Remove Lukitus ransomware and decrypt .lukitus extension files
Although the Locky ransomware family is no longer dominating the online extortion business, it is still in game. A recent proof of its longevity is the emergence of a new variant that adds the .lukitus extension to encrypted files and drops rescue notes named lukitus-[random].htm and lukitus-[random].bmp. This article sheds light on all hallmark signs of this edition of Locky and provides tips to restore encrypted data.
Table of Contents
What is the Lukitus ransomware?
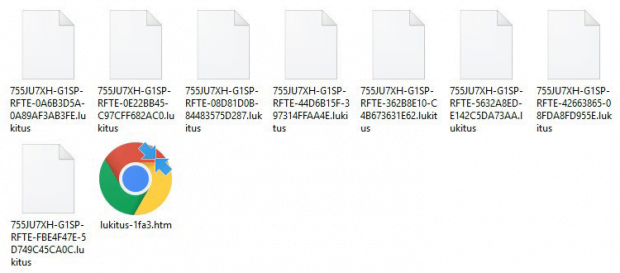
Lukitus is the name of the latest Locky ransomware mod. It was discovered on August 16, 2017, only a week after the previous Diablo6 variant was discovered. This recent activity of Locky developers designates they are back after months of hiatus, and they appear to be just as motivated as before, judging by the quantity of malicious payloads delivered via spam. It’s worth mentioning that the name given to this newest edition by researchers is a misnomer to a certain extent, because it’s actually still Locky that switched to using the .lukitus extension for encrypted files. In addition to crypto proper, the data mutilation workflow also involves the scrambling of filenames. As a result, an arbitrary file gets renamed to a weird-looking entry that consists of 36 random hexadecimal characters followed by the .lukitus suffix at the end (see image below).
Obviously, the victim has no way of knowing which encoded item corresponds to a specific document, image, video, database, etc. This nuance of the Lukitus ransomware impact definitely tangles the prioritization of file recovery, simply because the plagued user is unaware where on the computer the most important stuff is. The worst part of the damage, though, is the data encryption that relies on a combo of RSA-2048 and AES-128 cryptographic algorithms. In the aftermath of this routine, the user is unable to access any valuable files in a regular way. At this point, entities called ransom notes come to the fore. These are documents named lukitus-[4 random chars].htm and lukitus-[4 random chars].bmp. Locky drops the HTM edition into all folders with encrypted files and uses the BMP one to replace the original desktop wallpaper.
Like with earlier versions, the ransom notes say, “All of your files are encrypted with RSA-2048 and AES-128 ciphers.” In a nutshell, the rest of their contents instruct the user to install Tor Browser, enter a specified URL in the address bar and follow directions on the site. The destination resource is named the Locky Decryptor Page. It upsells the data decryption tool for about 0.5 Bitcoin, which is worth some $2,100. That’s the gist of the average ransomware predicament: a user is coerced into paying for what should belong to them in the first place – an unjust turn of events, but that’s how the online extortion ecosystem works.
The Lukitus iteration of Locky is still deposited on computers via spam. The booby-trapped emails mostly feature an invoice, fax or voice message theme, just to persuade the recipient to open up the attached ZIP or RAR archive. An obfuscated JS file lurks inside the archive and, when executed, downloads the Lukitus virus binary onto the machine. The infection then scans the hard drive, network drives and removable media for numerous types of data that are likely to be personal hence important. The rest of the impact has already been described above. To avoid Locky ransomware variants, steer clear of fishy-looking emails and refrain from opening files attached to them. Below are some tips that should come in handy as far as Lukitus removal and data recovery is concerned.
Lukitus extension automatic removal
Extermination of this ransomware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download Lukitus ransomware remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the extension and related infections removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the plague proper. Now you are facing a bigger challenge – try and get your data back.
Methods to restore files encrypted by Lukitus extension
Workaround 1: Use file recovery software
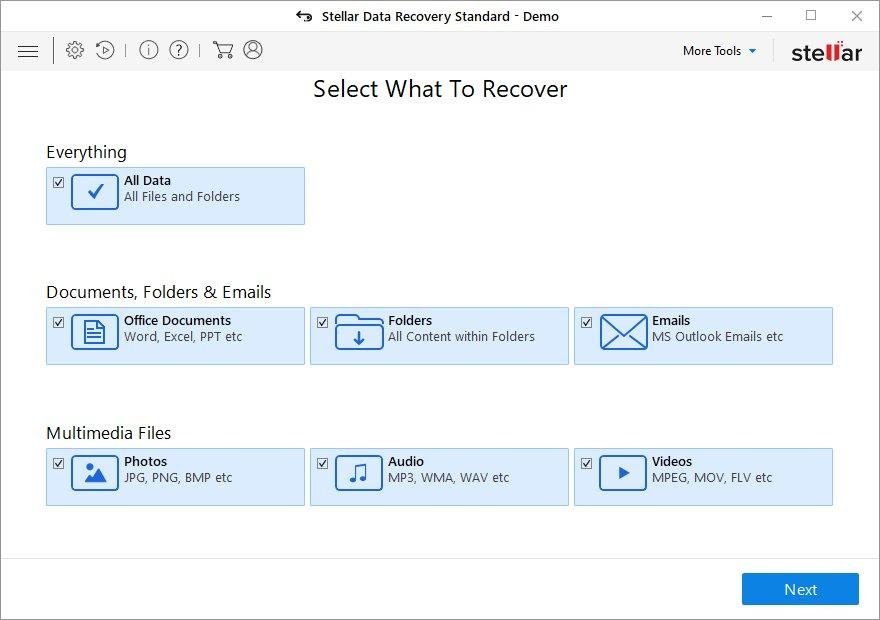
It’s important to know that the Lukitus extension creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Stellar Data Recovery for this purpose. The newest version of the extension under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Download Stellar Data Recovery Professional
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
-
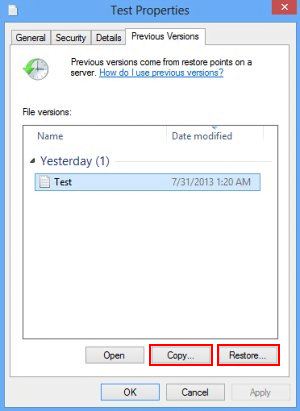
Use the Previous Versions feature
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.

-
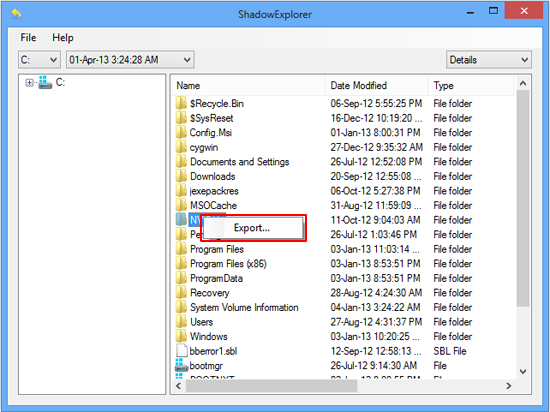
Apply Shadow Explorer tool
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.

Verify whether Lukitus extension has been completely removed
Again, ransomware removal alone does not lead to the decryption of your personal files. The data restore methods highlighted above may or may not do the trick, but the extension itself does not belong inside your computer. Incidentally, it often comes with other extension, which is why it definitely makes sense to repeatedly scan the system with automatic security software in order to make sure no harmful remnants of this extension and associated threats are left inside Windows Registry and other locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓
![Contents of lukitus-[random].htm/bmp ransom notes Contents of lukitus-[random].htm/bmp ransom notes](https://soft2secure.com/wp-content/uploads/contents-of-lukitus-ransom-note-620x350.png)