Decrypt Cryptowall 4.0: remove HELP_YOUR_FILES.png virus

The space occupied by file encrypting malware in the global computer threat pie chart has gotten big enough for security industry to build ad hoc features into their latest product lines. This, unfortunately, is merely a prevention measure rather than an effective way of approaching the matter after the fact. In the meanwhile, pests like the Cryptowall 4.0 keep putting their victims in a flummoxing circumstance of making the choice to pay or not to pay.
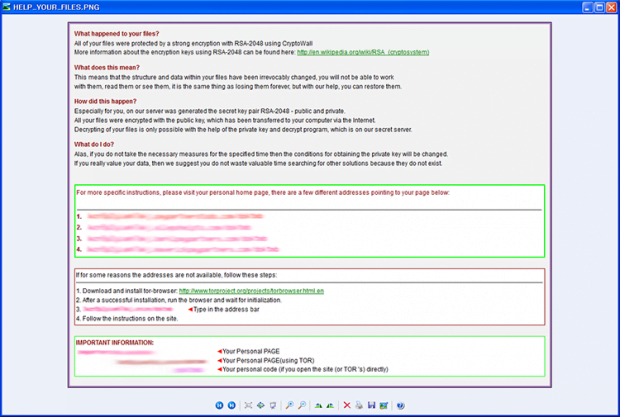
Dealing with the aftermath of a ransomware attack is certainly the hardest virus remediation task imaginable. As useful as it was originally intended to be, cryptography can become a devastating cyber weapon when in the wrong hands. The trojan called CryptoWall, in particular its 4.0 variant, employs one of the strongest encryption standards known as RSA-2048, pointing it against the infected user’s files. A file named HELP_YOUR_FILES.png, possibly also a HTML and TXT counterparts, is the byproduct of this compromise – it pops up within seconds after every Windows boot-up. The message in it includes information such as what happened to the victim’s personal files and what to do. In particular, the user is provided with several Tor gateway links to their “personal home page”, where they can send the scammers a ransom payment and get the private decrypt key in return.
There is no single distribution channel used by the cybercrime actors running the CryptoWall campaign. Some instances of the ransomware dropping routine rely on exploit kits. This is the worst-case scenario because hardly any countermeasures can be applied – the unsuspecting user visits a hacked site or malicious page hosting the malicious service, and the kit can then detect software vulnerabilities on the target box to execute the code on the quiet. An alternative entry point is through social engineering, where the would-be prey receives a deceptive email disguised as a legal notice, delivery report, etc. Once the email attachment is clicked and opened, the attack commences and goes all the way behind the scenes.
Cryptowall 4.0 scans the PC’s storage device for files with predefined formats. These are MS Word, Excel and PowerPoint documents, JPG, PNG and BMP images, PDF files and movies. As soon as the process of encrypting of these objects has been completed, the virus displays directions in the corresponding document. The ransomware lists The Onion Router URLs for the person to navigate to the Command and Control server and proceed with the payment steps. This means that Tor Browser must be installed and used for further interaction. Anonymity of the hoax is also secured by the recommended payment in Bitcoins. The ransom amounts to approximately 1.83 BTC, or 700 USD. By the way, a recent report by the Cyber Threat Intelligence states that the estimated income earned by CryptoWall publishers exceeds the astonishing 300 million USD – that shows how successful this plague is, regretfully enough.
The private decryption key required for decoding one’s personal files can only be received if the ransom is sent to the bad guys. Otherwise, the victim has a few options to try and rescue their data. These techniques, which are provided below, are no panacea and they don’t ensure full recovery of the hijacked information, but following them is a fair alternative to the extortion imposed by the malefactors.
Table of Contents
Cryptowall 4.0 ransomware automatic removal
Extermination of this ransomware can be efficiently accomplished with reliable security software. Sticking to the automatic cleanup technique ensures that all components of the infection get thoroughly wiped from your system.
1. Download recommended security utility and get your PC checked for malicious objects by selecting the Start Computer Scan option
Download Cryptowall 4.0 ransomware remover
2. The scan will come up with a list of detected items. Click Fix Threats to get the ransomware and related infections removed from your system. Completing this phase of the cleanup process is most likely to lead to complete eradication of the plague proper. Now you are facing a bigger challenge – try and get your data back.
Methods to restore files encrypted by Cryptowall 4.0 ransomware
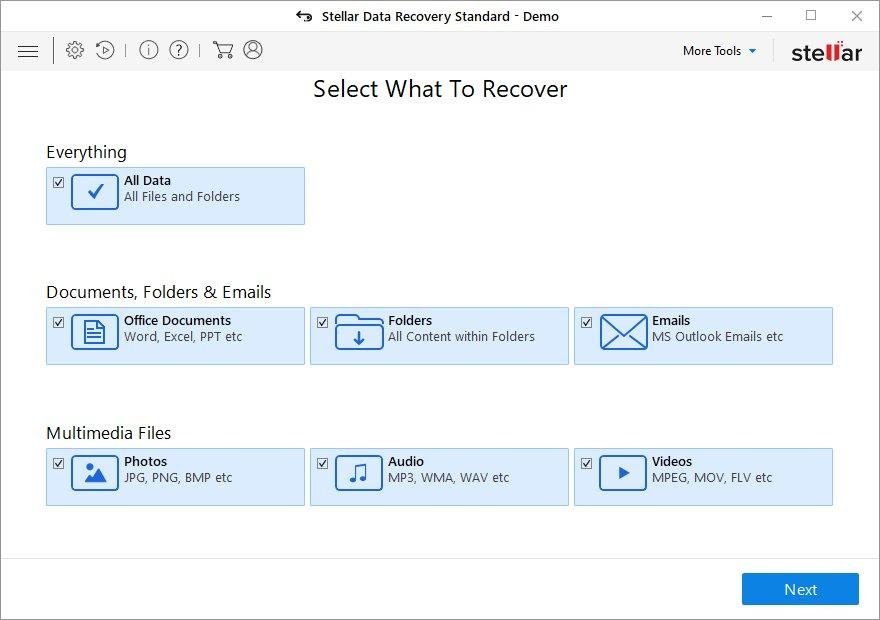
Workaround 1: Use file recovery software
It’s important to know that the Cryptowall 4.0 ransomware creates copies of your files and encrypts them. In the meanwhile, the original files get deleted. There are applications out there that can restore the removed data. You can utilize tools like Stellar Data Recovery for this purpose. The newest version of the ransomware under consideration tends to apply secure deletion with several overwrites, but in any case this method is worth a try.
Download Stellar Data Recovery Professional
Workaround 2: Make use of backups
First and foremost, this is a great way of recovering your files. It’s only applicable, though, if you have been backing up the information stored on your machine. If so, do not fail to benefit from your forethought.
Workaround 3: Use Shadow Volume Copies
In case you didn’t know, the operating system creates so-called Shadow Volume Copies of every file as long as System Restore is activated on the computer. As restore points are created at specified intervals, snapshots of files as they appear at that moment are generated as well. Be advised this method does not ensure the recovery of the latest versions of your files. It’s certainly worth a shot though. This workflow is doable in two ways: manually and through the use of an automatic solution. Let’s first take a look at the manual process.
-
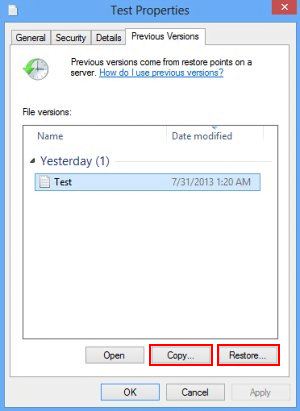
Use the Previous Versions feature
The Windows OS provides a built-in option of recovering previous versions of files. It can also be applied to folders. Just right-click on a file or folder, select Properties and hit the tab named Previous Versions. Within the versions area, you will see the list of backed up copies of the file / folder, with the respective time and date indication. Select the latest entry and click Copy if you wish to restore the object to a new location that you can specify. If you click the Restore button, the item will be restored to its original location.

-
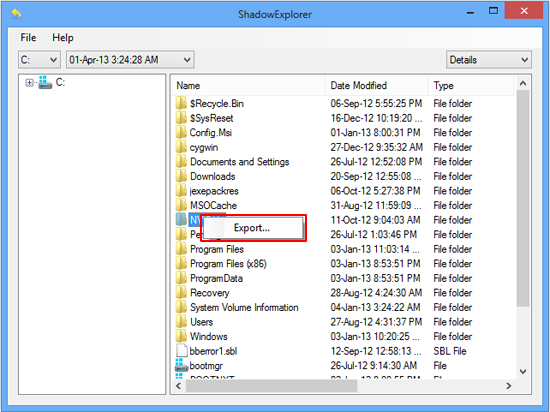
Apply Shadow Explorer tool
This workflow allows restoring previous versions of files and folders in an automatic mode rather than by hand. To do this, download and install the Shadow Explorer application. After you run it, select the drive name and the date that the file versions were created. Right-click on the folder or file of interest and select the Export option. Then simply specify the location to which the data should be restored.

Verify whether Cryptowall 4.0 ransomware has been completely removed
Again, ransomware removal alone does not lead to the decryption of your personal files. The data restore methods highlighted above may or may not do the trick, but the ransomware itself does not belong inside your computer. Incidentally, it often comes with other ransomware, which is why it definitely makes sense to repeatedly scan the system with automatic security software in order to make sure no harmful remnants of this ransomware and associated threats are left inside Windows Registry and other locations.
Posted in: KnowledgeBase
Leave a Comment (0) ↓