healthy system.
Trojan.Pidief.X malware automatic removal
The extermination of Trojan.Pidief.X trojan can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped out from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download Trojan.Pidief.X remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the malware removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the infection. However, it might be a good idea to consider ascertaining the malware is gone for good.
Posted in: KnowledgeBase
Leave a Comment (0) ↓