How to remove Memz trojan virus from Windows
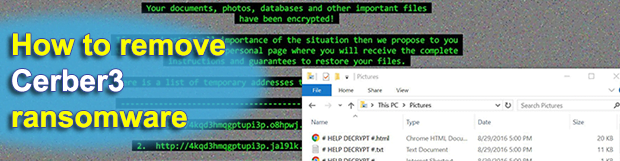
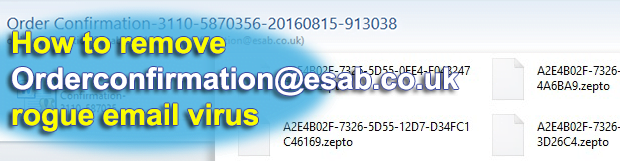
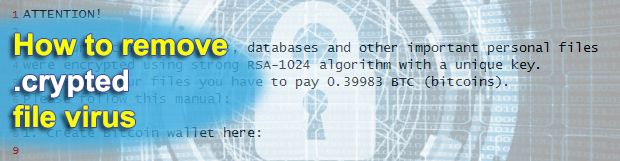
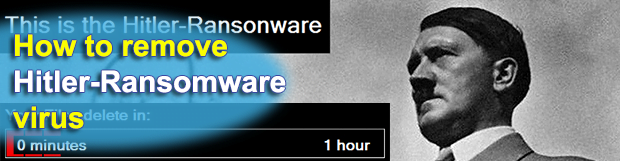
Most computer viruses are written for specific malevolent objectives, typically ones related to financial gain in one way or another. Infections like the Memz trojan, however, go beyond this mercantile paradigm. The above-mentioned app appears to be built for wreaking havoc with any Windows machine it ends up on, period. It calls forth multiple glitches […]
Read more →Posted in: KnowledgeBase
Leave a Comment (0) →